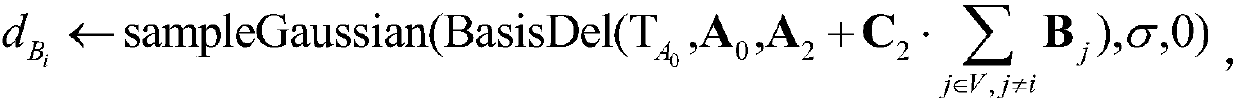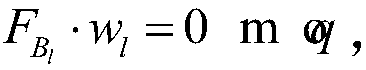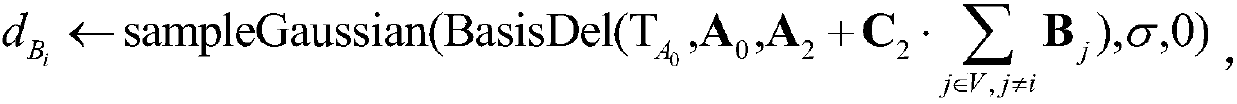Reversible Identity-Based Encryption Method Based on Accumulator on Lattice
An encryption method and an accumulator technology, applied in the field of identity-based encryption, can solve problems such as user private key leakage and difficulty in resisting quantum attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0059] The present invention will be described in detail below in combination with specific embodiments.
[0060] The reversible identity-based encryption method based on the accumulator in the grid of the present invention is specifically implemented according to the following steps:
[0061] Step 1. System establishment:
[0062] Specifically follow the steps below:
[0063] Step (1.1), input the security parameter λ, and the sum N of the maximum number of users and the number of time periods, so that the user identity here period Define φ as a one-to-one mapping φ(id)=d, φ(t)=l,d,l∈{1,…,N}, set parameter m=2nlog q,
[0064] Step (1.2), use the lattice-based trapdoor generation algorithm TrapGen(q,n) to generate a random uniform n×m dimensional matrix as well as base Satisfy
[0065] Step (1.3), select 4 random uniform matrices and 2n-1 random uniform matrices Choose an n-dimensional vector uniformly at random
[0066] Step (1.4), let U denote th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com