A network real-name authentication method and system
A real-name authentication and network technology, applied in transmission systems, user identity/authority verification, electrical components, etc., can solve problems such as weak security, poor implementability, and easy leakage of personal privacy, so as to achieve no leakage of personal privacy, Highly implementable effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
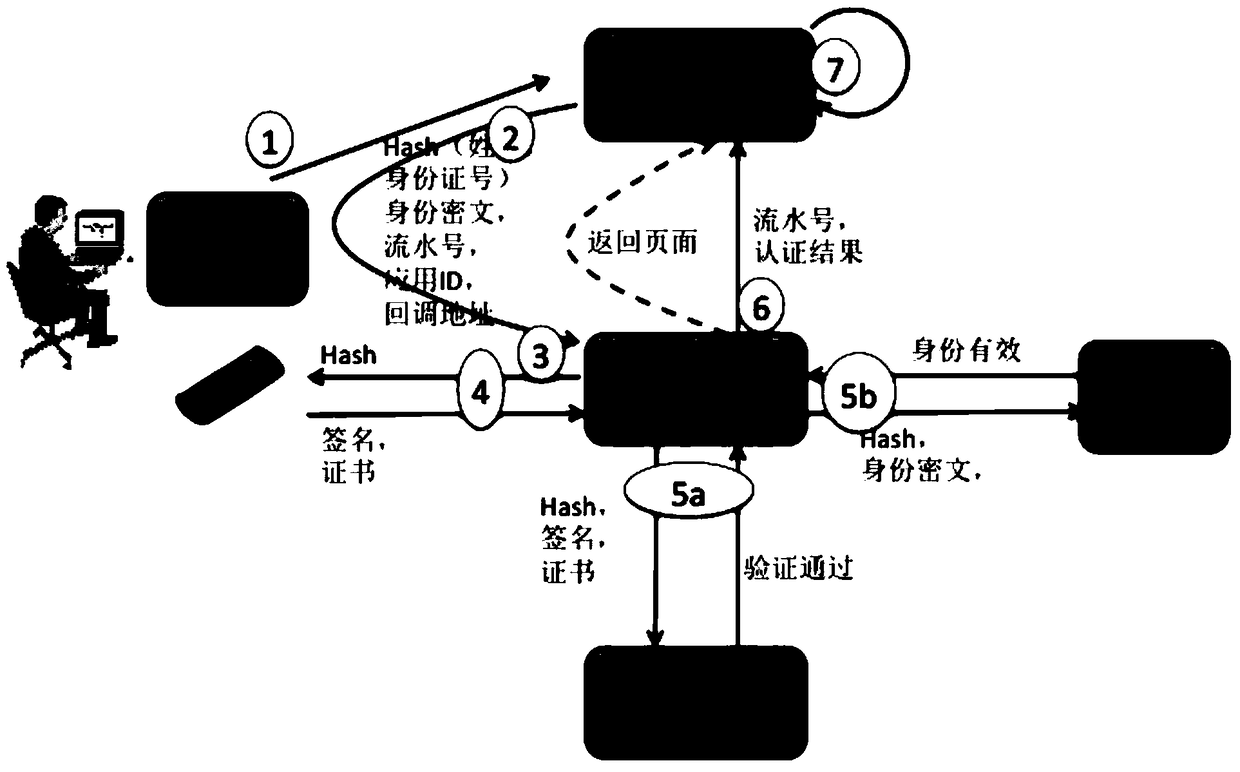
[0089] In order to make the description of the present invention more detailed and complete, the embodiments and specific embodiments of the present invention will be described below with reference to the accompanying drawings; but this is not the only form for implementing or using the specific embodiments of the present invention. The various embodiments disclosed below can be combined or replaced with each other when beneficial, and other embodiments can also be added to one embodiment, without further description or illustration.
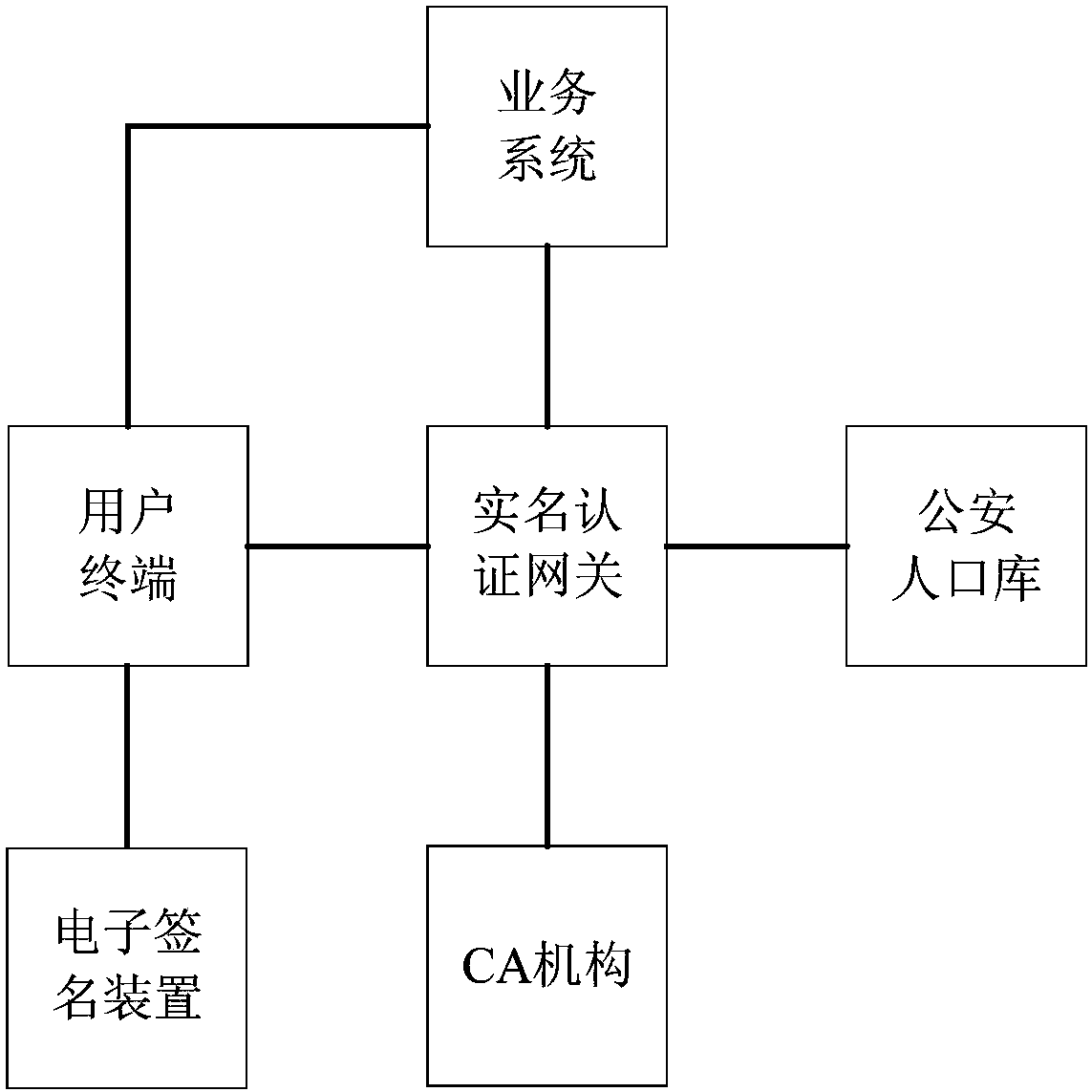
[0090] The present invention mainly uses the existing basic implementation and combines a real-name authentication gateway to complete the network real-name authentication. These infrastructures include:
[0091] (1) An electronic signature device, such as a UKey issued to a user by a bank. At present, in our country, in order to protect the security of its online banking, various banks have issued a large number of electronic signature devices...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com