Start verification method and system
A verification method and technology for verifying information, applied in the fields of digital data authentication, instruments, electrical digital data processing, etc., can solve the problems of low security and easy cracking of the verification method, achieve high security and overcome the effect of easy cracking
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
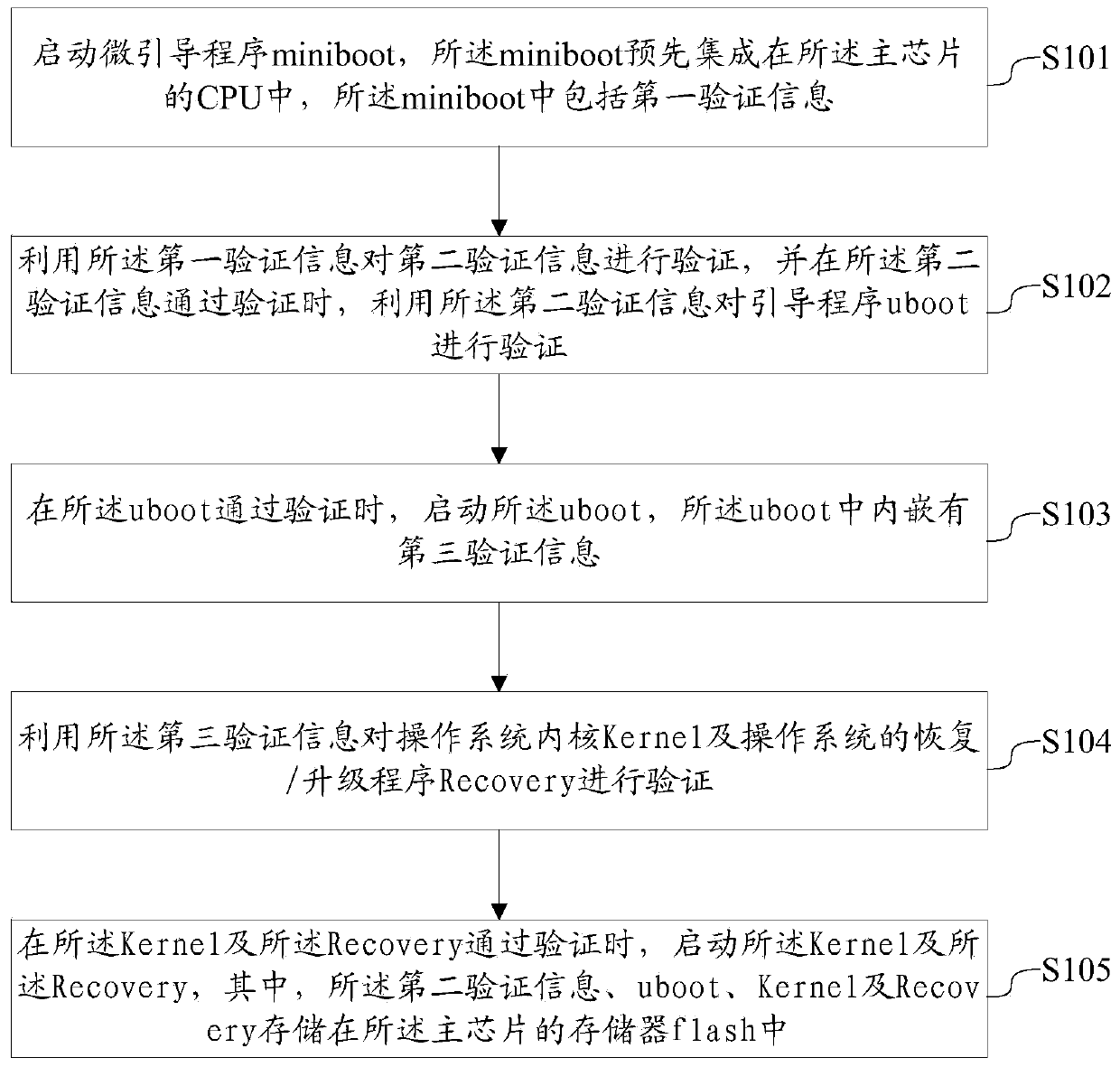
[0055] Embodiment 1 discloses a startup verification method, which can be applied to electronic devices such as smart terminals, where the electronic device includes a main chip.
[0056] refer to figure 1 , the method may include the following steps:
[0057] S101: Start a micro-boot program miniboot, the miniboot is pre-integrated in a CPU (Central Processing Unit, central processing unit) of the main chip, and the miniboot includes first verification information.
[0058] S102: Use the first verification information to verify the second verification information, and use the second verification information to verify the boot program uboot when the second verification information passes the verification.
[0059] Wherein, this step S102 includes:
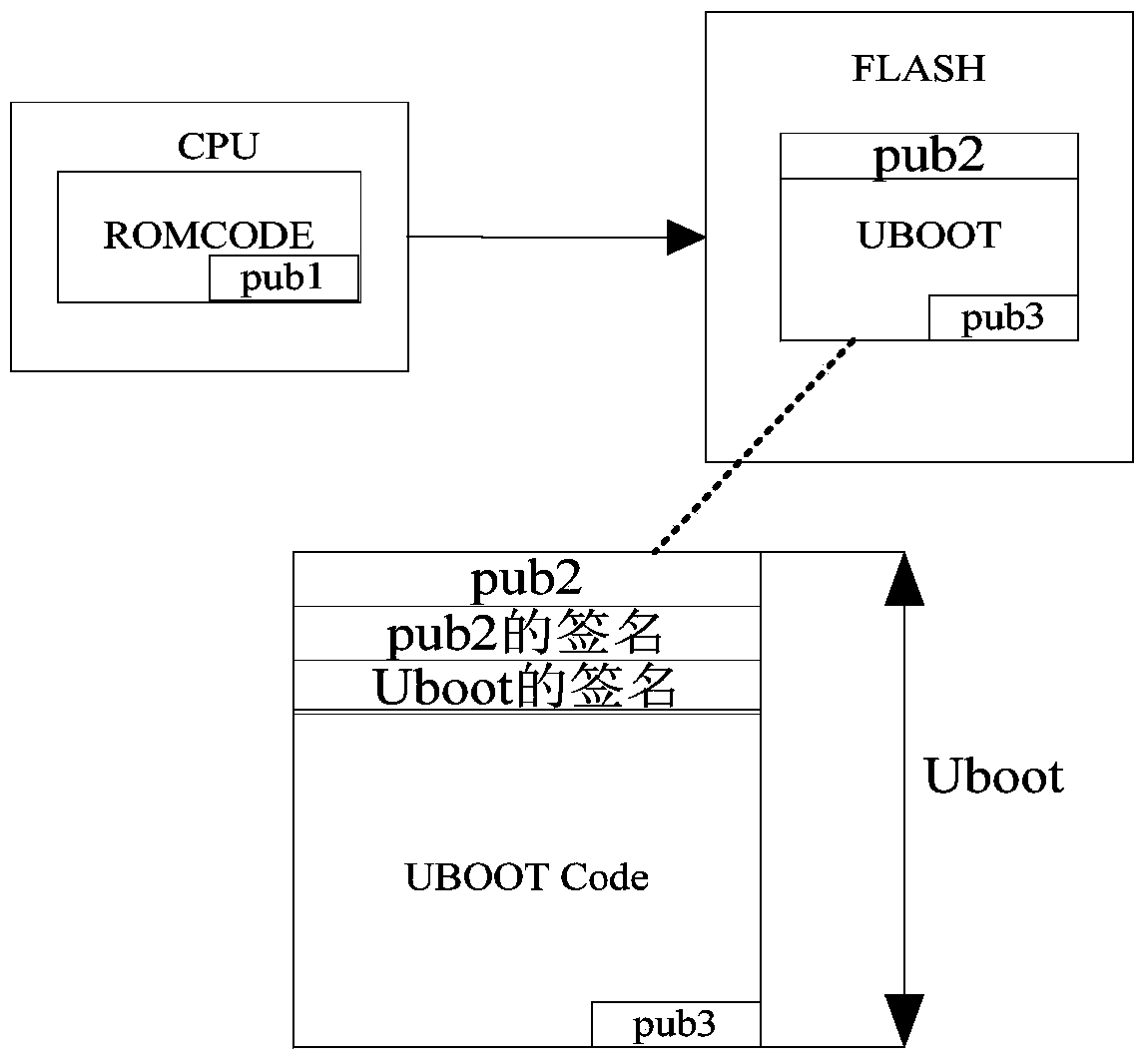
[0060] Based on the first signature data generated by signing the second public key with the first private key in advance, using the first public key to verify the second public key;
[0061] When the second public key passes th...
Embodiment 2
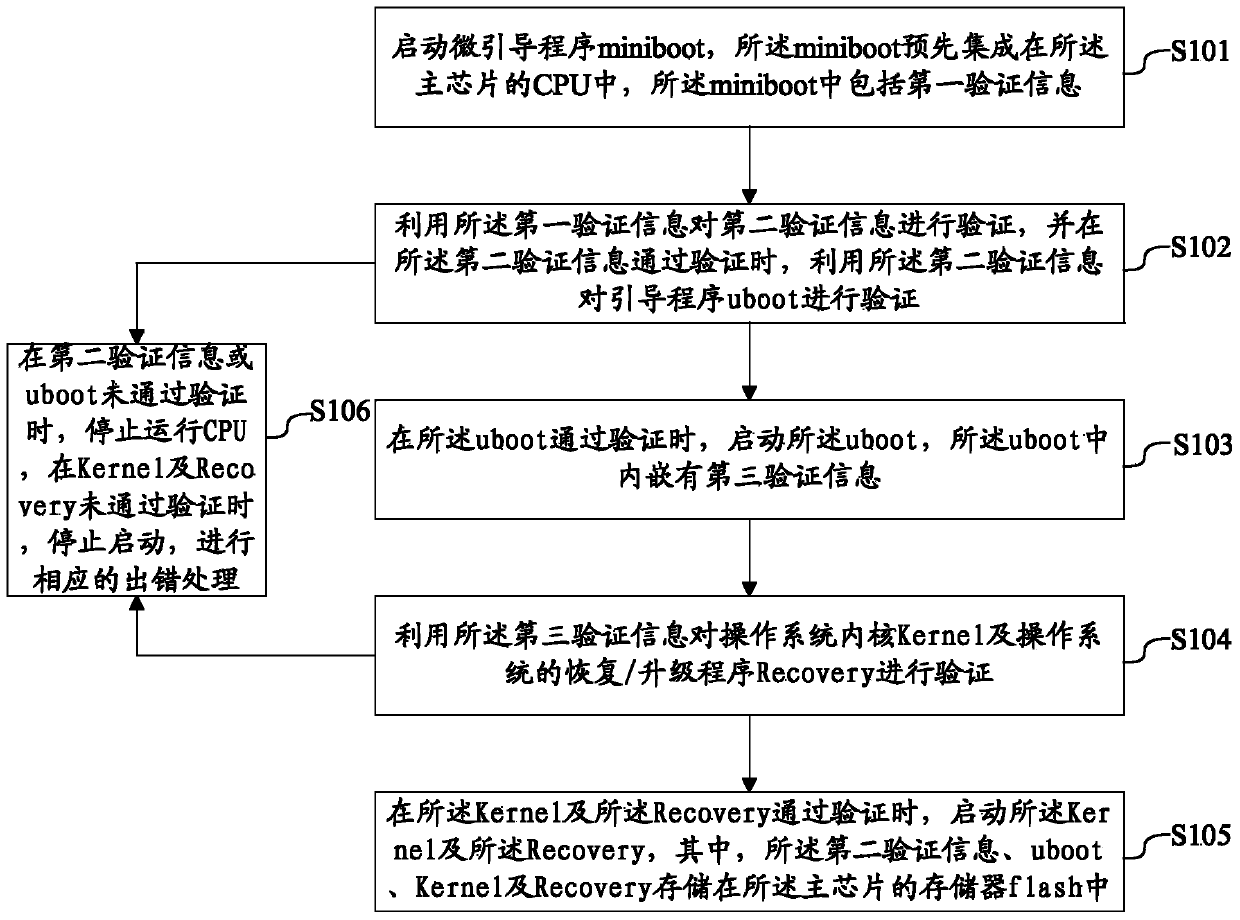
[0079] In this example, refer to image 3 , the above method also includes the following steps:
[0080] S106: When the second verification information or the uboot fails the verification, stop running the CPU, and when the Kernel and the Recovery fail the verification, stop starting and perform corresponding error handling.
[0081] That is to say, when the present invention is applied, when the verification of any one of the various verification steps fails, the main chip cannot be started normally.
[0082] For example, after the original codes of uboot, kernel, or recovery stored in the flash of the main chip are copied for illegal purposes, the copied uboot, kernel, or recovery cannot be copied because the miniboot with the root key embedded in the CPU of the main chip cannot be copied. etc. The original code cannot be activated normally due to the inability to start the verification process.
[0083] After the corresponding original code in the flash of the main chip i...
Embodiment 3
[0097] Embodiment 3 discloses a startup verification system, which corresponds to the startup verification methods disclosed in Embodiment 1 and Embodiment 2.
[0098] First, corresponding to Embodiment 1, refer to Figure 5 , the system includes a first startup module 100 , a first verification module 200 , a second startup module 300 , a second verification module 400 and a third startup module 500 .
[0099] The first startup module 100 is used to start the micro-boot program miniboot, the miniboot is pre-integrated in the central processing unit CPU of the main chip, and the miniboot includes the first verification information;
[0100] The first verification module 200 is configured to use the first verification information to verify the second verification information, and use the second verification information to verify the boot program uboot when the second verification information passes the verification.
[0101] Wherein, the first verification module 200 includes ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com