Multi-factor authentication techniques
A technology for verifying information and verifying components, which is applied in the field of multi-factor verification technology and can solve problems such as theft of user names, passwords and mobile IDs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] 1. Typical scenarios that can be verified
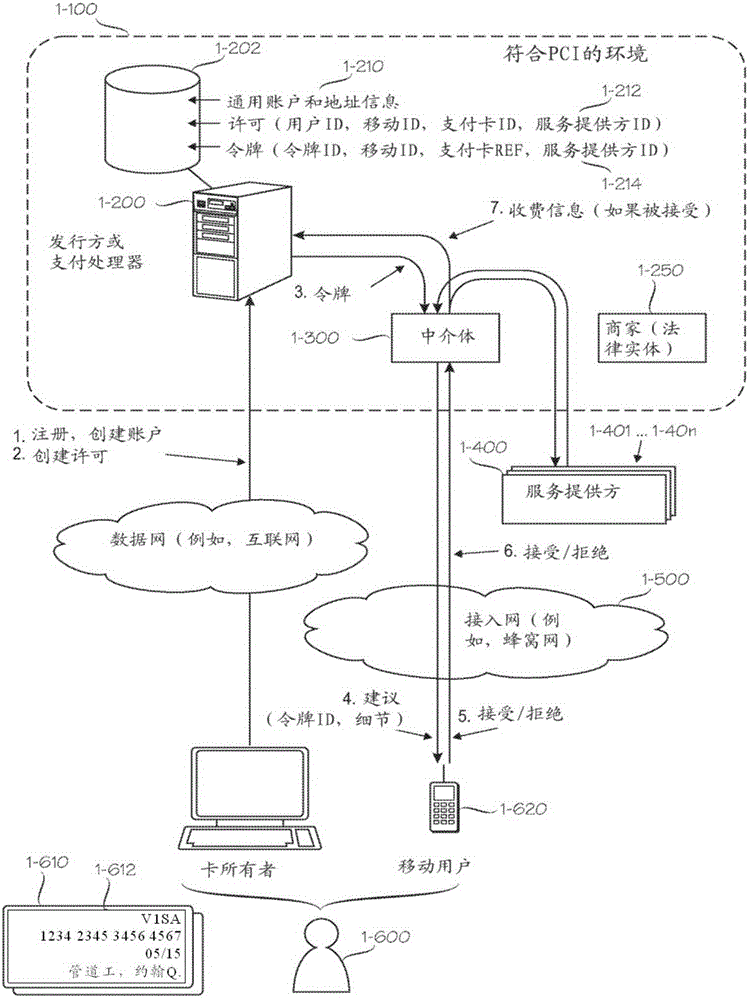
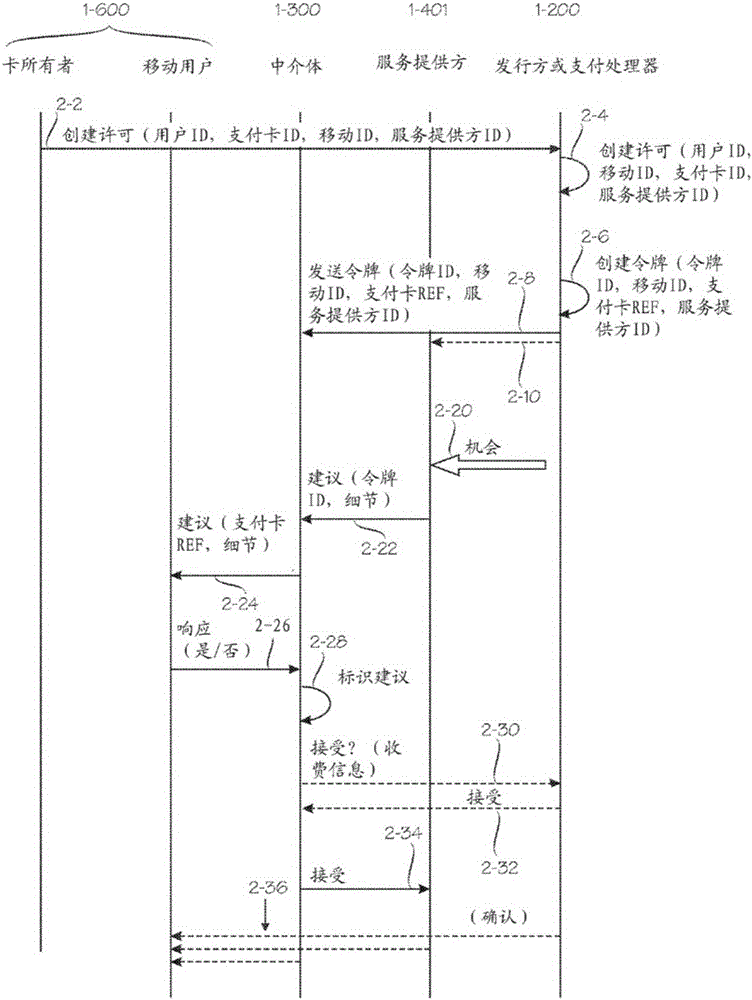
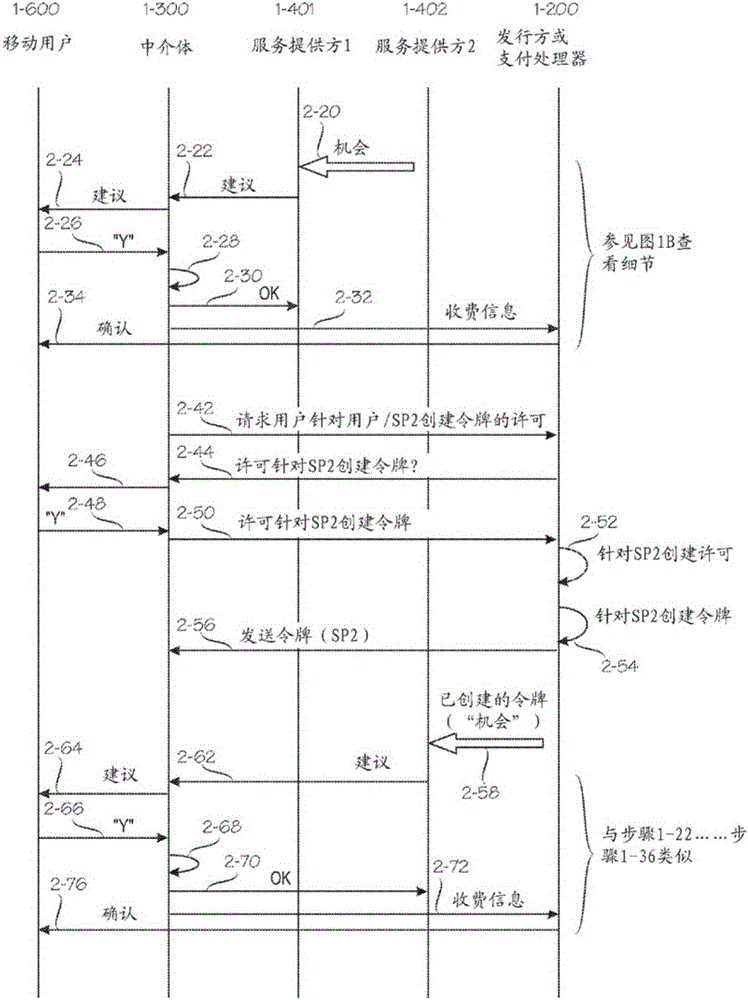
[0034] figure 1 , Figure 2A with Figure 2B Shows how embodiments of the invention can be configured to cooperate with other legal entities to form a composite framework that facilitates provision of services and payments. The following description of this composite framework will illustrate various perspectives on validation. One point of view is that modern e-commerce involves multiple cooperative entities, and naturally involves many mutual verification issues. Another point to make is that there are many different situations that have different requirements for the verification process, especially with regard to security and convenience, which should be properly balanced. Another point to make is that although a large number of entities are involved, it is still possible for a centralized authentication server to perform authentication for many or all of these entities.
[0035] in particular, figure 1 , Figure ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com