A network security log template extraction method and device
A network security and log technology, applied in the field of information security, can solve the problem that it is difficult for analysts to extract log templates, log format changes, etc., to achieve high accuracy, reduce system load, and improve computing efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] In order to make the above objects, features and advantages of the present invention more obvious and understandable, the present invention will be further described below through specific embodiments and accompanying drawings.
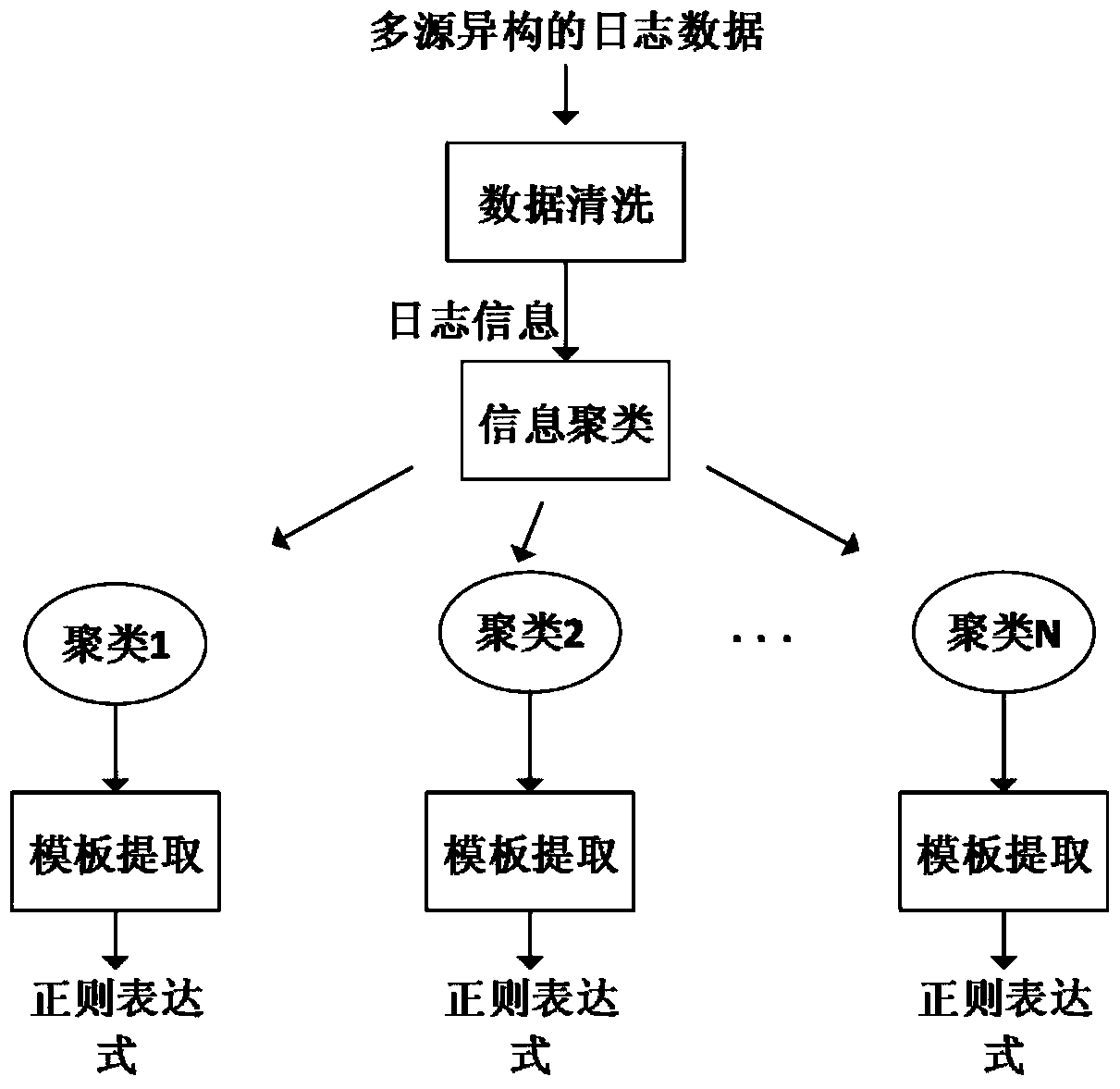
[0033] The network security log template extraction method provided by the present invention, its main steps include data cleaning, information clustering and template extraction, such as figure 1 shown. Among them, data cleaning is to first filter the fields with specific formats in the log data, including date, IP address, etc.; information clustering is to use clustering algorithm to divide the logs with similar formats into one category after cleaning. Medium; template extraction is to extract the template words describing the format in the log for each log in the class, and only keep the template words in the original log to obtain the log format.
[0034] 1. Data cleaning
[0035] The data cleaning in this method is mainly to filter out...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com