Method and system for preventing computer system time from being tampered
A technology of computer system and system time, which is applied in the field of communication and computer, can solve the problems of artificial interference and lack of inspection measures in the method of time validity, and achieve good monitoring effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach
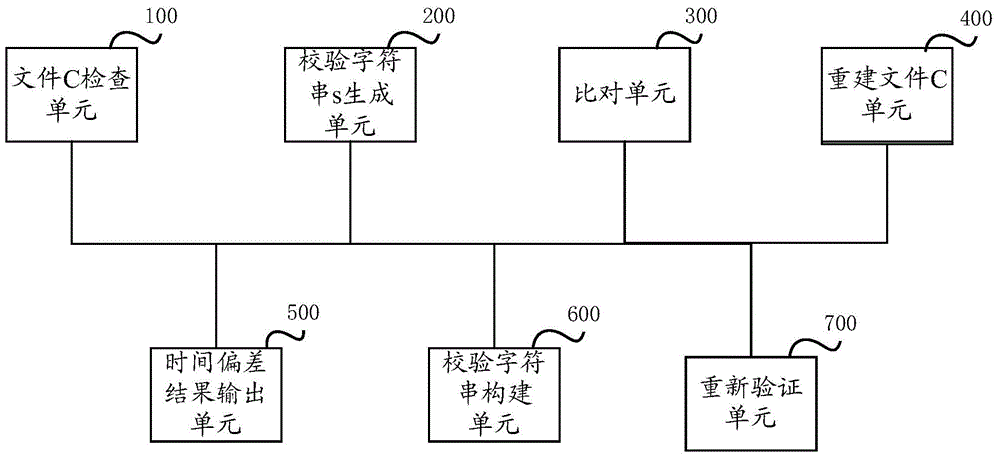
[0043] Specific embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings. However, the embodiments of the present invention are not limited thereto.
[0044] The basic principle of each embodiment of the present invention is: in the computer system to be checked, periodically maintain an array composed of feature descriptions of all checkpoint times in the valid time range, the array describes the valid time range, and when the check time arrives When comparing the system time feature description with the values in the array, if the same feature description exists in the array, it means that the system time deviation does not exceed the predetermined range, otherwise a prompt is given. When the array is first established or reestablished after failure, it is necessary to input the time characteristic description from the reference system to determine whether the current system time is within the valid range.
[004...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com