Identification method for judging home invasion in real time
An identification method and area identification technology, applied to instruments, anti-theft alarms, alarms, etc., can solve problems such as inability to perform image matching, inability to identify real-time alarm conditions, and inability to achieve monitoring effects, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0038] Example 1 Indoor monitoring
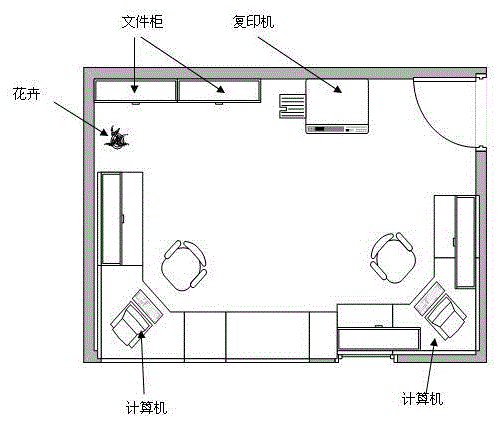
[0039] (1) Camera installation The cameras of the indoor real-time video surveillance system are generally installed on the opposite wall of the door entering the room or at a higher position on the side, so that all entrances and exits such as doors and windows enter the monitoring range of the camera as much as possible.
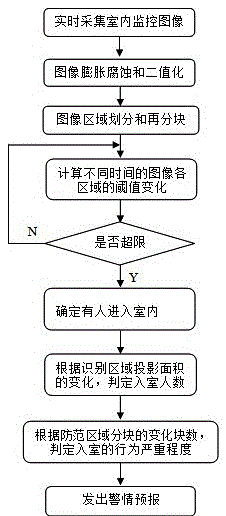
[0040] (2) After the camera is turned on, the system collects images in the monitoring area in real time, such as figure 2 shown.
[0041] (3) Preprocessing the collected images, including filtering, binarization, etc.
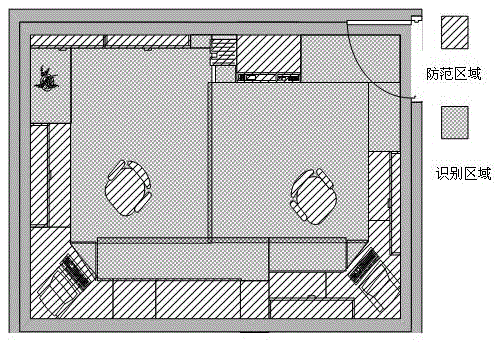
[0042] (4) Perform region division and block processing on the preprocessed real-time image. Such as image 3 As shown, the image in the monitoring area in the house is divided into the recognition area and the prevention area. The identification area is used to identify the human body characteristics of the intruder entering the room, such as height, body width, and number of people. The area, esp...
Embodiment 2
[0048] Embodiment 2 corridor monitoring
[0049] (1) The corridor is generally relatively empty. All the images obtained by the monitoring system can be divided into recognition areas.
[0050] (2) The block method of the recognition area. Same as Example 1
[0051] (3) Compare the intrusion image entering the monitoring area with the previous image to obtain the characteristics and quantity of the intruded human body.
[0052] (4) Send out alarm information and call the police.
Embodiment 3
[0053] Example 3 Area Monitoring
[0054] Different from Embodiment 1 and Embodiment 2, this embodiment adopts the same rules as Embodiment 1 and is completed on the basis of Embodiment 2.
[0055] (1) The personnel and vehicles in the area monitoring may change continuously, and as in implementation 2, all are divided into identification areas.
[0056] (2) Image block processing Determine the reference objects of personnel, various vehicles, etc., and perform block processing on the collected real-time images.
[0057] (3) According to the personnel and vehicles entering the monitoring area, identify the height, body width and quantity of personnel; identify the length, width and quantity of vehicles.
[0058] (4) Based on the information in (3) above, make statistics on the characteristic information of various identifiers.
[0059] The identification method of the present invention has the following beneficial effects:
[0060] (1) Without the human body infrared sensor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com