System and method for identifying compromised private keys
A technology for private keys and applications, the application cares that the agent can use the leaked private key to sign the field, which can solve the problem of lack of a mechanism for whether the private key has been leaked
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
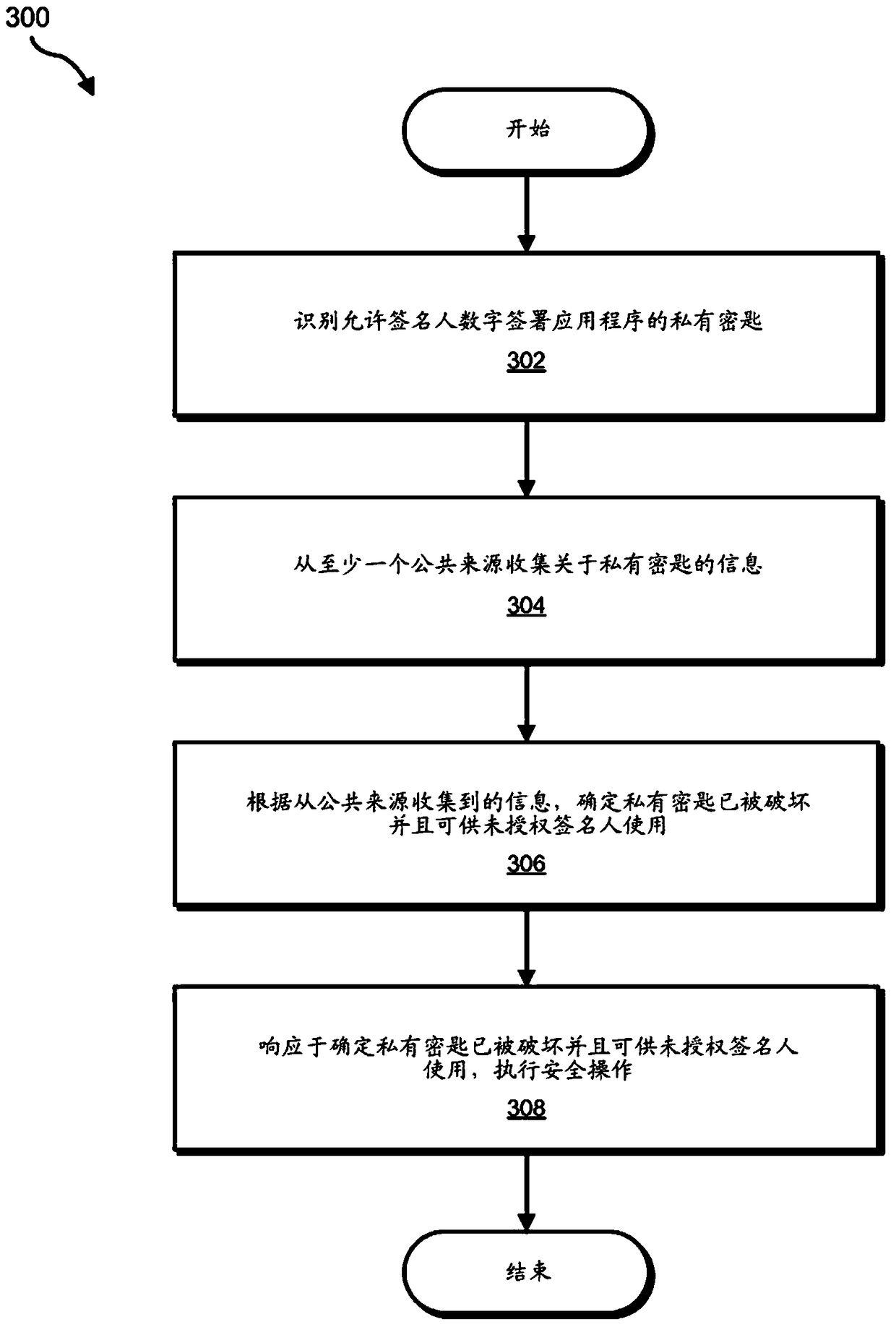
[0023] The present invention generally relates to systems and methods for identifying compromised private keys. As will be explained in more detail below, by determining that a private key has been compromised based on analysis of information gathered from publicly available sources, the system described herein can (1) sign the application with a compromised private key by alerting the user , to increase the security of users, (2) to increase the security of signers by warning signers that their private keys have been compromised, and / or (3) to reduce the security of applications signed with compromised private keys. reputation score and / or block the application to improve the security of the application distribution platform.
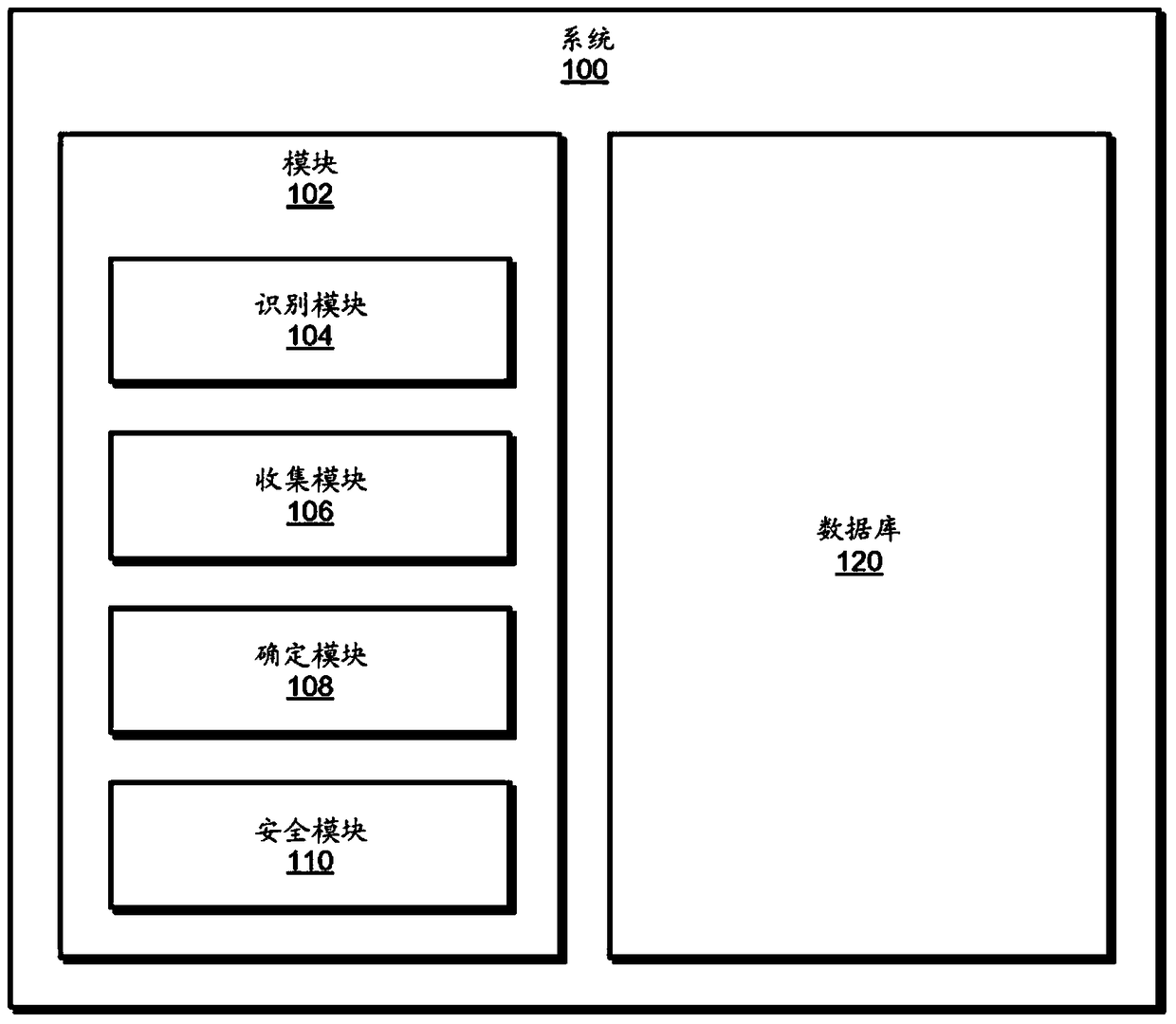
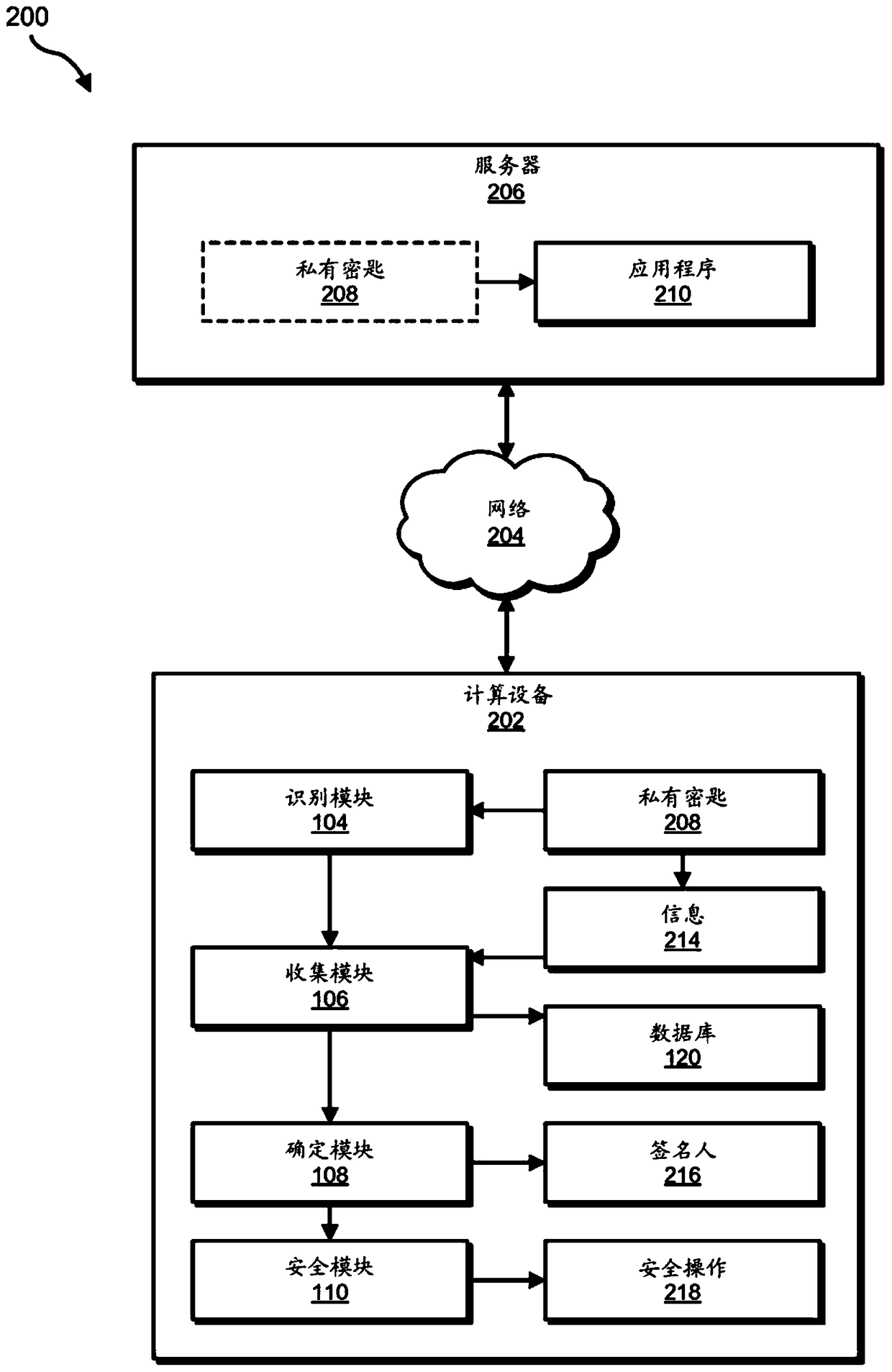
[0024] will be combined below Figure 1 to Figure 2 , Figure 4 with Figure 5 A detailed description of an exemplary system for identifying compromised private keys is provided. will also combine image 3 A detailed description of the correspondi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com