A device for network topology troubleshooting
A network topology and network security technology, which is applied in the field of network security and can solve the problems of generating illegal outreach of business systems, breaking through the defense line of physical isolation, and generating hidden dangers of information security of business systems.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
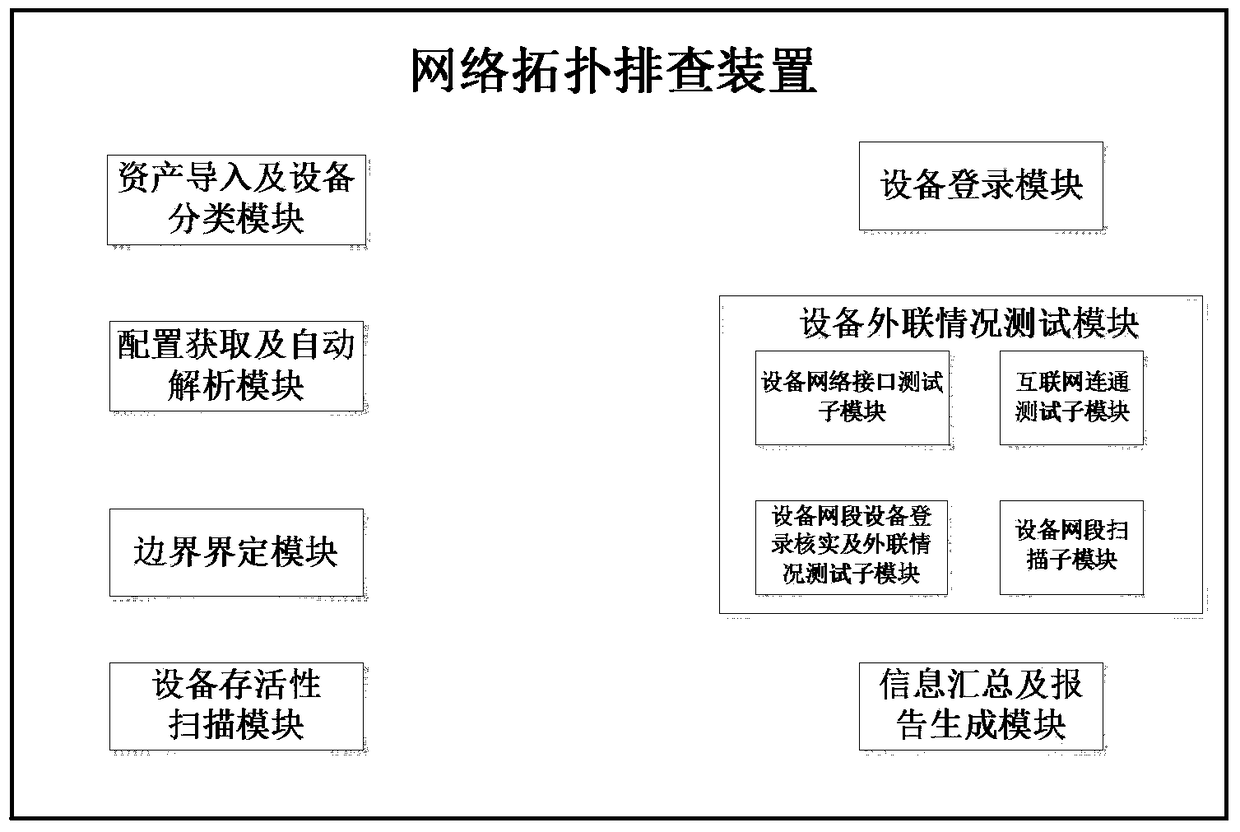
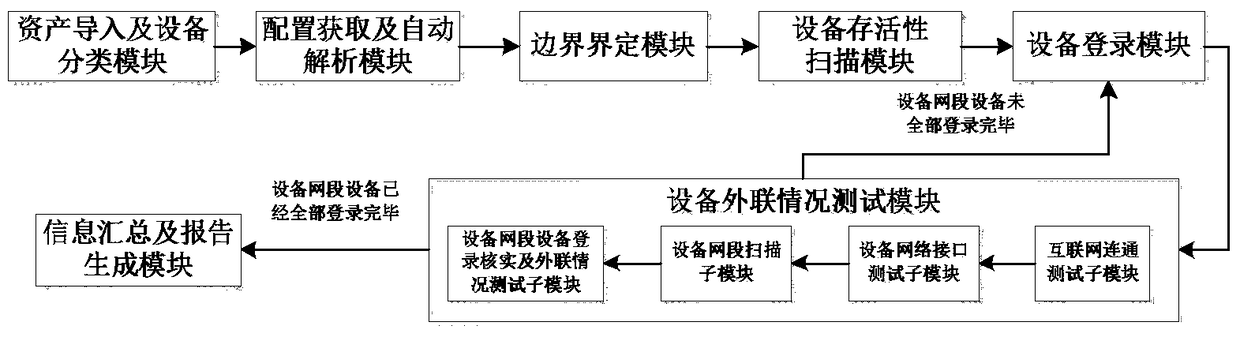
[0028] The purpose of the present invention is to provide a device for network topology troubleshooting. The device of the present invention can quickly and effectively ascertain the network connection status of the information system, automatically generate a topological map of the system that is true and consistent with the system's operating conditions, effectively discover illegal outreach in the information system, and assist operation and maintenance personnel and inspection personnel Quickly locate and eliminate system security risks to ensure the security of information systems.
[0029] The network topology investigation device mainly includes the following seven modules: asset import and equipment classification module, configuration acquisition and automatic analysis module, boundary definition module, equipment survivability scanning module, equipment login verification module, equipment outreach testing module, and information summary and report generation module;...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com