Network topology checking method and system thereof
A technology of network topology and information system, applied in the field of network topology investigation method and system thereof, can solve problems such as breakthrough of physical isolation defense line, generation of hidden dangers of information security of business system, generation of illegal outreach of business system, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
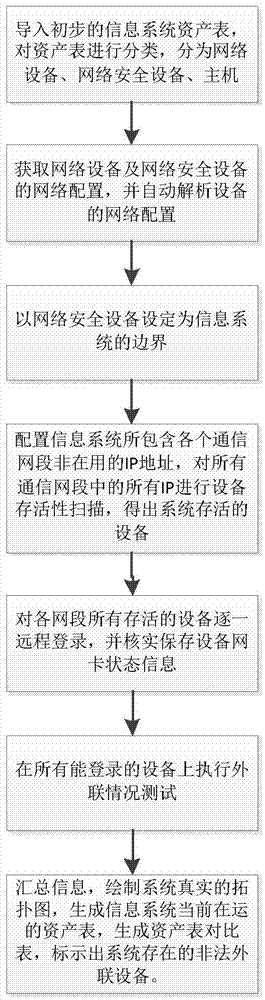
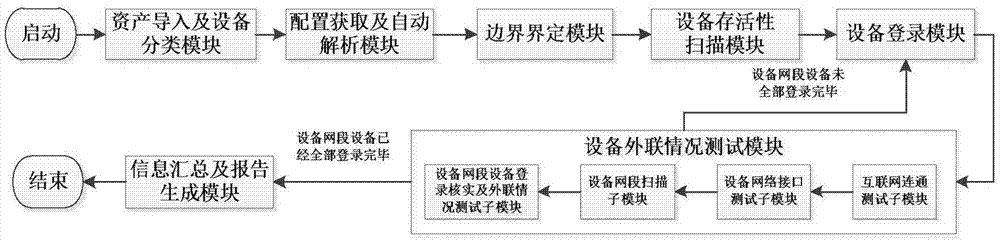
[0045] In the actual operation process, the specific implementation method is as follows:
[0046] 1) The system administrator provides the initial information system asset list of the information system (including the account information of the device, and the user name and password information of the device), and provides the preliminary information system asset list to Network topology checking software or network topology checking device or network topology checking system;
[0047] 2) Network topology checking software or network topology checking device or network topology checking system divides the preliminary information system asset list provided by the information system into three categories: network equipment, network security equipment and host.
[0048] 3) The network topology checking software or network topology checking device or network topology checking system obtains the configuration of network equipment and network security equipment. The way of transmi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com