A method and system for privacy protection
A technology of privacy protection and mode, applied in the field of privacy protection, can solve problems such as user privacy is easy to leak, display terminal does not have privacy protection function, etc., to achieve the effect of solving privacy easy to leak
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
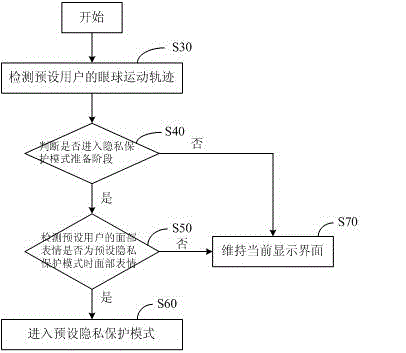
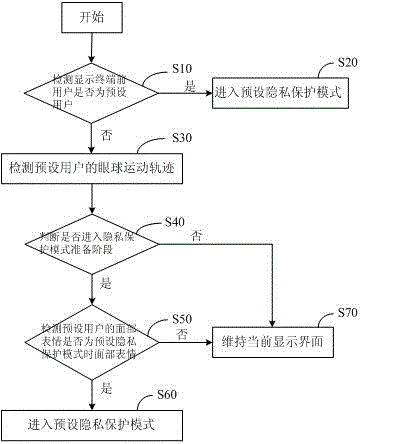
[0054] figure 2 It shows the implementation process of the privacy protection method provided by the first embodiment of the present invention applied to the display terminal. For the convenience of description, only the parts related to the embodiment of the present invention are listed, and the details are as follows:
[0055] As a preferred embodiment of the present invention, the following steps are included before step S30:
[0056] Step S10, detecting whether the user in front of the display terminal is a preset user;
[0057] If yes, execute step S30, and if no, execute step S20.
[0058] Step S20, enter the preset privacy protection mode.
[0059] In the embodiment of the present invention, it is mainly to detect whether the display terminal is a preset user, if not, directly enter the privacy protection mode, and if it is a preset user, further detect the preset eyeball trajectory and facial expression judge.
[0060] It should be noted that the above-mentioned m...
Embodiment 2
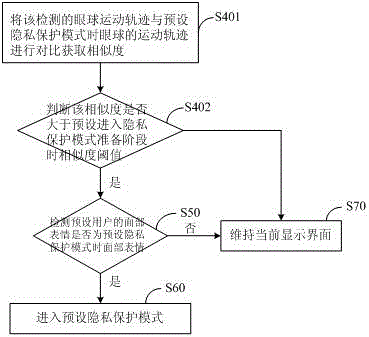
[0062] image 3It shows the implementation process of the privacy protection method provided by the second embodiment of the present invention applied to the display terminal. For the convenience of description, only the parts related to the embodiment of the present invention are listed, and the details are as follows:
[0063] As a preferred embodiment of the present invention, step S40 includes the following steps:
[0064] Step S401, comparing the detected eyeball trajectory with the eyeball trajectory in the preset privacy protection mode to obtain similarity;
[0065] Step S402 judges whether the similarity is greater than the preset similarity threshold when entering the privacy protection mode preparation stage;
[0066] If yes, it means entering the preparation stage of the privacy protection mode, and performing step S50;
[0067] If not, execute step S70.
[0068] In the embodiment of the present invention, when the contrast between the detected eye movement traj...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com