Defense method and system for cross-site scripting attack
A cross-site scripting attack and defense system technology, applied in transmission systems, instruments, computing, etc., can solve problems such as low operating efficiency, detection of non-attack events, and non-detection of attack events, etc., to achieve high operating efficiency and good defense The effect of the function
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
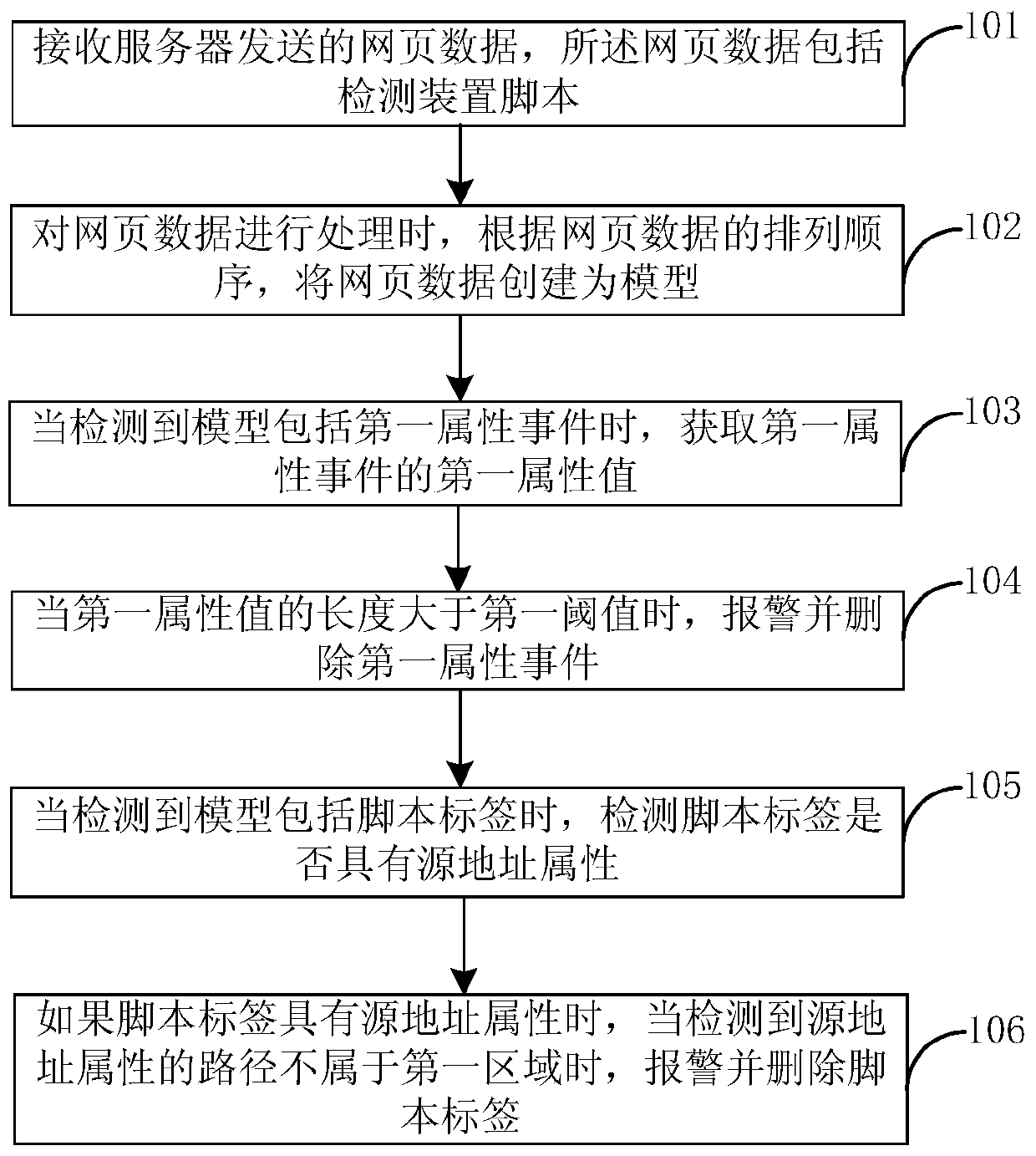
[0020] figure 1 It is a flow chart of the defense method for cross-site scripting attack provided by Embodiment 1 of the present application. This example is applicable to the processing scenario of web page data, and this embodiment can be executed by the client.
[0021] Such as figure 1 As shown, the defense method of cross-site scripting attack in this application specifically includes the following steps:
[0022] Step 101, receiving the web page data sent by the server, the web page data including the detection device script;
[0023] The client receives the web page data sent by the server. First, the client sends a request to the server, and then receives the webpage data that the server responds to. The difference between the webpage data here and ordinary webpage data is that the webpage data includes the detection device script.
[0024] Optionally, the detection device script is located in the first line after the header tag of the web page. For example, the ...
Embodiment 2
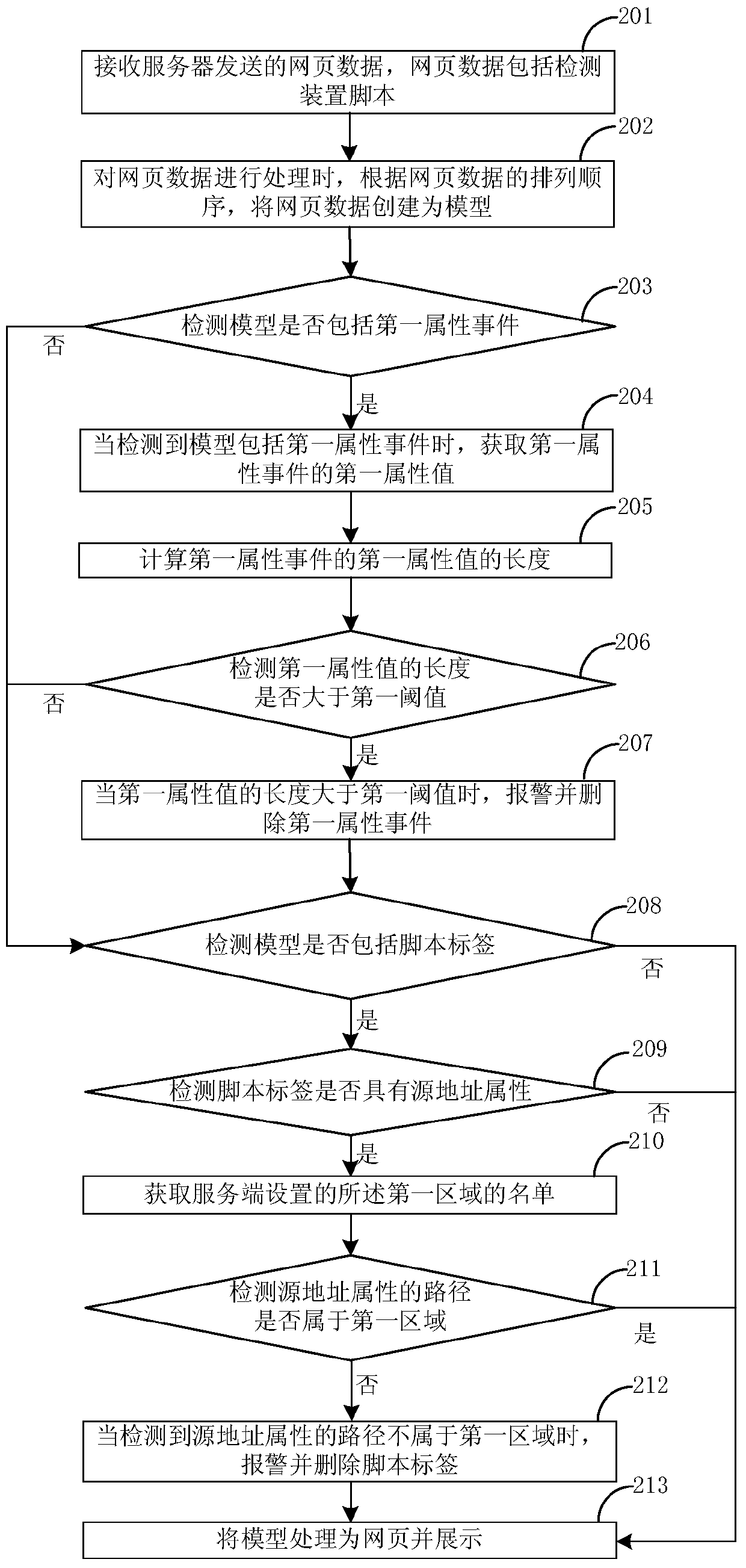
[0105] figure 2 It is a specific flow chart of the cross-site scripting attack defense method provided in Embodiment 2 of the present application. This example is applicable to the processing scenario of webpage data, and this embodiment can be executed by the client, and the same or similar points between the second embodiment and the first embodiment can be referred to.
[0106] Such as figure 2 As shown, the defense method of cross-site scripting attack in this application specifically includes the following steps:
[0107] Step 201, receiving the webpage data sent by the server, the webpage data includes the detection device script;
[0108] The detection device script is located in the first line after the header tag of the web page.
[0109] Step 202, when processing the webpage data, create the webpage data as a model according to the sequence of the webpage data;
[0110]Optionally, the creating the web page data as a model specifically further includes: adding c...
Embodiment 3
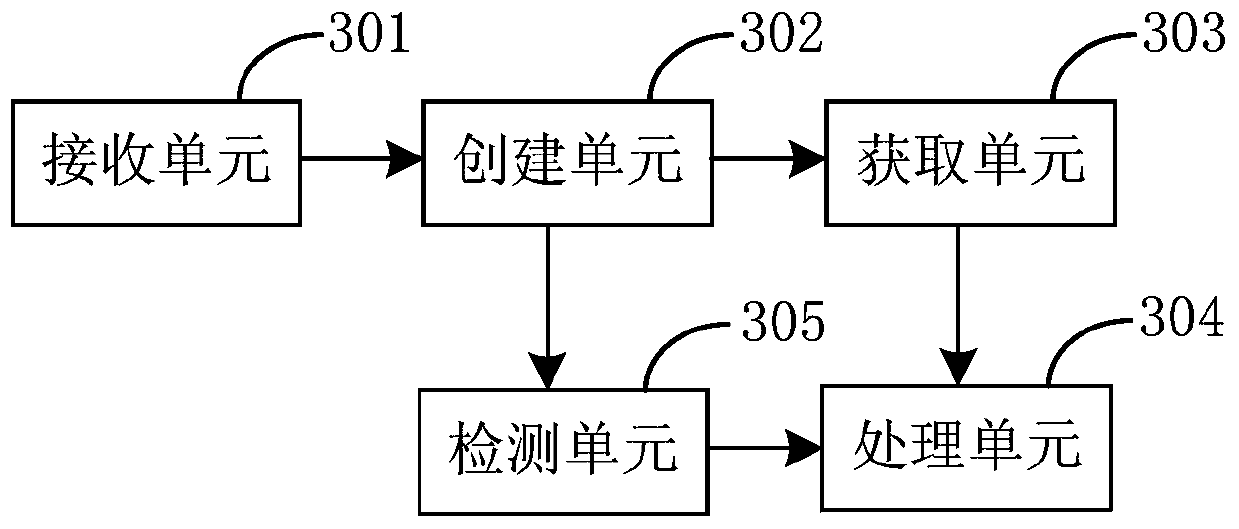
[0131] Corresponding to the cross-site scripting attack defense method provided in the first embodiment of the present application, the third embodiment of the present application also provides a cross-site scripting attack defense system, the system is a client, see image 3 , the system may specifically include: a receiving unit 301 , a creating unit 302 , an acquiring unit 303 , a processing unit 304 and a detecting unit 305 .
[0132] The receiving unit 301 is configured to receive webpage data sent by the server, the webpage data including the detection device script;
[0133] The creating unit 302 is configured to create the webpage data as a model according to the arrangement order of the webpage data when processing the webpage data;
[0134] An acquiring unit 303, configured to acquire the first attribute value of the first attribute event when it is detected that the model includes the first attribute event;
[0135] A processing unit 304, configured to send an alar...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com