Isolation operation method for Linux application program
A technology of application program and operation method, applied in the computer field, which can solve the problems of interfering with the daily work of users, data security and personal privacy, hindering the normal execution of other programs, and unmaintainable system suspended animation.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] The present invention will be described in further detail below in conjunction with the accompanying drawings and embodiments. The following examples are used to illustrate the present invention, but should not be used to limit the scope of the present invention.
[0026] A method for isolated running of Linux applications, such as figure 1 As shown, the method includes the following steps:
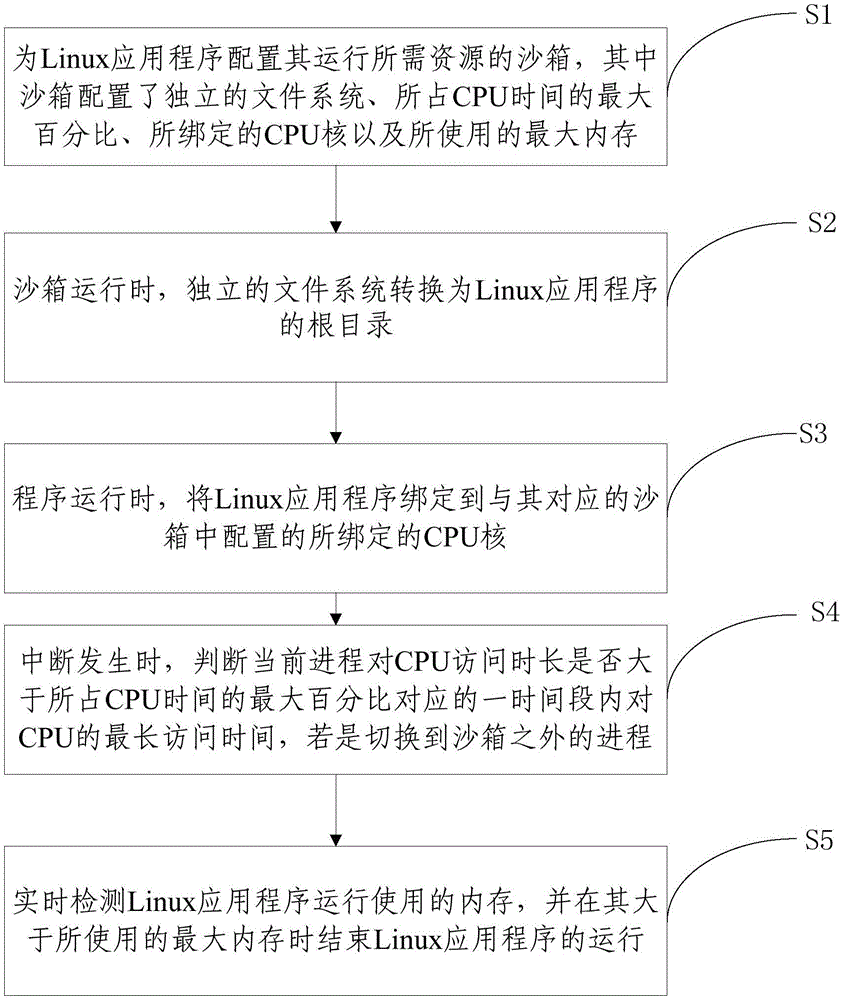
[0027] S1. Configure a sandbox for the resources required for the Linux application to run, wherein the sandbox is configured with an independent file system, a maximum percentage of CPU time, a bound CPU core, and a maximum memory used;
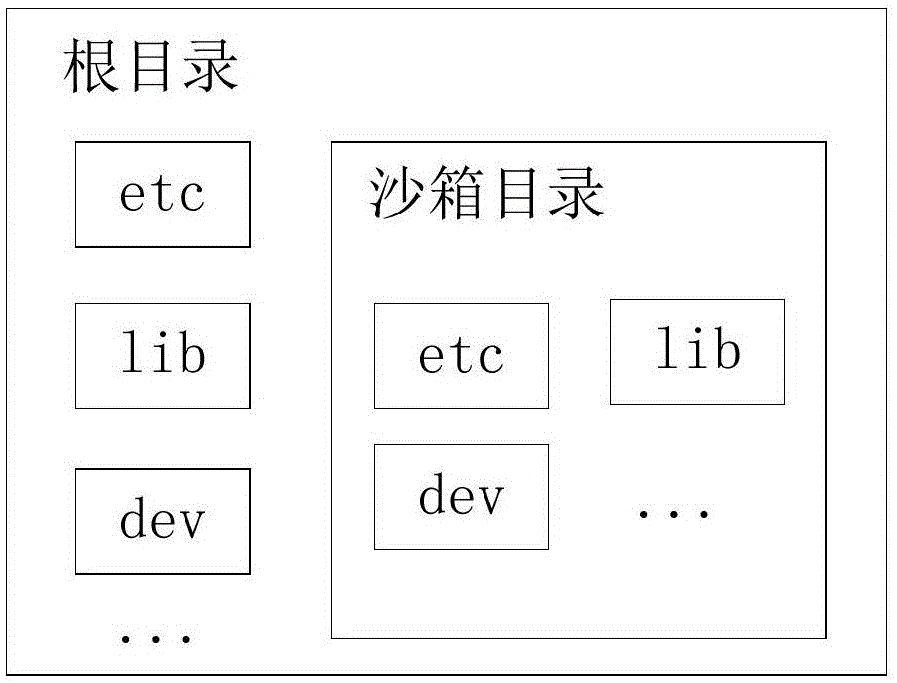
[0028] S2. When the sandbox is running, the independent file system is converted into the root directory of the Linux application program;
[0029] S3. When the program is running, bind the Linux application program to the bound CPU core configured in the corresponding sandbox;
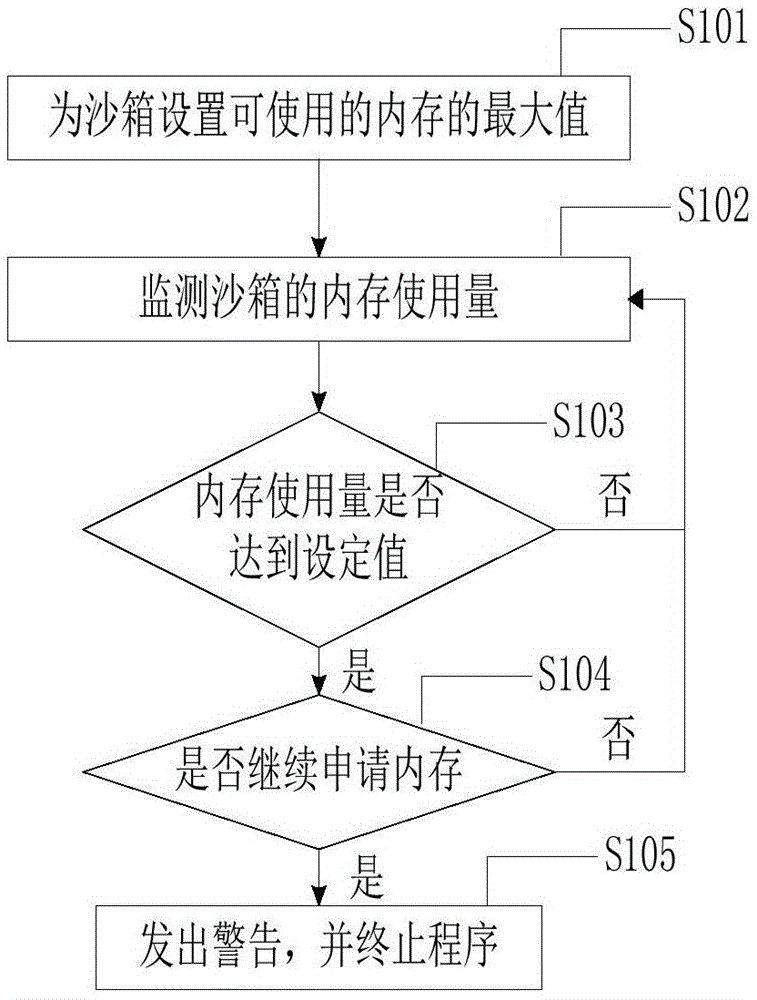
[0030] S4. When an interruption occurs, determine whether the cu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com