Confidence leakage protection method and device
An illegal and legal technology, applied in the network field, can solve problems such as blocking normal connections
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
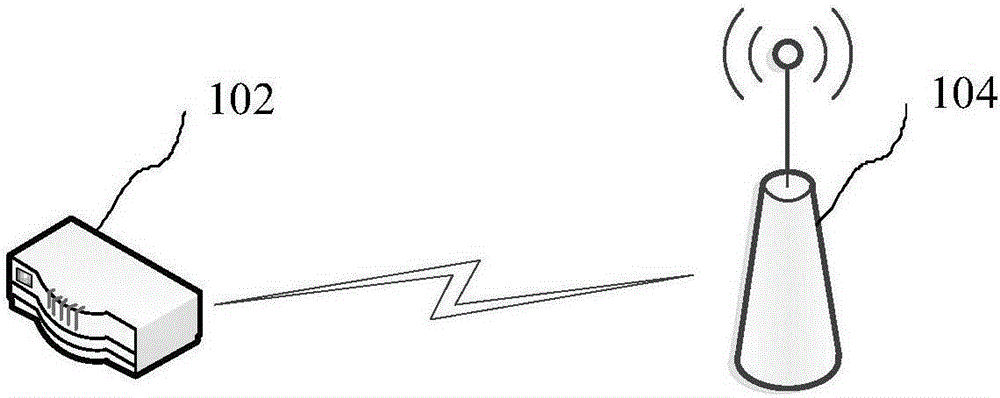
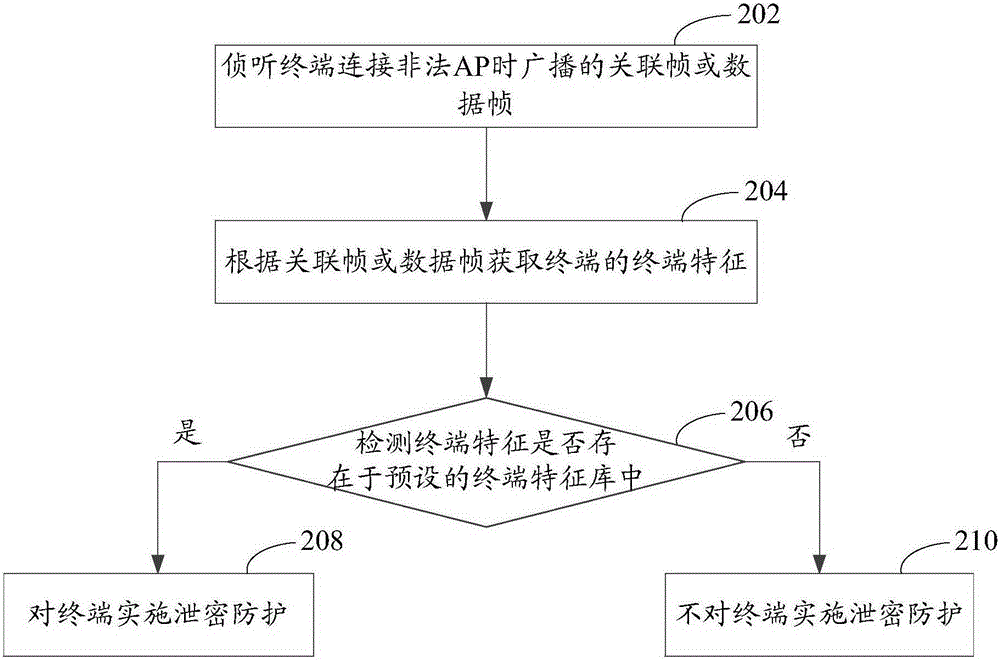
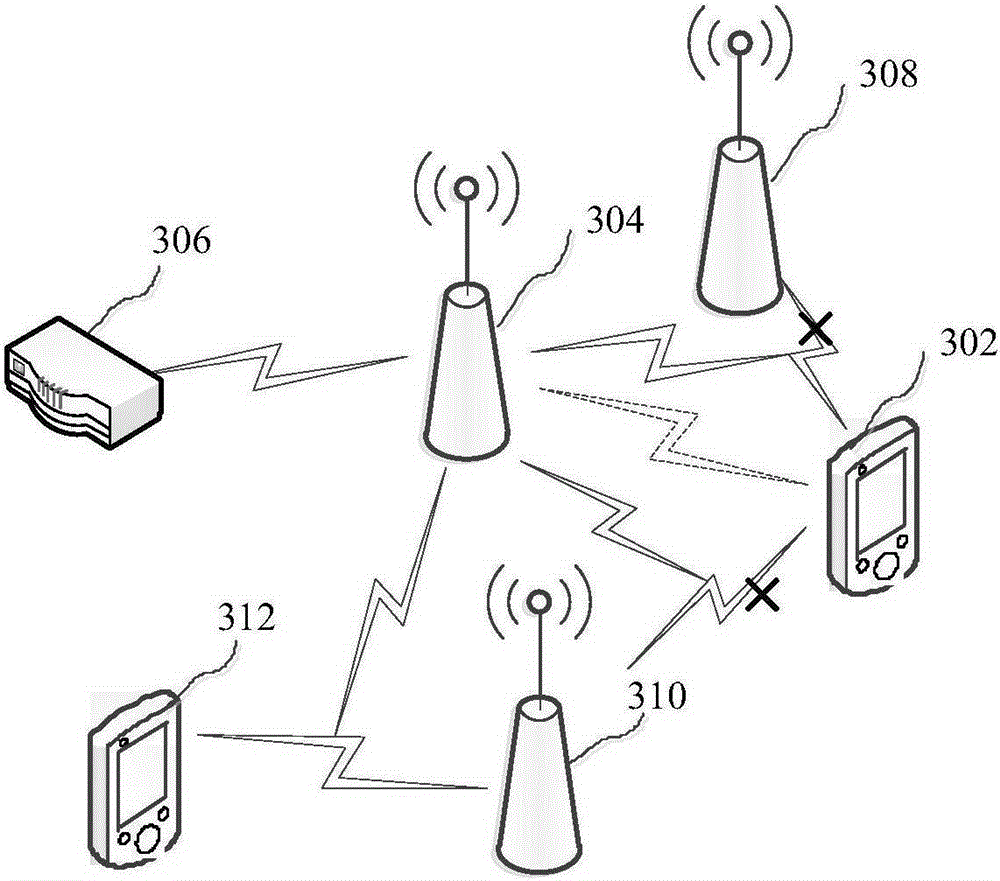
[0022] The leakage prevention method provided by the embodiment of the present invention can be applied to such as figure 1 environment shown. refer to figure 1 As shown, the wireless controller 102 can centrally control multiple APs, such as one of the APs 104 , through a wired connection or a wireless connection. The wireless controller 102 includes a terminal feature library for storing terminal features. The wireless controller 102 can send information to the terminal, and can also receive data transmitted by the AP 104 and analyze the received data to obtain specific information. AP104 can listen to the association frame or data frame broadcast within its coverage when the terminal connects to other APs or itself, and can also listen to the wireless data transmitted between the terminal and the illegal AP when the terminal has successfully connected to the illegal AP In addition, the AP 104 can also send information to terminals and other APs. Wherein, the association ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com