Method and system for installing application program between multiple systems and terminal
A technology of application programs and installation methods, which is applied in the field of multi-system control, can solve problems such as data information tampering, operating system crashes, difficulties, etc., and achieve the effect of avoiding theft and leakage of safe data, realizing intelligent installation, and data security and smoothness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
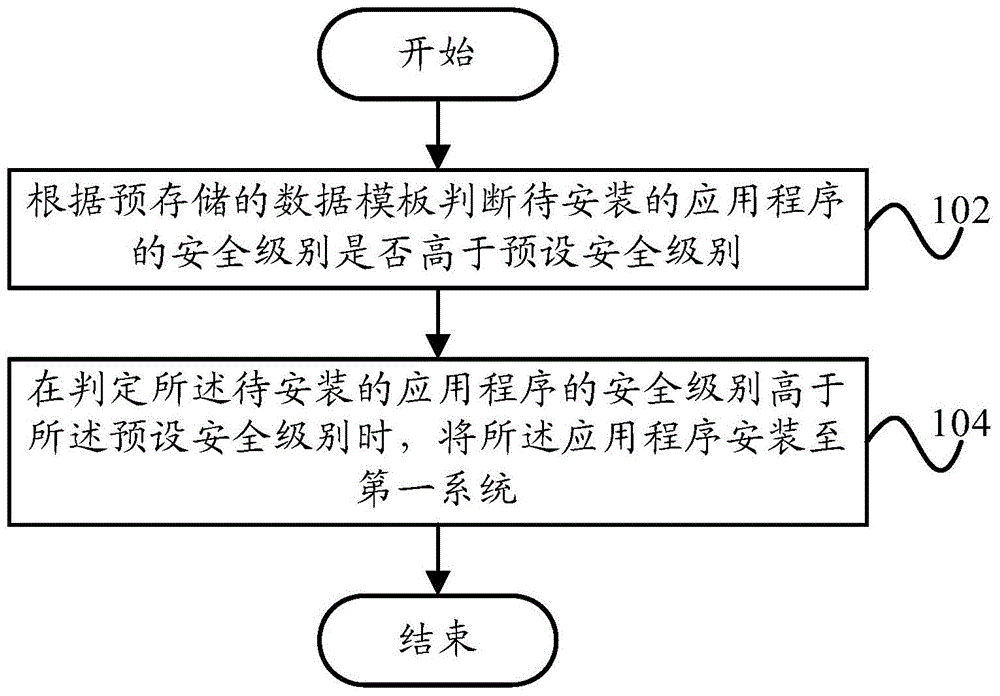
[0053] like figure 1 As shown, the method for installing an application between multiple systems according to an embodiment of the present invention includes: step 102, judging whether the security level of the application to be installed is higher than the preset security level according to the pre-stored data template; step 104 , when it is determined that the security level of the application to be installed is higher than the preset security level, installing the application into the first system.
[0054] In this technical solution, when the security level of the application program to be installed is judged to be higher than the preset security level according to the pre-stored data template, the above-mentioned application program is installed in the first system, realizing the intelligent installation of the application program, effectively avoiding It prevents non-secure applications from stealing and leaking user's security data, and ensures the security of user's in...
Embodiment 2
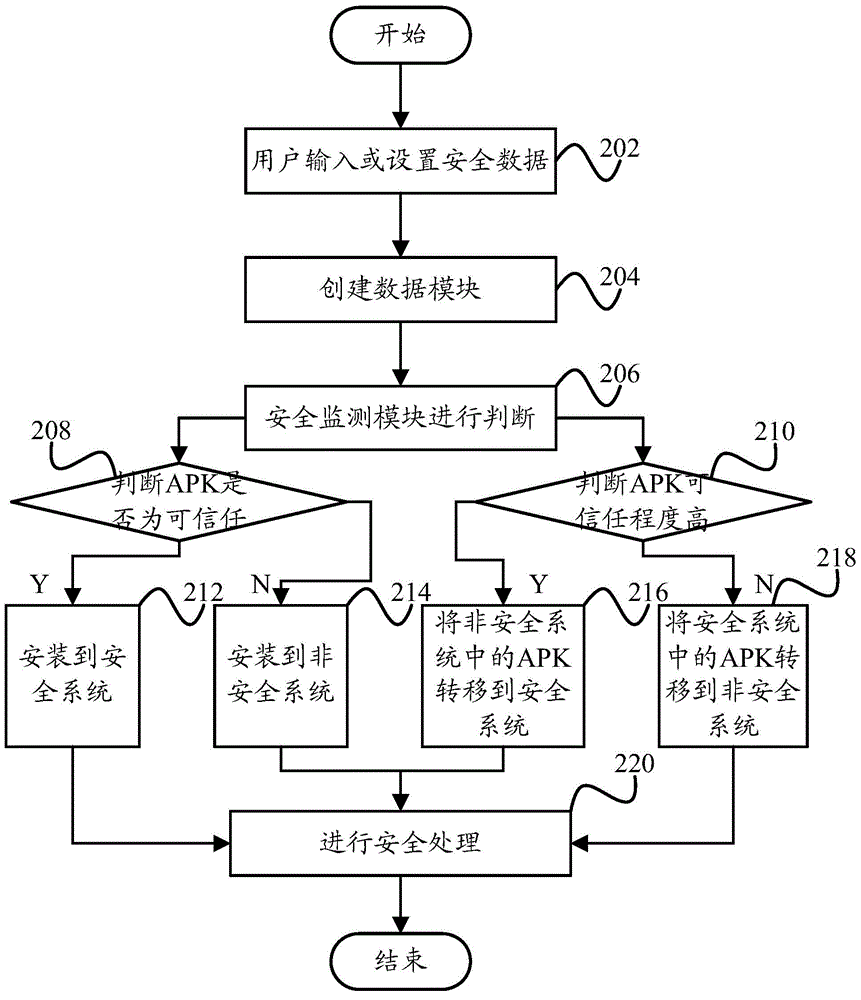
[0072] like figure 2 As shown, the method for installing application programs among multiple systems according to an embodiment of the present invention includes: Step 202, the user inputs or sets security data; Step 204, creates a data module; Step 206, the security monitoring module judges; Step 208 , judge whether the APK (Android Package, installation package) is trustworthy, if so, then execute step 212, if not, then execute step 214; Step 218; Step 212, install to the secure system; install to the non-secure system; transfer the APK in the non-secure system to the secure system; transfer the APK in the secure system to the non-secure system; Step 220, perform security processing.
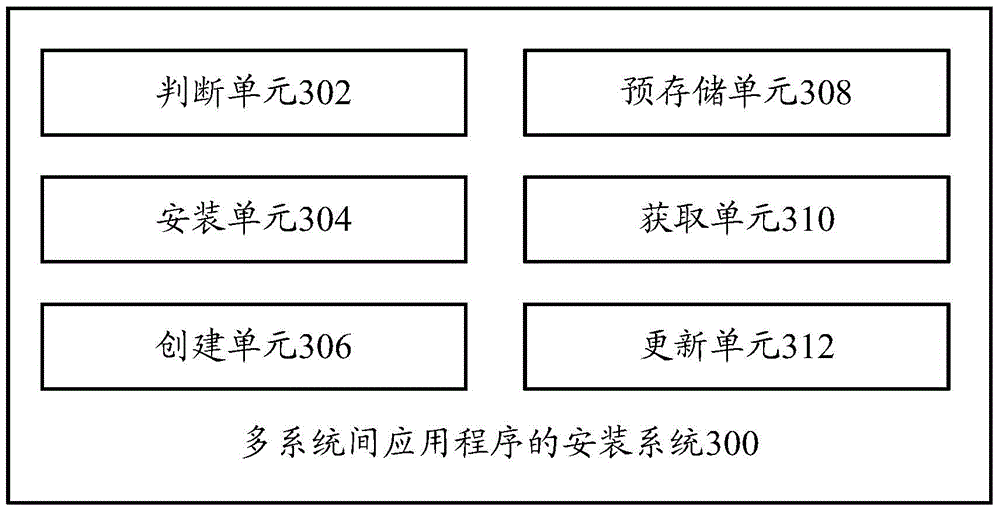
[0073] like image 3 and Figure 4 As shown, the system for installing application programs among multiple systems according to an embodiment of the present invention includes multiple implementation manners.
[0074] Embodiment one:
[0075] like image 3 As shown, the system 300 for in...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com