Stand-in authorization method and electronic equipment
A technology of electronic equipment and authorization credentials, applied in the electronic field, can solve problems such as time-consuming and complicated input steps, and achieve the effect of reducing login steps and saving login time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0056] In Embodiment 1, a method of authorization is provided, which is applied to a first electronic device, the first electronic device is connected to the authorized application terminal through the Internet, and the first electronic device is connected to the second electronic device through a local area network , in practical applications, the first electronic device may be an electronic device such as a smart phone, a tablet computer, a notebook, and a television set, and the second electronic device may also be an electronic device such as a smart phone, a tablet computer, a notebook, a television set, etc. , which will not be listed one by one in this embodiment.
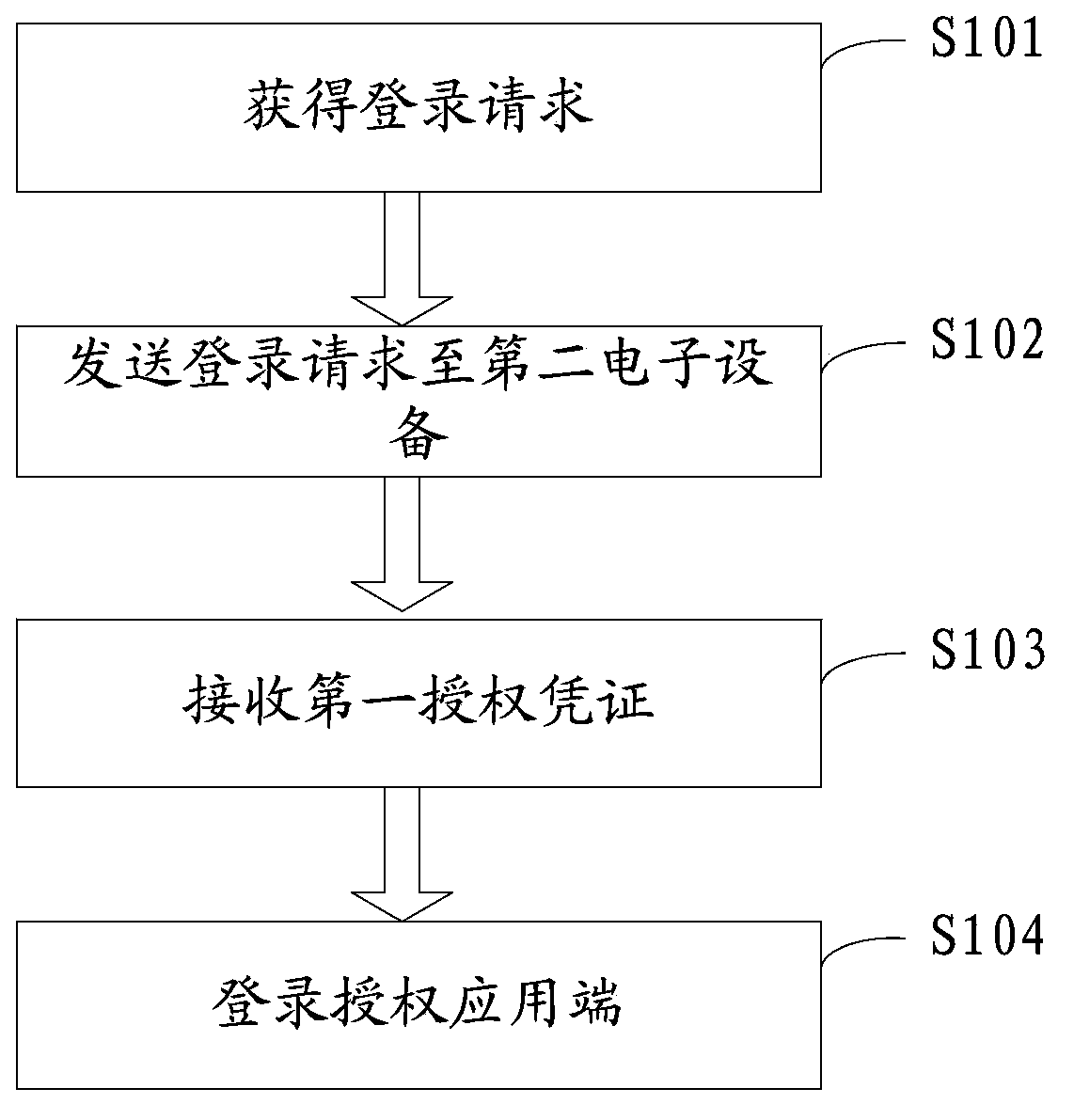
[0057] Please refer to figure 1 , figure 1 It is a flow chart of the method of authorization in Embodiment 1 of the present application, and the method includes the following steps:
[0058] Step S101, obtaining a login request for logging into the authorized application;
[0059] Step S102, sending the l...
Embodiment 2
[0085] In the second embodiment, a method of authorization is provided, which is applied to the second electronic device, the second electronic device is connected to the first electronic device in the first embodiment through a local area network, and the second electronic device is connected to the authorized The application end is connected through the Internet. In practical applications, the first electronic device can be a smart phone, a tablet computer, a notebook, a television, etc., and the second electronic device can also be a smart phone, a tablet computer, a notebook, Electronic devices such as televisions are not listed one by one in this embodiment.
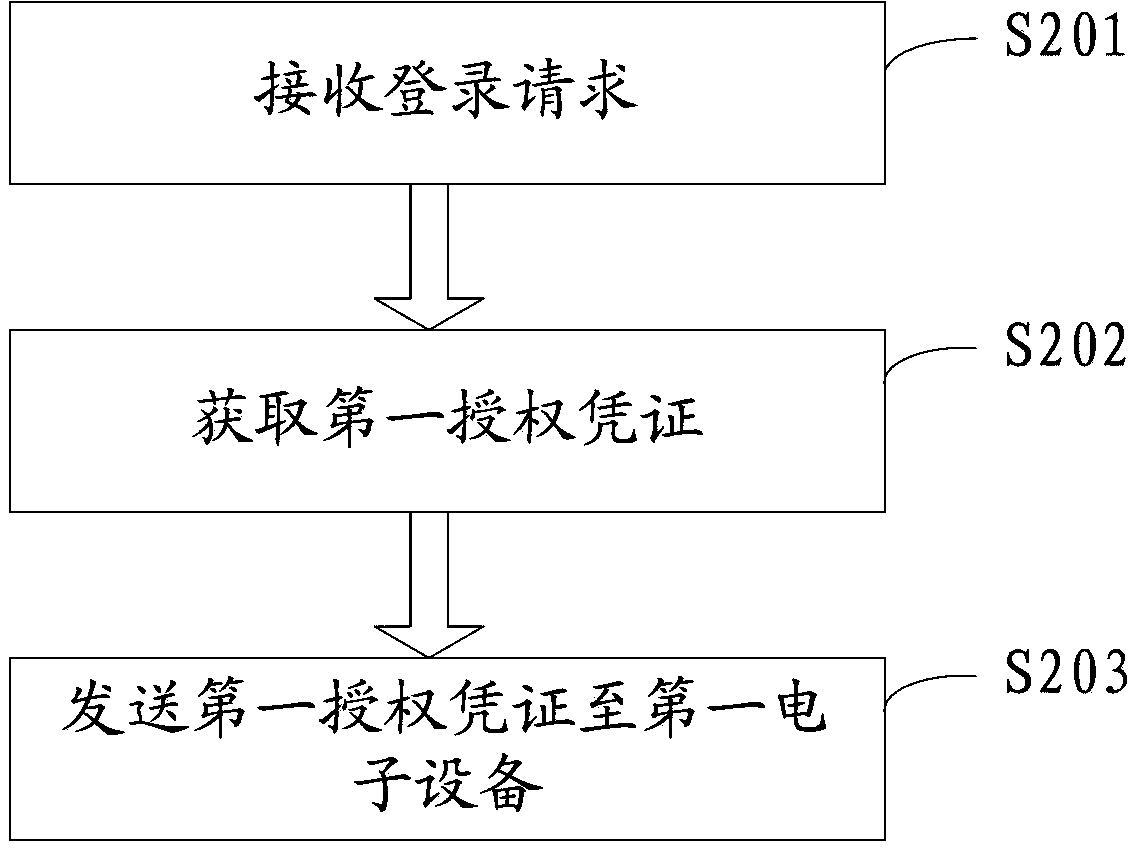
[0086] Please refer to figure 2 , figure 2 It is a flow chart of the method of authorization in Embodiment 2 of the present application, and the method includes the following steps:
[0087] Step S201, receiving a login request sent by the first electronic device for logging into the authorized application;
[00...
Embodiment 3
[0107] Embodiment 3 is an electronic device corresponding to the authorization method in Embodiment 1, specifically the first electronic device, the first electronic device is connected to the authorized application terminal through the Internet, and the first electronic device and the second electronic device Connected through a local area network, in practical applications, the first electronic device can be electronic devices such as smart phones, tablet computers, notebooks, and televisions, and the second electronic device can also be smart phones, tablet computers, notebooks, and televisions. and other electronic devices are not listed one by one in this embodiment.
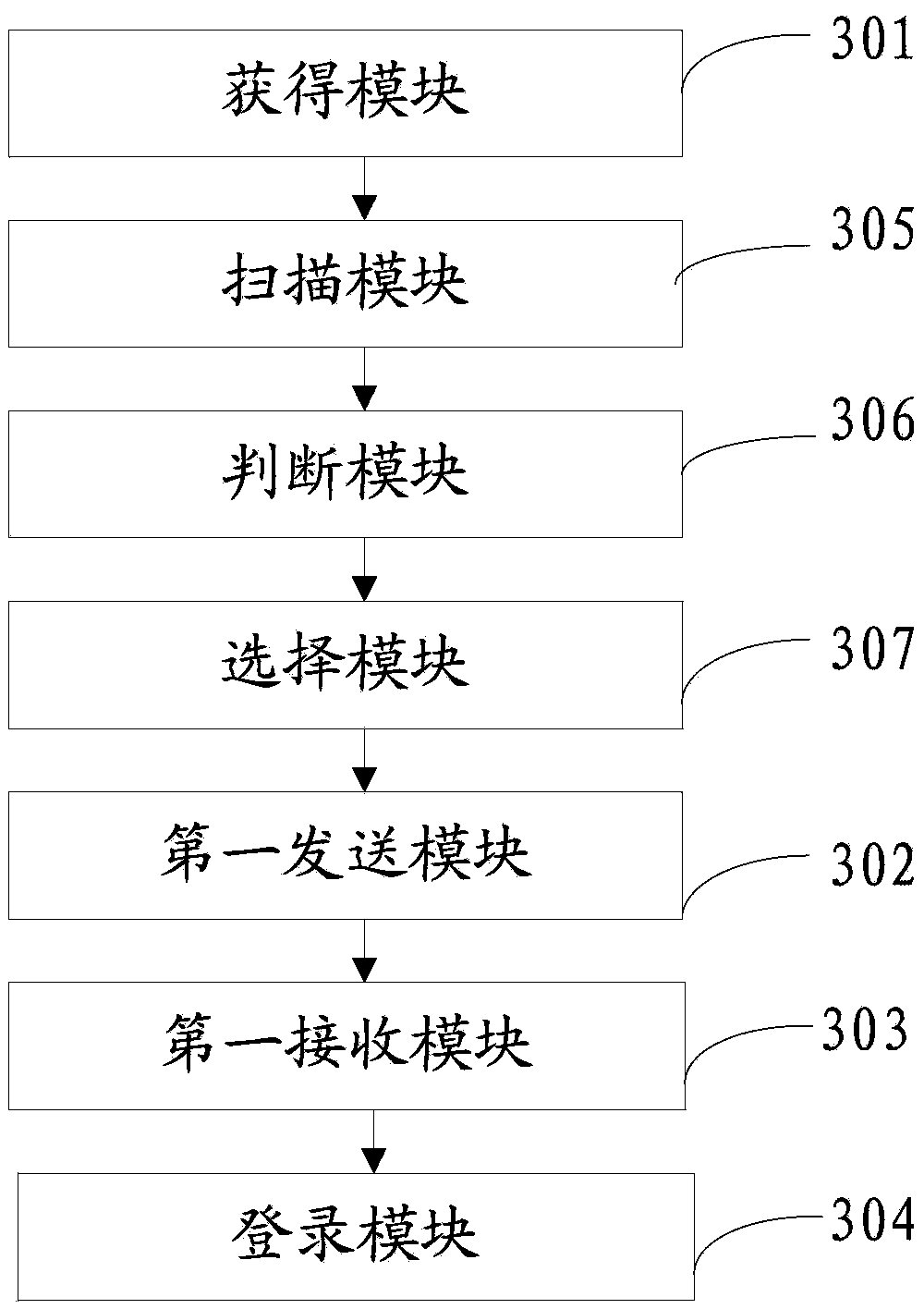
[0108] Please refer to image 3 , image 3 It is a schematic structural diagram of the electronic device in Embodiment 3 of the present application, and the electronic device includes:
[0109] Obtaining module 301, configured to obtain a login request for logging into the authorized application end;
[...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com