Encrypted application identification and encrypted webpage content classification methods, and encrypted application identification and/or encrypted webpage content classification devices
A technology for application identification and web page content, applied in the field of network application security, it can solve the problems of random data, large amount of calculation, and no obvious packet-length sequence characteristics in the data stream, and achieve the effect of ensuring accuracy and efficient identification.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
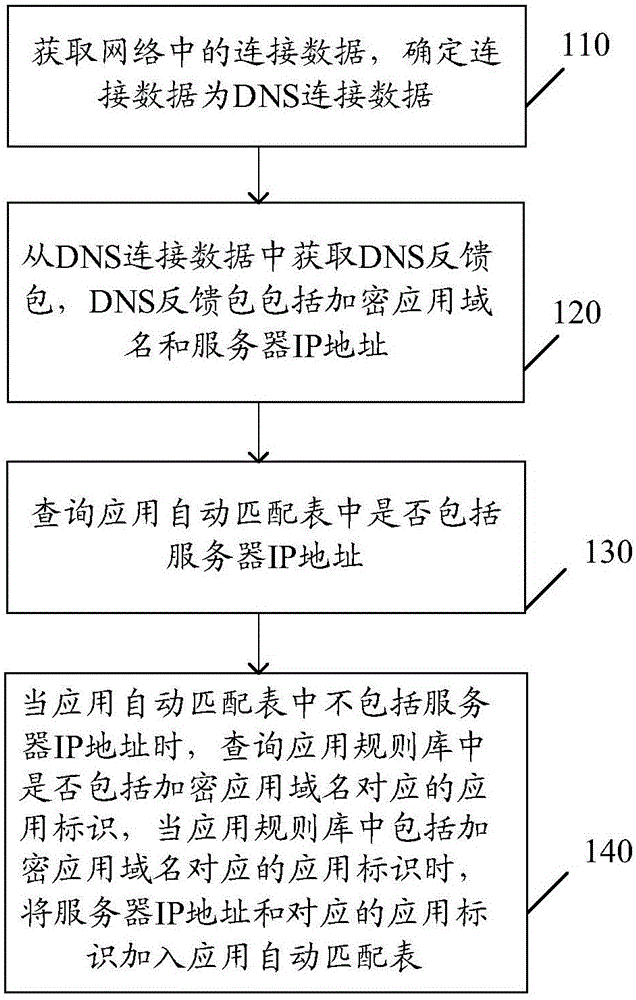
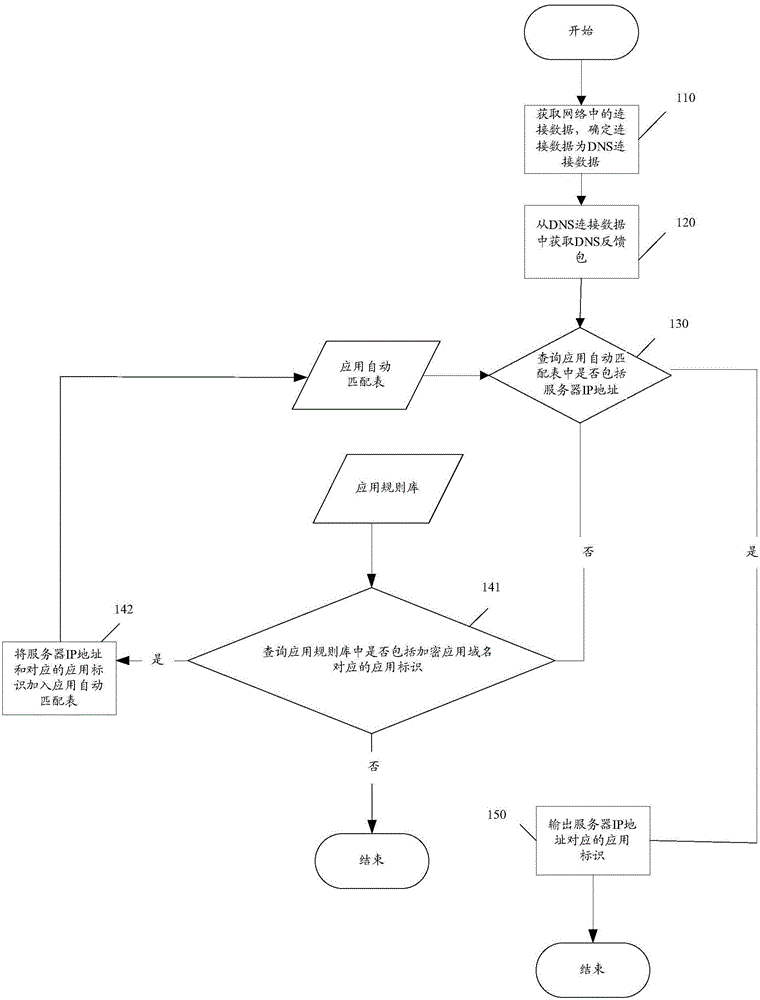
[0072] figure 2 and image 3 It is a schematic diagram of the implementation flow of the encrypted application identification method provided in Embodiment 1 of the present invention, as shown in image 3 As shown, the encryption application identification method includes:
[0073] Step 110: Obtain connection data in the network, and determine that the connection data is DNS connection data.
[0074] In step 110, the device for identifying encrypted applications, or the device for identifying encrypted applications and classifying encrypted webpage content acquires and analyzes information in the connection data in the network. The connection data is any connection data in the network, and may include DNS connection data and the like.
[0075] Specifically, the device for identifying encrypted applications, or the device for identifying encrypted applications and classifying encrypted webpage content monitors the network and acquires the connection data.
[0076] Here, th...
Embodiment 2
[0094] Embodiment 2 is an HTTPS identification method. When the encryption application is HTTPS, the HTTPS identification method includes:
[0095] Obtain connection data in the network, and determine that the connection data is DNS connection data;
[0096] Obtaining a DNS feedback packet from the DNS connection data, the DNS feedback packet including an HTTPS domain name and an HTTPS server IP address;
[0097] Query whether the HTTPS server IP address is included in the application automatic matching table;
[0098] When the application automatic matching table does not include the HTTPS server IP address, query whether the application rule base includes the application identification corresponding to the HTTPS domain name, and when the application rule base includes the application identification corresponding to the HTTPS domain name , adding the HTTPS server IP address and the corresponding application identifier to the application automatic matching table.
[0099] F...
Embodiment 3
[0102] Figure 4 and Figure 5 It is a schematic diagram of the implementation flow of the method for classifying encrypted webpage content provided by Embodiment 3 of the present invention. It should be noted that the application type in the method for classifying encrypted webpage content is HTTPS. Such as Figure 5 As shown, the encrypted webpage content classification method includes:
[0103] Step 210: Obtain connection data in the network, and determine that the connection data is DNS connection data.
[0104] Step 220: Obtain a DNS feedback packet from the DNS connection data, where the DNS feedback packet includes an encrypted application domain name and a server network protocol IP address.
[0105] Step 230: When it is determined that the encryption application is HTTPS, check whether the IP address of the server is included in the classification automatic matching table.
[0106] Here, the category automatic matching table is pre-configured by the device for cl...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap