Image identifying code achievement method based on text adhesion and visual compensation
A picture verification code and visual compensation technology, which is applied in the field of network security, can solve the problem that the click input is easy to be cracked by violence, etc., and achieve the effect of easy automatic recognition, easy recognition, and good usability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] The technical solution of the present invention will be described in detail below in conjunction with the drawings.
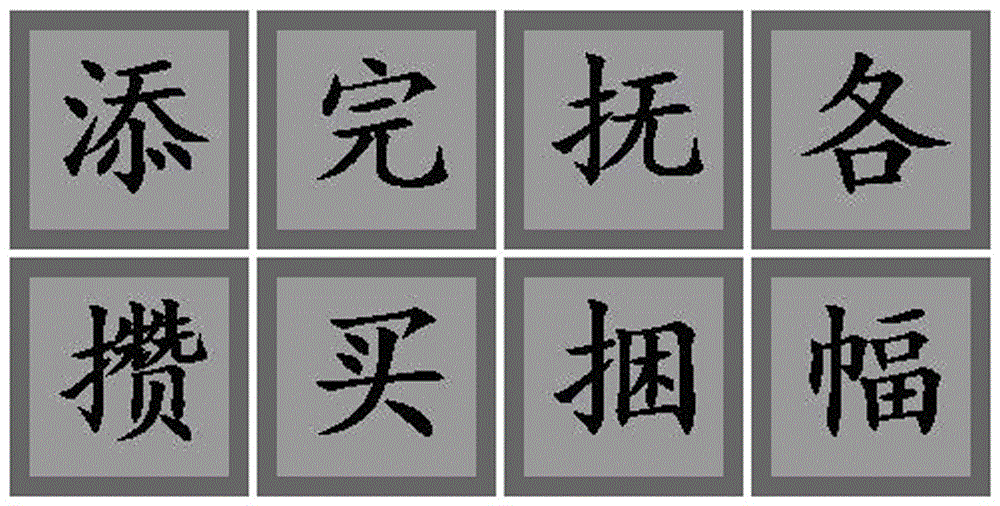
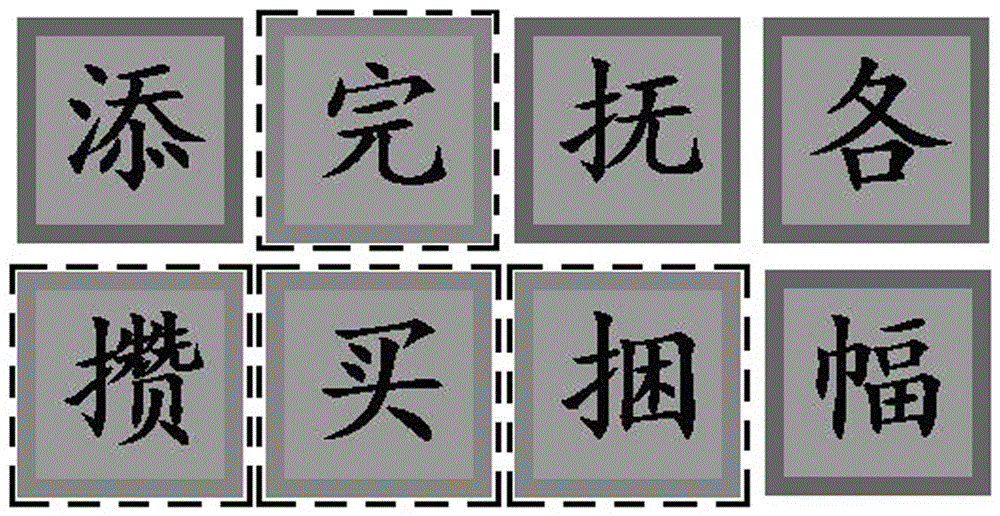
[0043] The present invention proposes a method for implementing image verification code based on text adhesion and visual compensation, which includes verification code and candidate code generation, verification code input and verification code verification.
[0044] (1) Generation of verification code and candidate code
[0045] 1. The server side randomly generates 4-32 different text characters according to the requirements of the user's corresponding preset verification level, these characters are used as candidate characters, and a 4-32 bit all 0 series number S0 is generated at the same time, each character Corresponds to one of the serial numbers. In this embodiment, all users are initially normal users by default, and only require general level verification. At this time, the server generates 8 different text characters; if the user is verifying, the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com