A Source Location Privacy Preservation Method for Phantom Routing in Sector Domain
A fan-shaped, phantom technology, applied in security devices, wireless communications, electrical components, etc., can solve the problems of short distance, small number, and centralized distribution of phantom nodes, and achieve the effect of prolonging security time, increasing difficulty, and improving security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
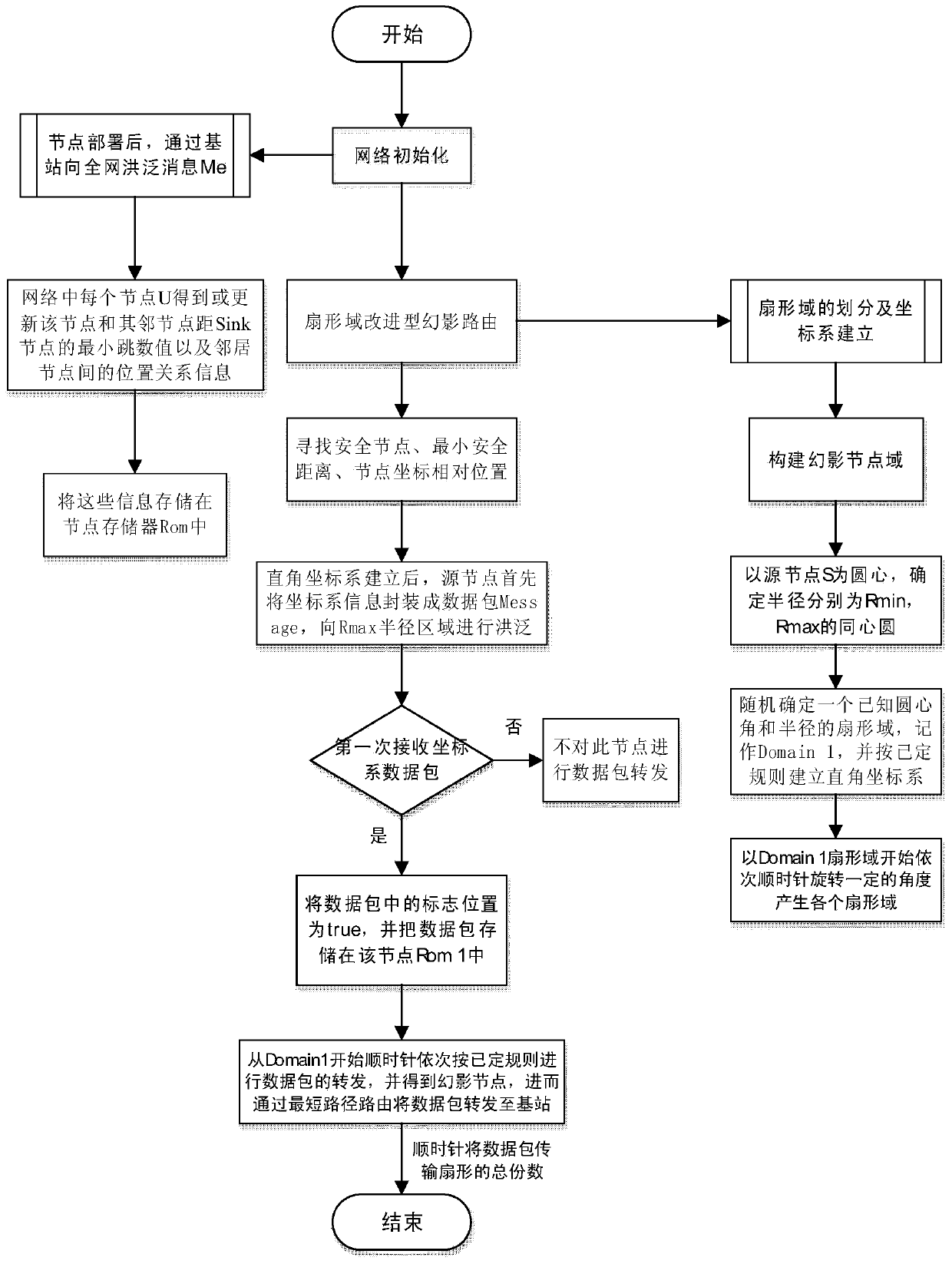
[0014] The specific implementation steps of the present invention will be further explained in detail below in conjunction with the accompanying drawings.
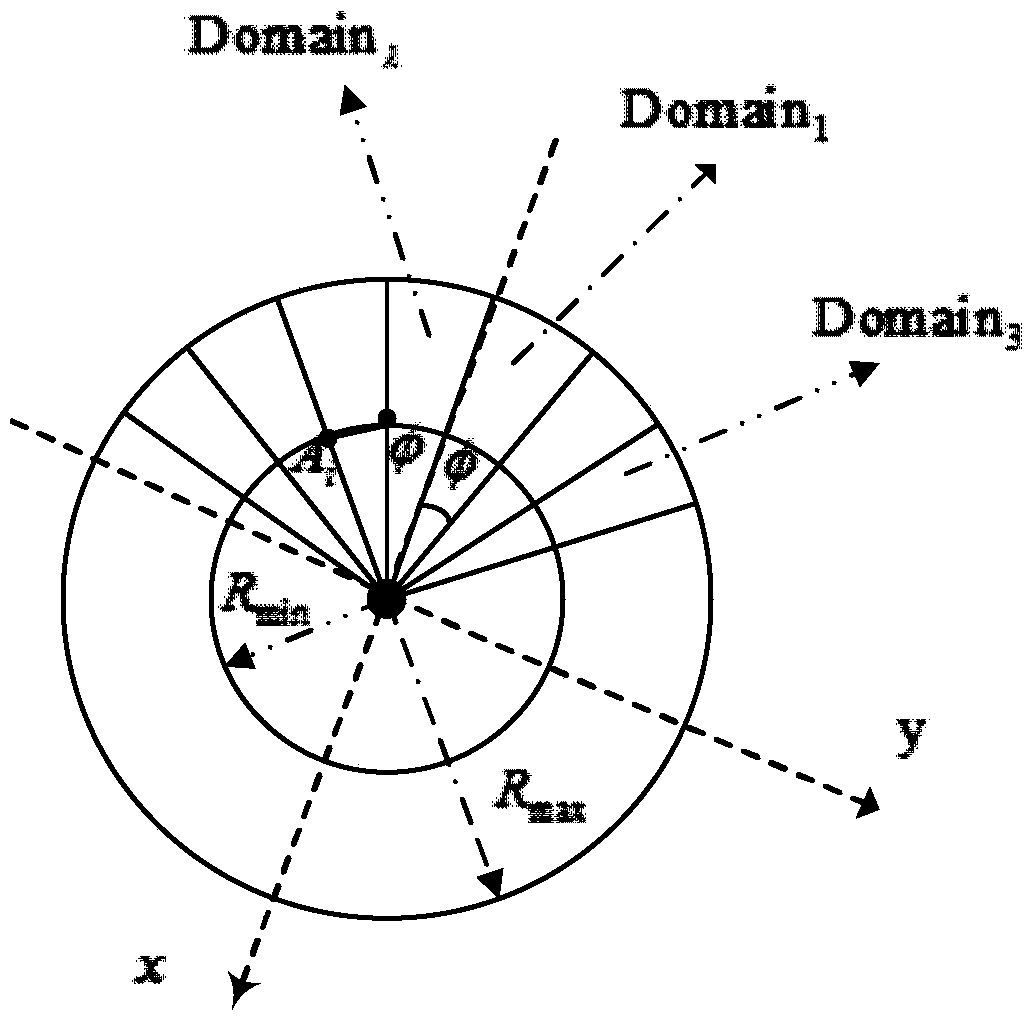
[0015] figure 1 The source location privacy protection system model established for the present invention includes a network model and an attacker model.
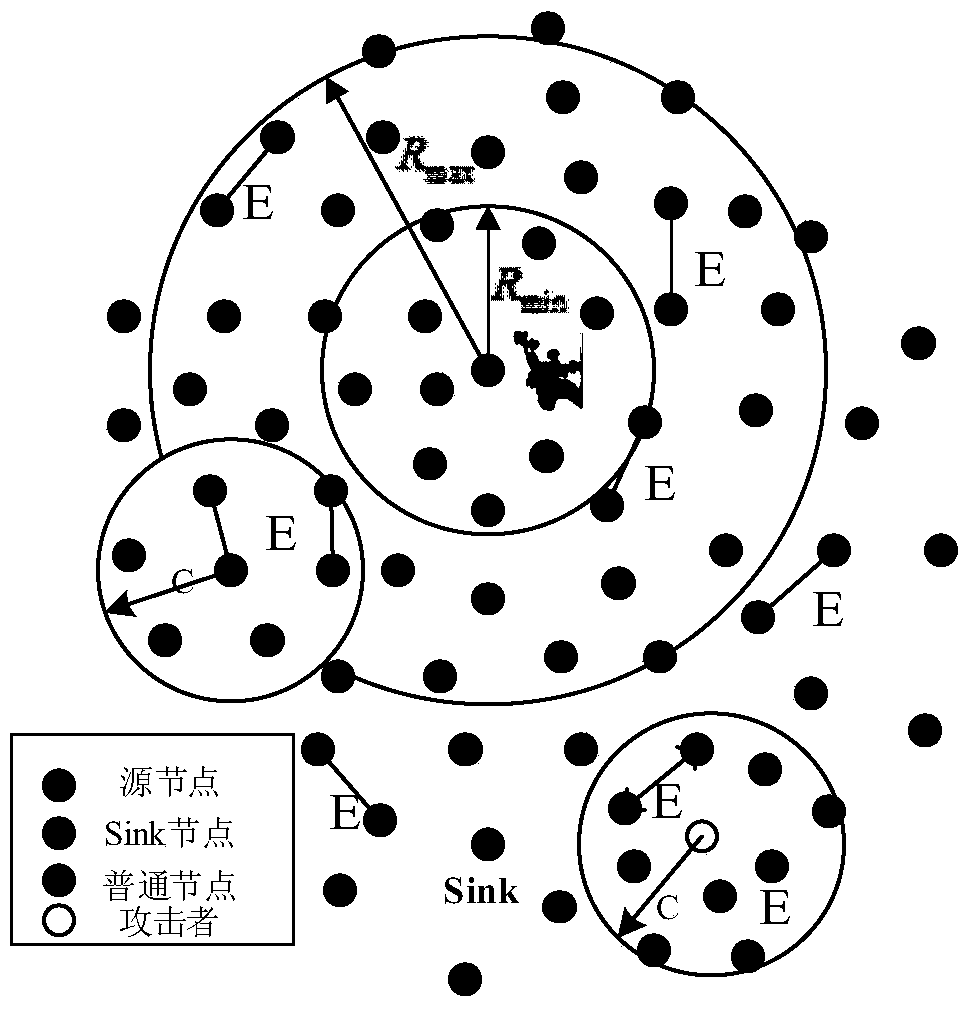
[0016] Network model: there is only one Sink node (base station node) in the wireless sensor network; once a certain node is used as the source node S, the node remains static and continues to send data packets to the Sink node within a certain period of time; each node in the network All have the position information S_Position of the Sink node; the effective transmission radius of the node is recorded as C, and the average distance between nodes within the transmission radius C is recorded as E.
[0017] Attacker model: The attacker is located near the Sink node during initialization, and only monitors within the radius C; the attacker can not obtain the location inf...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com