Method and device for detecting malicious network behaviors
A behavioral and network technology, applied in the field of network security, can solve problems such as insufficient accuracy and false detection, and achieve the effect of improving accuracy and reducing interference
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
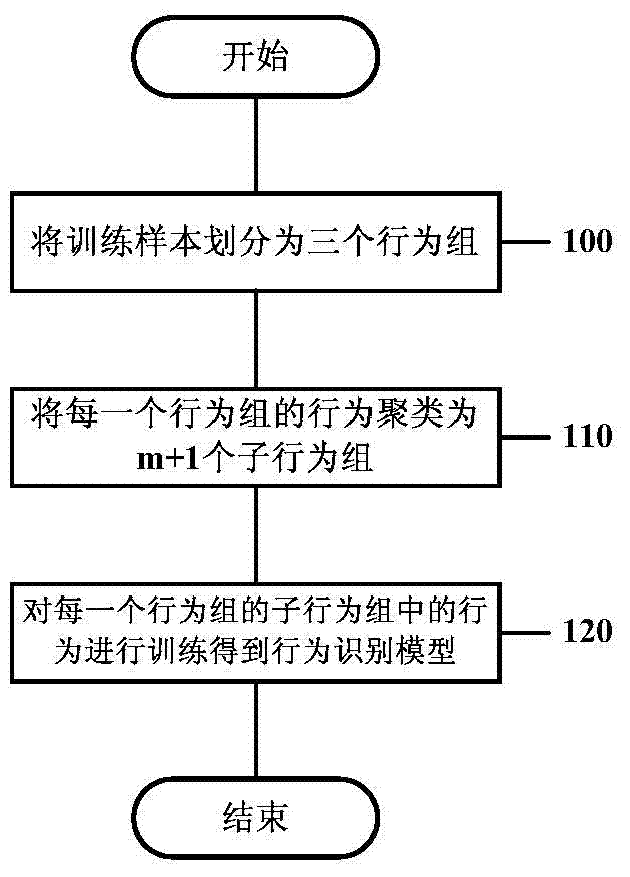
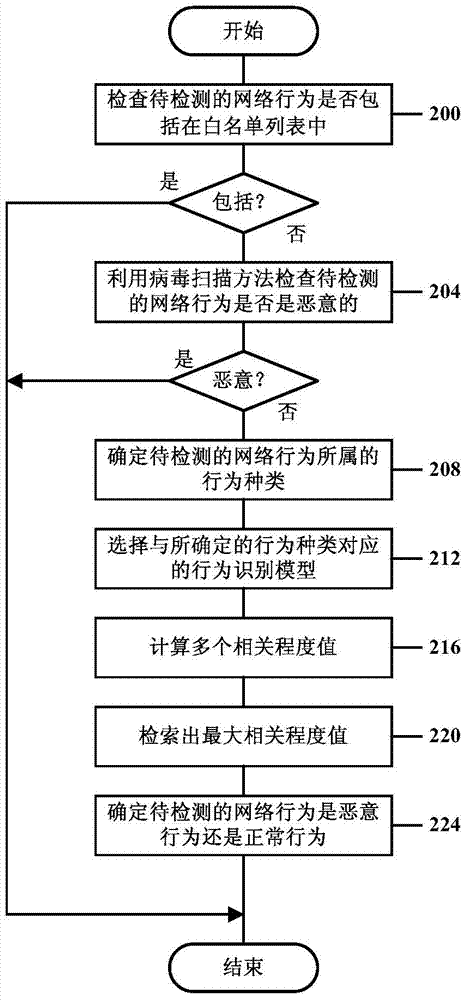
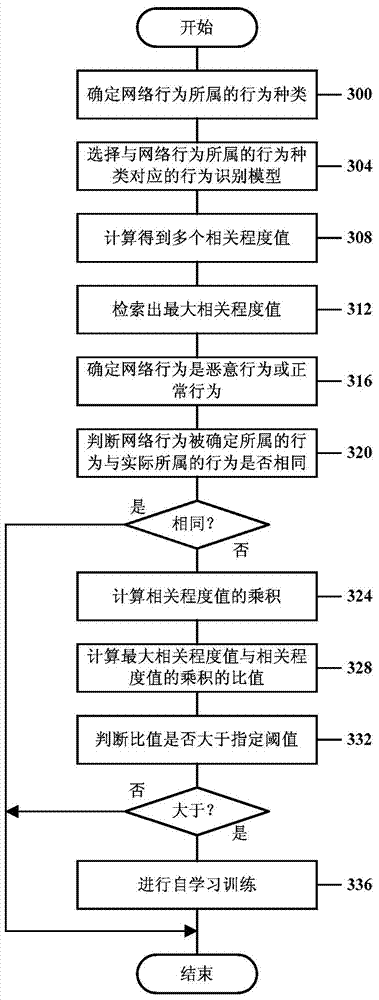
[0023] In the following, various embodiments of the present invention will be described in detail with reference to the accompanying drawings.
[0024] In an embodiment of the present invention, the data tuple X={x 1 ,x 2 ,...,x k} (k is an integer) to characterize network behavior, where x 1 ,x 2 ,...,x k Different characteristic attributes used to describe the network behavior, which can be obtained based on groups related to the network behavior. For example, x 1 ,x 2 ,...,x k It can be the key fields in the TCP / IP header and application layer protocol header of packets related to network behavior, the statistical information (for example, frequency) of packets related to network behavior, and the main body of packets related to network behavior keywords, etc. Packets related to network behavior can be sent from mobile terminals, gateway devices in the mobile Internet (for example, Gateway GPRS Support Nodes (GGSN) or Serving GPRS Support Nodes (SGSN) in General Pa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com