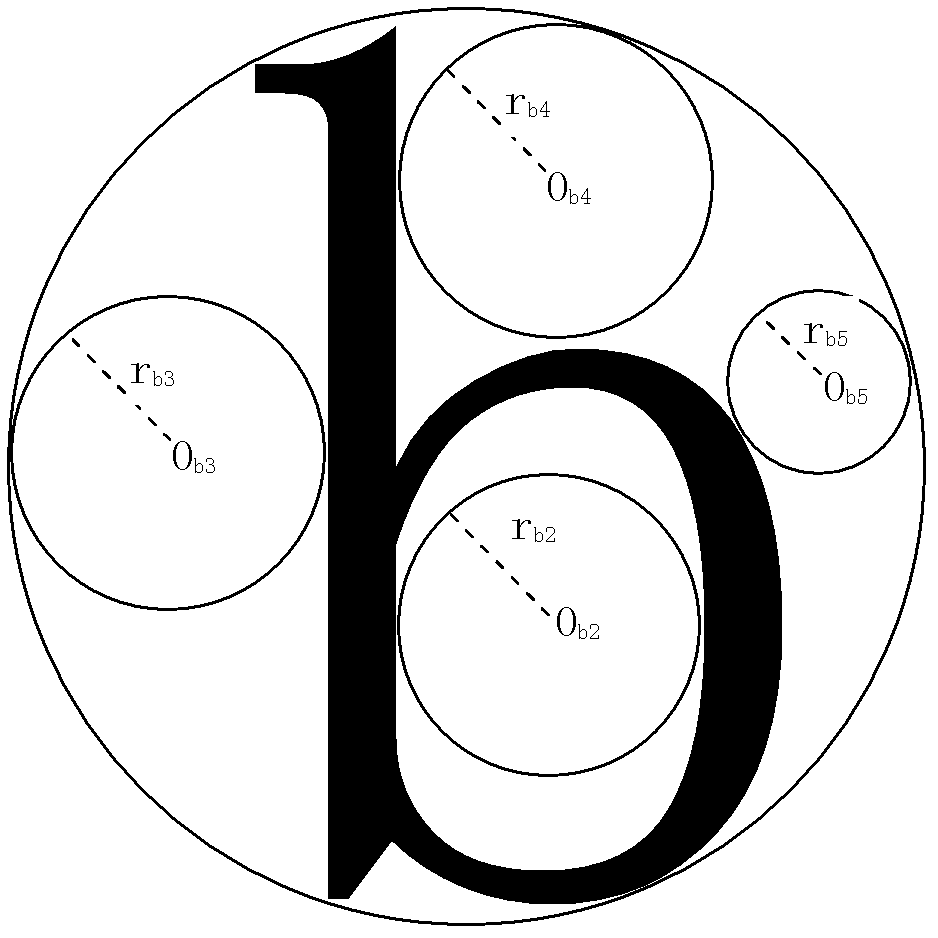Patents
Literature
54results about How to "Increase the difficulty of recognition" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
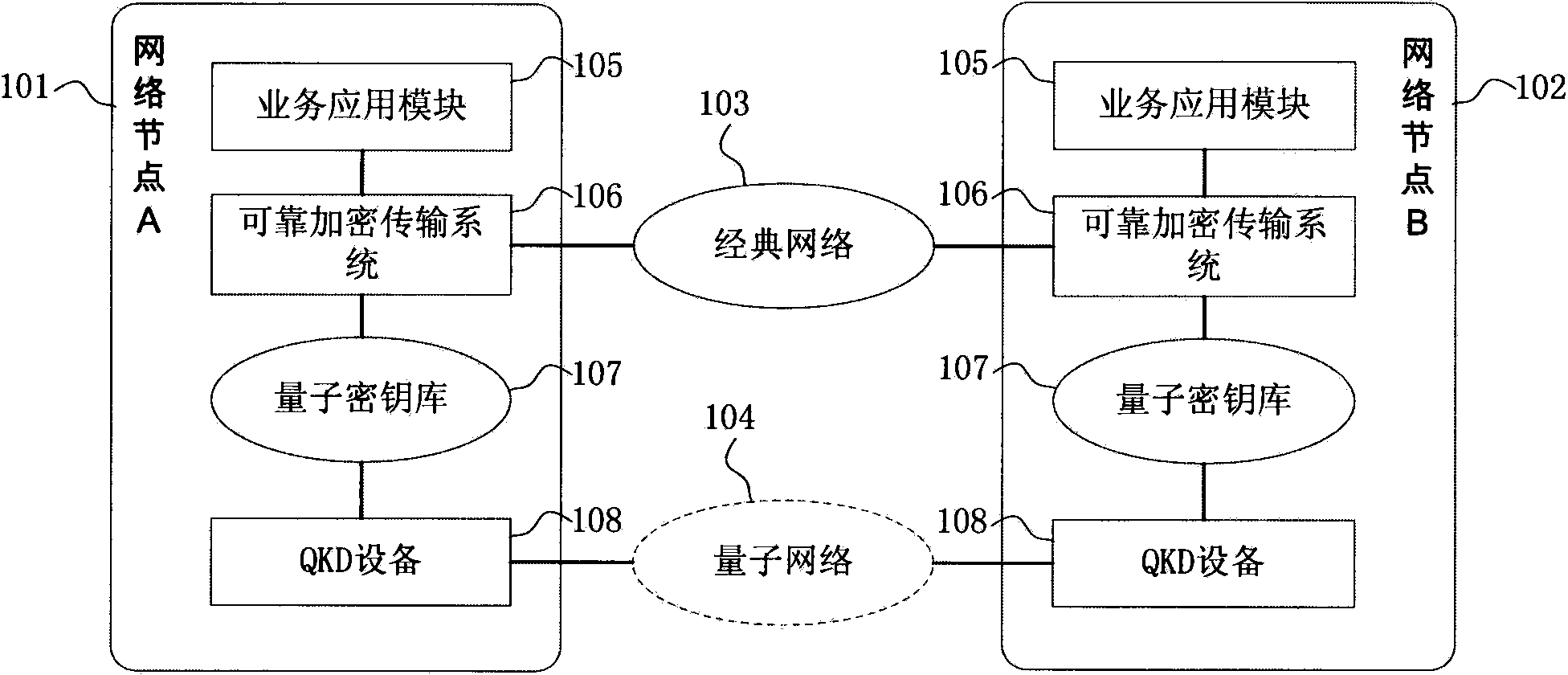
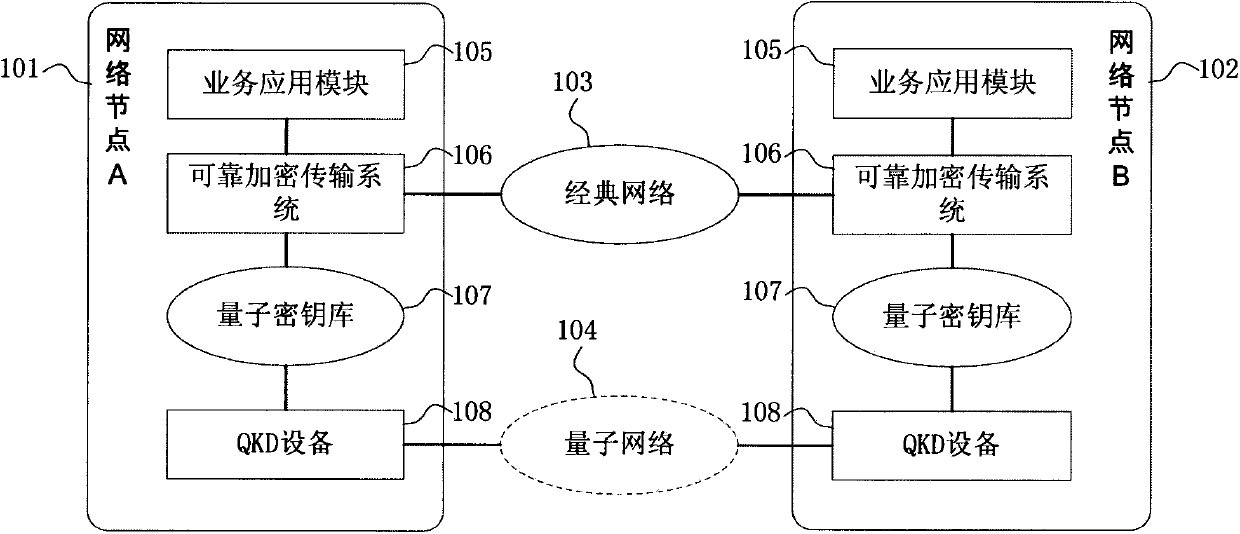
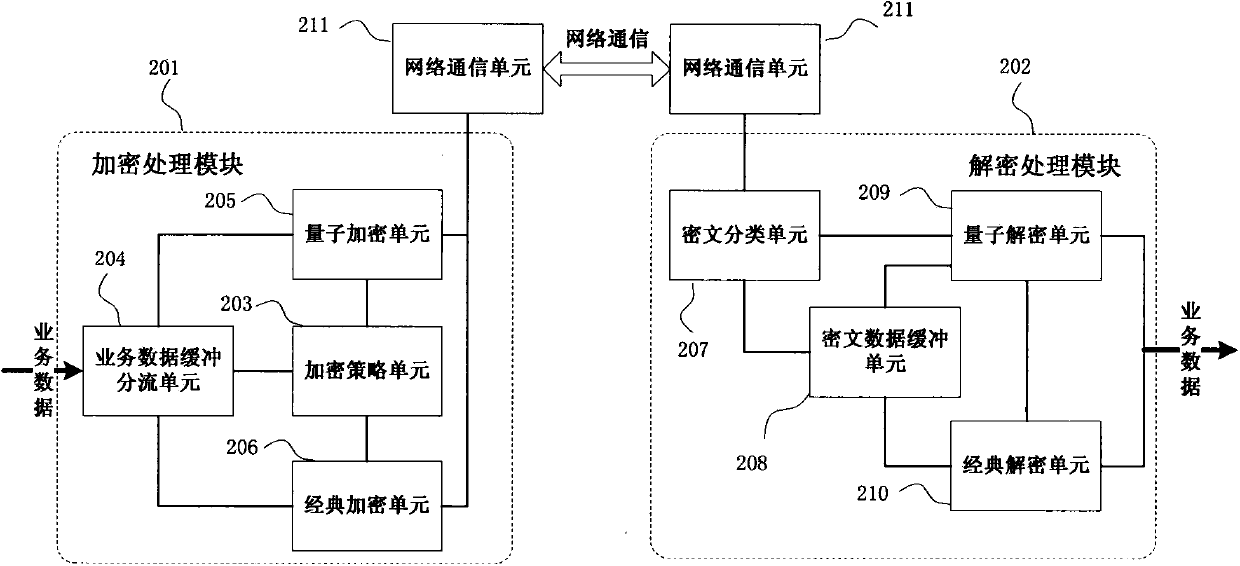
Reliable encryption transmission system and method of quantum cryptography network
ActiveCN103840936AImprove continuityImprove reliabilityKey distribution for secure communicationSynchronising transmission/receiving encryption devicesCiphertextDependability
The invention provides a reliable encryption transmission system of a quantum cryptography network. The reliable encryption transmission system comprises an encryption processing module and a decryption processing module, the encryption processing module is composed of an encryption strategy unit, a service data buffering shunt unit, a classic encryption unit and a quantum encryption unit, and the decryption processing module is composed of a cryptograph classification unit, a cryptograph data buffering unit, a classic decryption unit and a quantum decryption unit. Meanwhile, the invention further provides a reliable encryption transmission method of the quantum cryptography network. The classic encryption mode and the quantum one-time pad encryption mode are adopted for transmitting service data in a shunt mode, the shunt proportion of the service data can be timely and correspondingly changed according to changes of the quantum secret key supply-demand relationship, on the basis that the safety is guaranteed, the continuity of service data encryption transmission is improved, and the reliability of service data encryption transmission is improved. Meanwhile, the consumption of quantum secret key data is reduced, quantum secret key generation loads of the quantum cryptography network are reduced, and the cost of service data encryption transmission of the quantum cryptography network is reduced.
Owner:SHANDONG INST OF QUANTUM SCI & TECH
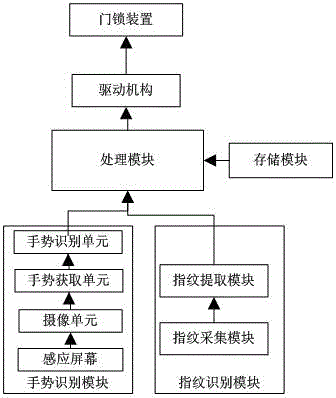
Fingerprint and gesture identification-based door lock control system
InactiveCN104821022ASolve the problem of only unlocking with fingerprint recognitionAdd gesture recognitionCharacter and pattern recognitionIndividual entry/exit registersControl signalControl system
The invention discloses a fingerprint and gesture identification-based door lock control system. The system comprises a processing module, a driving mechanism and a door lock device, and also comprises a memory module, a gesture identification module and a fingerprint identification module, wherein the gesture identification module comprises, sequentially connected, an induction screen, a shooting unit, a gesture acquisition unit and a gesture identification unit; the fingerprint identification module comprises a fingerprint acquisition module and a fingerprint extraction module; the memory module is used for storing initialized set fingerprint image and fingerprint-based gesture image; the fingerprint acquisition module acquires fingerprint, and extracts through the fingerprint extraction module to obtain the fingerprint image; the processing module matches the fingerprint image with the initiated fingerprint image; and a control signal is output to the induction screen when matching is successful to make the induction screen provide an induction platform, the shooting unit is used to monitor the gesture motion on the induction platform, the gesture acquisition unit acquires the gesture motion to obtain the gesture image, the gesture identification unit identifies the gesture image and inputs an identification result to the processing module, and the processing module controls the driving mechanism to unlock according to the identification result. The system based on two identification modes has improved identification function and safety coefficient.
Owner:WUXI CITY CHONGAN DISTRICT TECH ENTREPRENEURSHIP SERVICE CENT
Calibration method and device based on verification code
ActiveCN106899411AConvenient and accurate identificationReduce violationsKey distribution for secure communicationUser identity/authority verificationAlgorithmTime-Consuming
The embodiment of the invention discloses a calibration method and device based on a verification code. The method comprises the following steps: receiving a calibration request, and acquiring a first character string generated in advance after receiving the calibration request, wherein the first character string contains at least one variable character, replacing partial or complete variable characters as a standby character so as to obtain a second character ring according to a pre-established corresponding relation between the variable character and the standby character; generating the verification code according to the second character string, and calibrating the user corresponding to the calibration request. By use of the calibration method disclosed by the embodiment of the invention, the accuracy of distinguishing the verification code by the user can be increased, and the time consuming in the calibration process is reduced; and meanwhile, the recognition difficulty on the verification code by a computer program is increased, and the possibility of executing an illegal operation by the computer program can be effectively lowered.
Owner:ADVANCED NEW TECH CO LTD
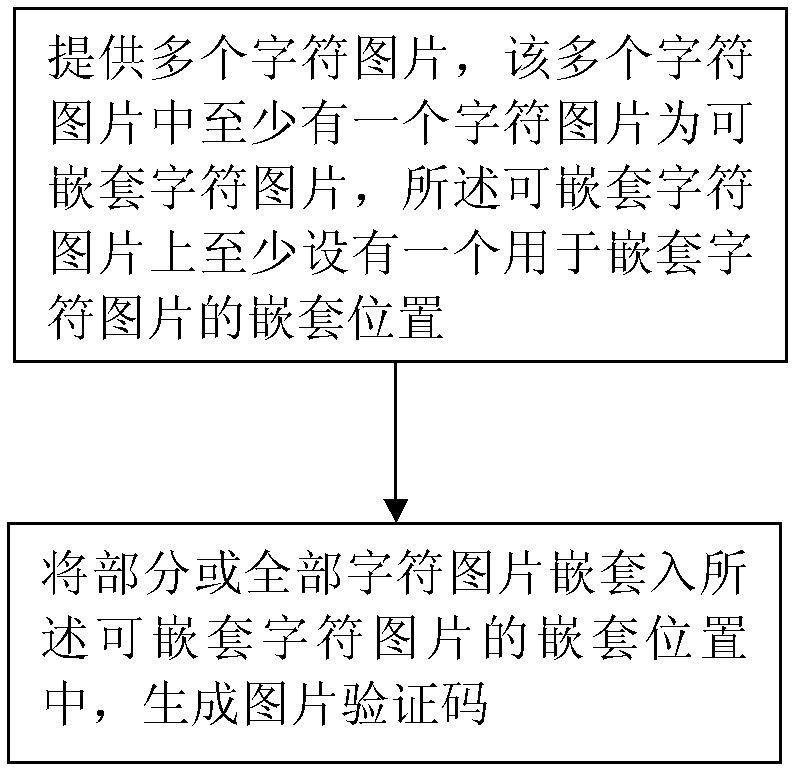
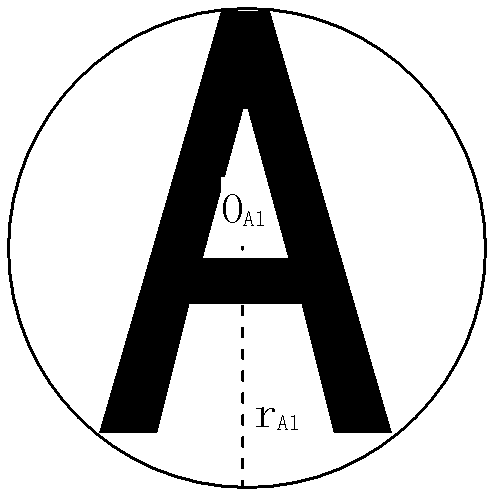
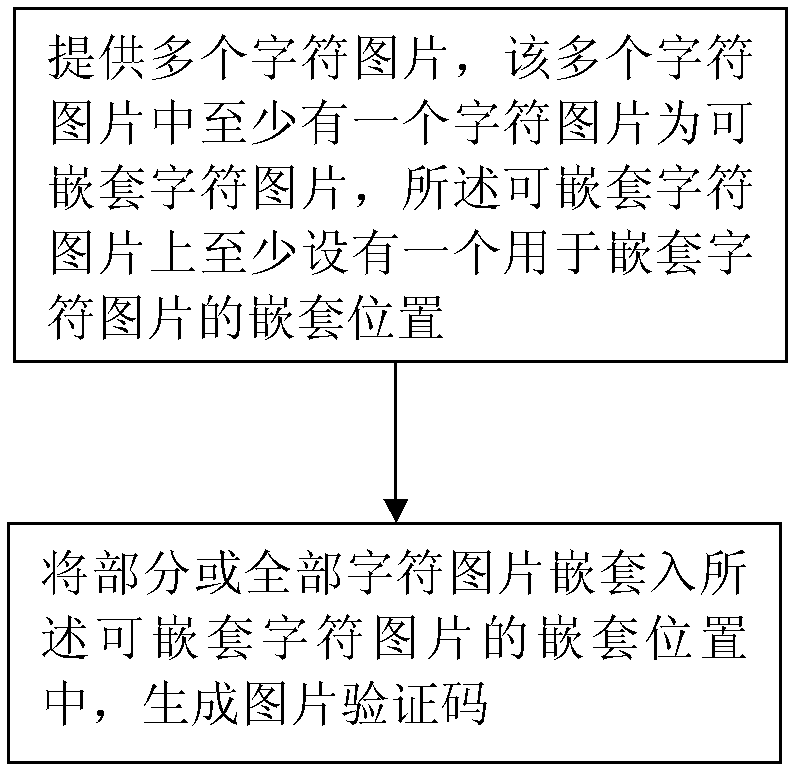
Generation method and generation device of image verification code
ActiveCN103106631AIncrease the difficulty of recognitionDifficulty will not increaseImage data processing detailsPattern recognitionComputer vision
The invention discloses a generation method of an image verification code. According to the generation method of the image verification code, a plurality of character images are provided, at least one of the plurality of character images is a nesting character image, at least one nesting part used for nesting of a nesting character image is arranged on the nesting character image, part or all of the character images are nested in the nesting part on the nesting character image, and then the image verification code is generated. The invention further discloses a generation device of the image verification code. According to the generation method and the generation device of the image verification code, the plurality of character images are arranged in a nesting mode, linear segmentation between each two characters in the image verification code which is generated is difficult, and the generated image verification code is prevented from being recognized easily by computer programs, and difficulty of recognition of the image verification code by a person is not increased.
Owner:ALIBABA GRP HLDG LTD
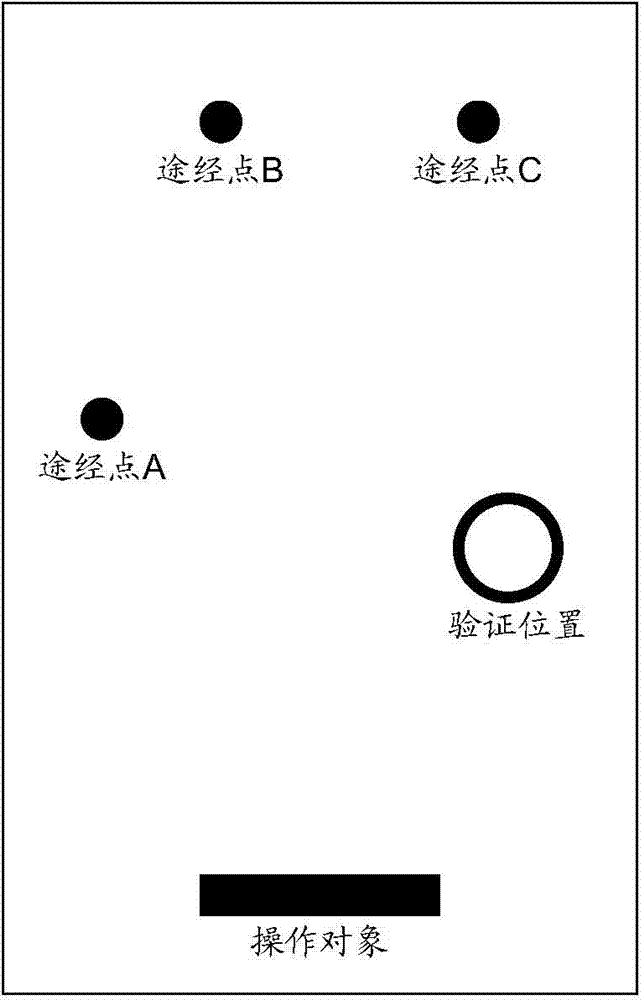
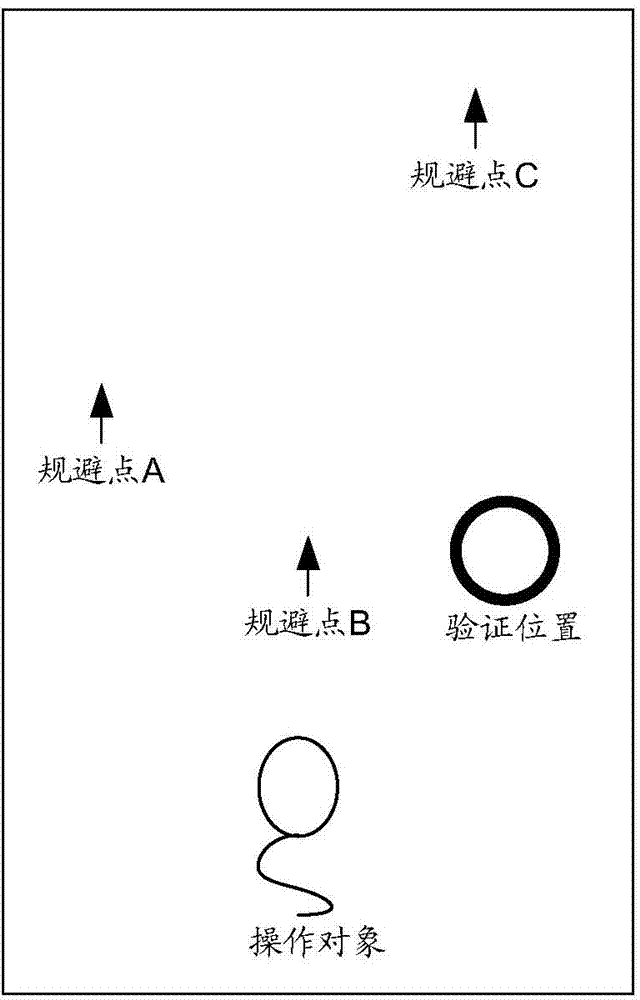
Position-based operation verification method, server, and client
ActiveCN103685231AAvoid operabilityAvoid error-prone problemsUser identity/authority verificationValidation methodsComputer engineering
The invention provides a position-based operation verification method, a server, and a client. On one hand, the method comprises: the server provided by the embodiments of the invention, according to an operation behavior of a user, obtaining a verification position, an operation object and a movable trend, and sending to the client display indication information and the movable trend, wherein the display indication information is used for instructing the client to display the verification position and the operation object; the server receiving a final position of the operation object, which is sent by the client, wherein the final position is obtained by the client through moving the operation object on a path corresponding to the movable trend according to a direction instruction; and if the final position is consistent with the verification position, the server executing successfully verified operation of the client. By using the method, server and the client, provided by the invention, the problems of inconvenient operation of inputting verification information by an input device and easily occurred errors in the prior art can be avoided, thus operation verification efficiency and reliability are improved.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
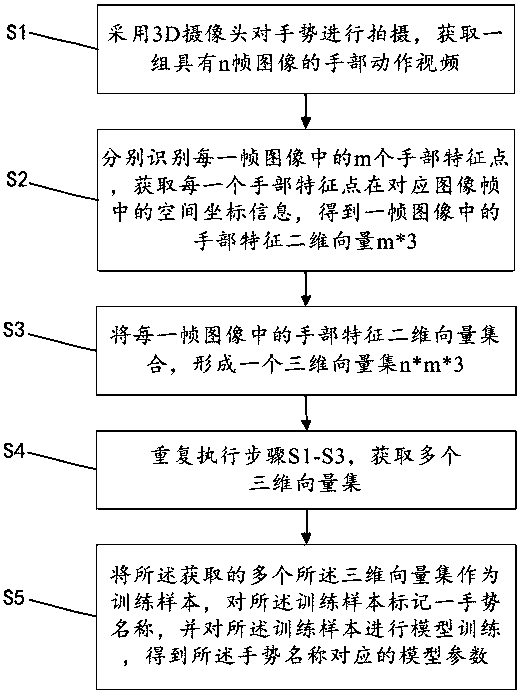
Method and system for dynamic gesture recognition
PendingCN109117766AIncrease the difficulty of recognitionImprove recognition accuracyCharacter and pattern recognitionNeural architecturesModel parametersHand motion
The invention discloses a dynamic gesture recognition method. The method comprises the following steps: shooting the gesture by a 3D camera to obtain a group of hand motion videos with n frames of images; identifying m hand feature points in each frame image respectively, obtaining spatial coordinate information of each hand feature point in the corresponding image frame, and obtaining a two-dimensional vector m*3 of hand feature in one frame image; forming a three-dimensional vector set n*m*3 from a two-dimensional vector set of hand features in each frame image; steps S1-S3 are repeated, acquiring a plurality of three-dimensional vector sets; The obtained plurality of the three-dimensional vector sets are used as training samples, a gesture name is marked on the training samples, and model training is performed on the training samples to obtain model parameters corresponding to the gesture names, so that dynamic gesture recognition can be performed with high accuracy.
Owner:杭州吉吉知识产权运营有限公司
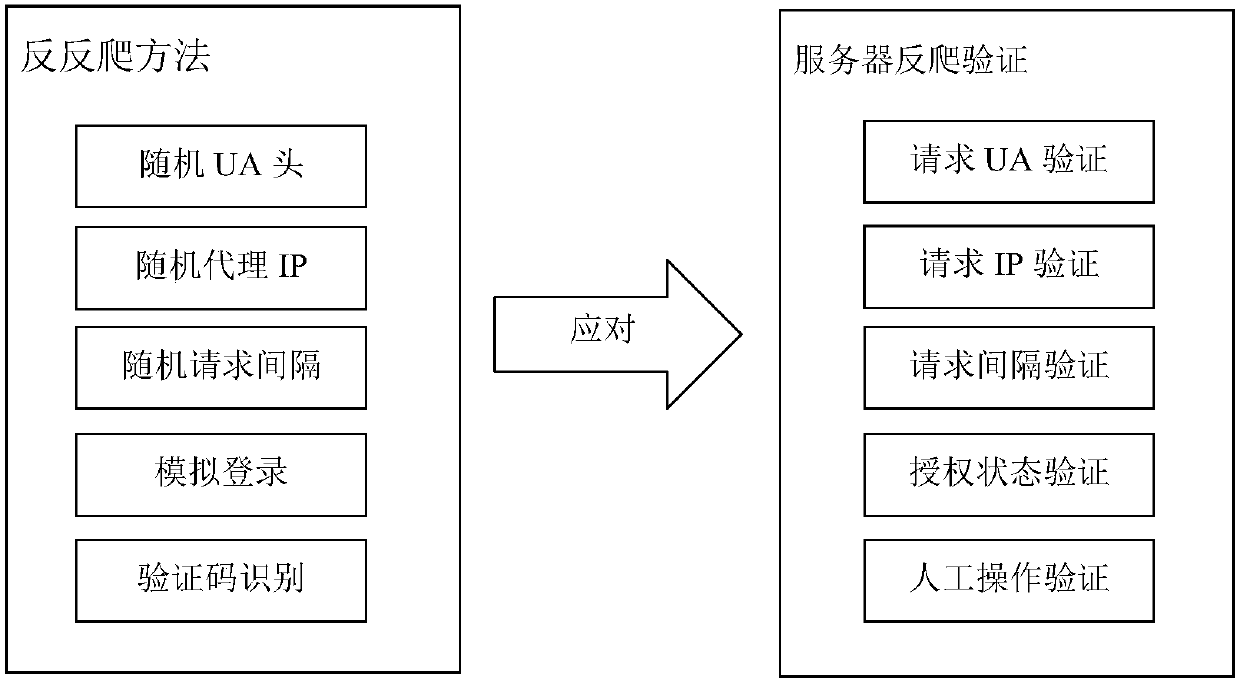
A universal internet data acquisition anti-reverse crawling system and method
The invention discloses a universal internet data acquisition anti-reverse crawling method and system. The method comprises the following steps: a UA verification unit (01) provides a random UA headerto a server through; a random agent IP is provided for the server through an IP verification unit (02); An interval verification unit (03) has a random request interval according to the specification. the login is simulated through an authorization state verification unit (04); and the verification code is identified through a verification code identification unit (05) or Or through the above combination to separately respond to the request UA verification, request IP verification, request interval verification, authorization status verification, manual operation verification, or a combination thereof in the Internet anti-climbing verification,and the method can bypass interception of various anti-crawling verification means combinations , and achieve effective acquisition of the websiteinformation.
Owner:北京宸瑞科技股份有限公司
Wiring method for reinforcing protection on important region of metal protection layer at top layer of chip
InactiveCN109585419AIncrease the difficulty of recognitionIncrease the difficultySemiconductor/solid-state device detailsSolid-state devicesEngineeringInformation security
The invention relates to the field of chip technology and information safety. By the method, the wiring density of a metal wire at a top layer can be improved, the failure area of a shielding line ata key region is reduced, the difficulty on circuit analysis by an attacker is improved, the purpose of important protection on the key region of the chip is achieved, the attacker can be effectively prevented from acquiring internal data of the chip by attack means such as shooting analysis reverse engineering and FIB, and a safety coefficient of the key region of the chip is improved. The wiringmethod for reinforcing protection on the important region of the metal protection layer at the top layer of the chip, disclosed by the technical scheme comprises the steps of firstly, planning wiringregion area and a protection level of each region according to the size of the chip, and dividing a metal shielding layer at the top layer into several wiring regions; and secondly, wiring and fillingeach wiring unit according to a safety coefficient of the wiring region, wherein the wiring number of each region is gradually increased according to the safety level. The method is mainly applied toa chip design and manufacturing occasion.
Owner:TIANJIN UNIV
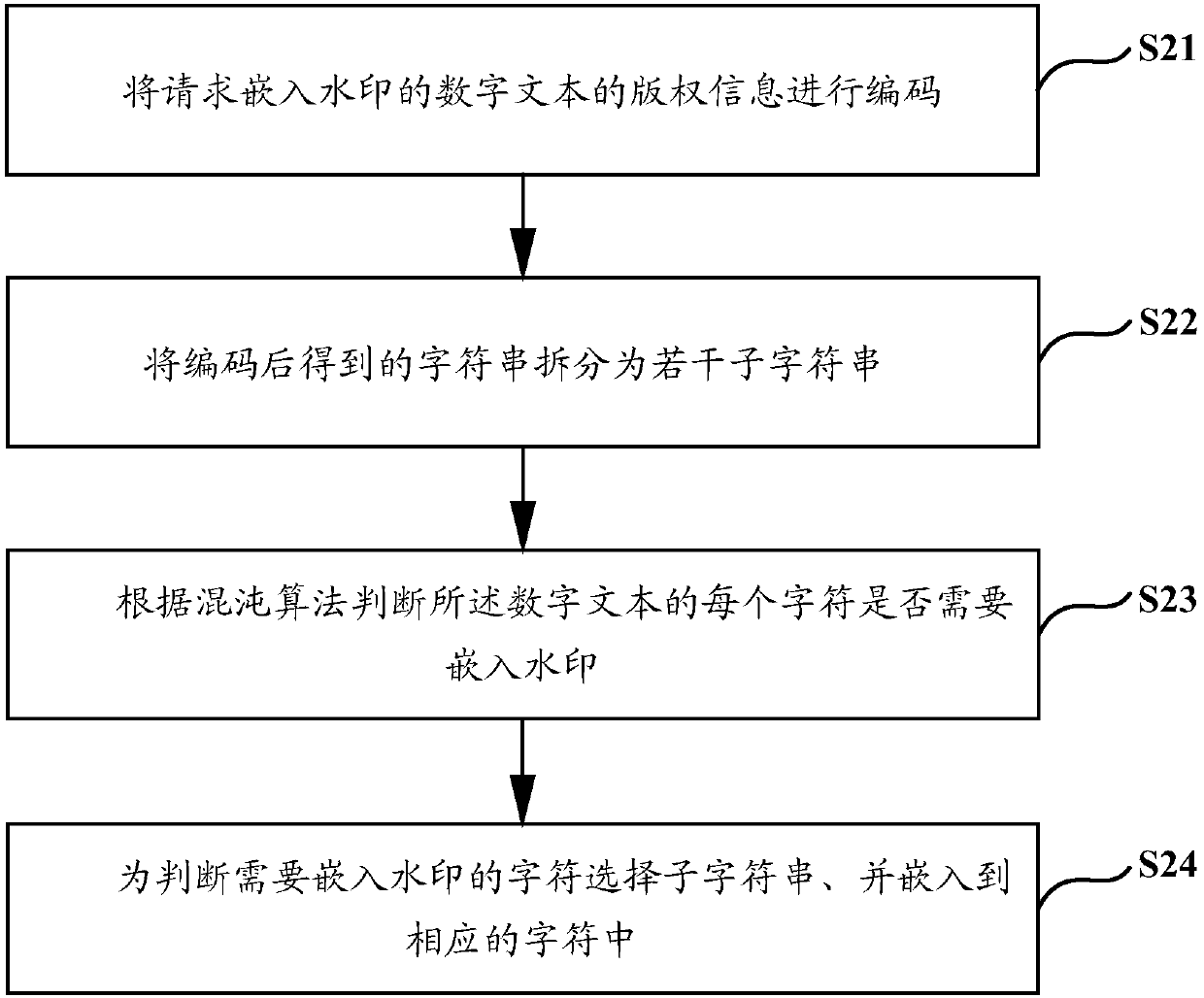
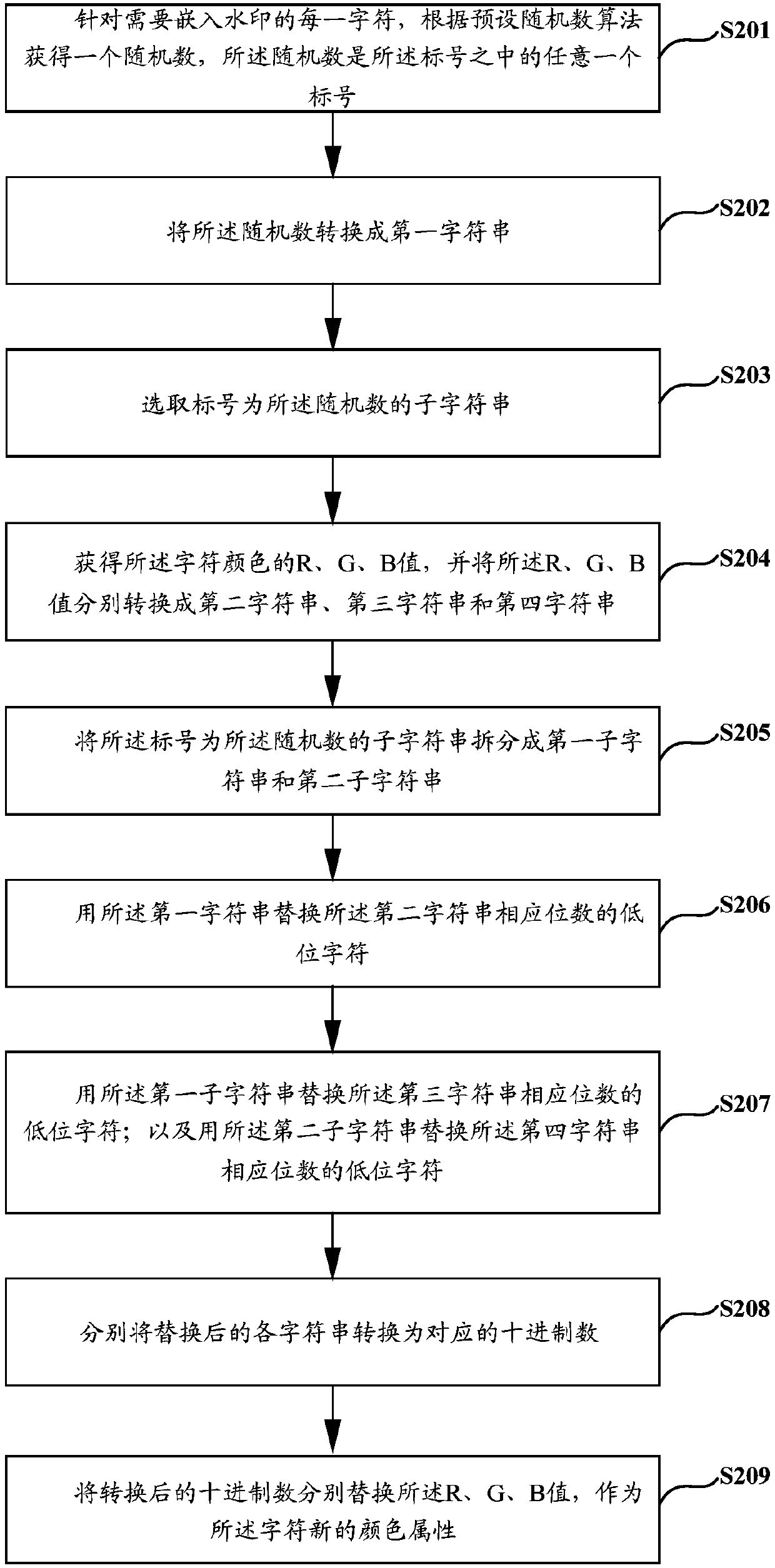
Digital text watermark embedding and detecting method and device
PendingCN110322386AImprove privacyPrevent tamperingImage data processing detailsComputer scienceDigital text
The invention discloses a digital text watermark embedding and detecting method and device, solves the problem that watermark information of an existing digital text watermark embedding method is easily tampered, and improves the effectiveness of digital copyright protection. The digital text watermark embedding method comprises: encoding copyright information of a digital text requesting watermark embedding, and the copyright information being used for representing sending end attribute information of the digital text; splitting a character string obtained after encoding into a plurality of sub-character strings; judging whether each character of the digital text needs to be embedded with a watermark or not according to a chaos algorithm; and selecting a sub-character string for judging the character which needs to be embedded with the watermark, and embedding the sub-character string into the corresponding character.
Owner:CHINA MOBILE SUZHOU SOFTWARE TECH CO LTD +1
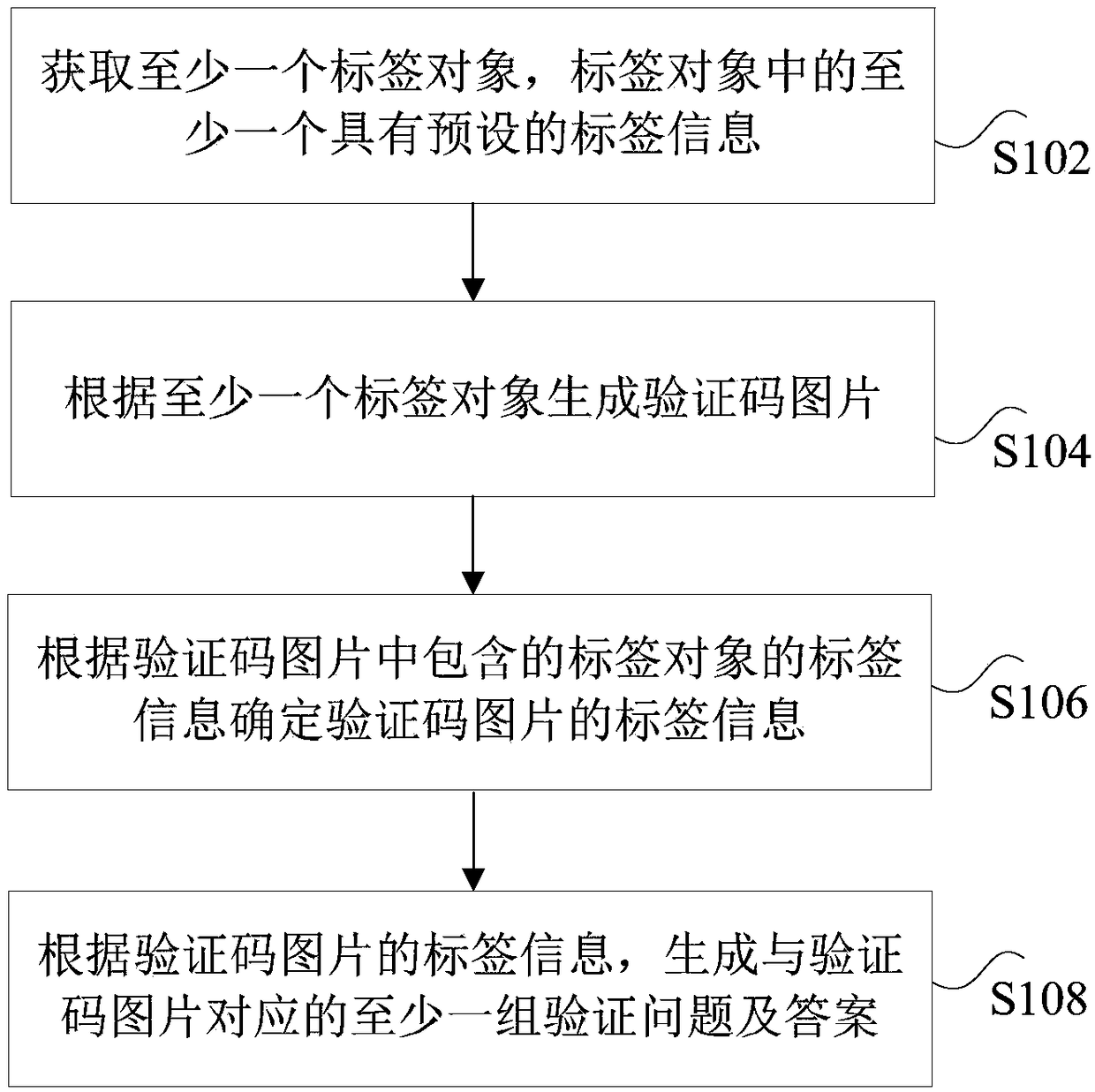
Method and device, storage medium, processor and terminal for generating verification code
ActiveCN108159700AIncrease the difficulty of recognitionDigital data authenticationVideo gamesComputer hardwareMachine recognition
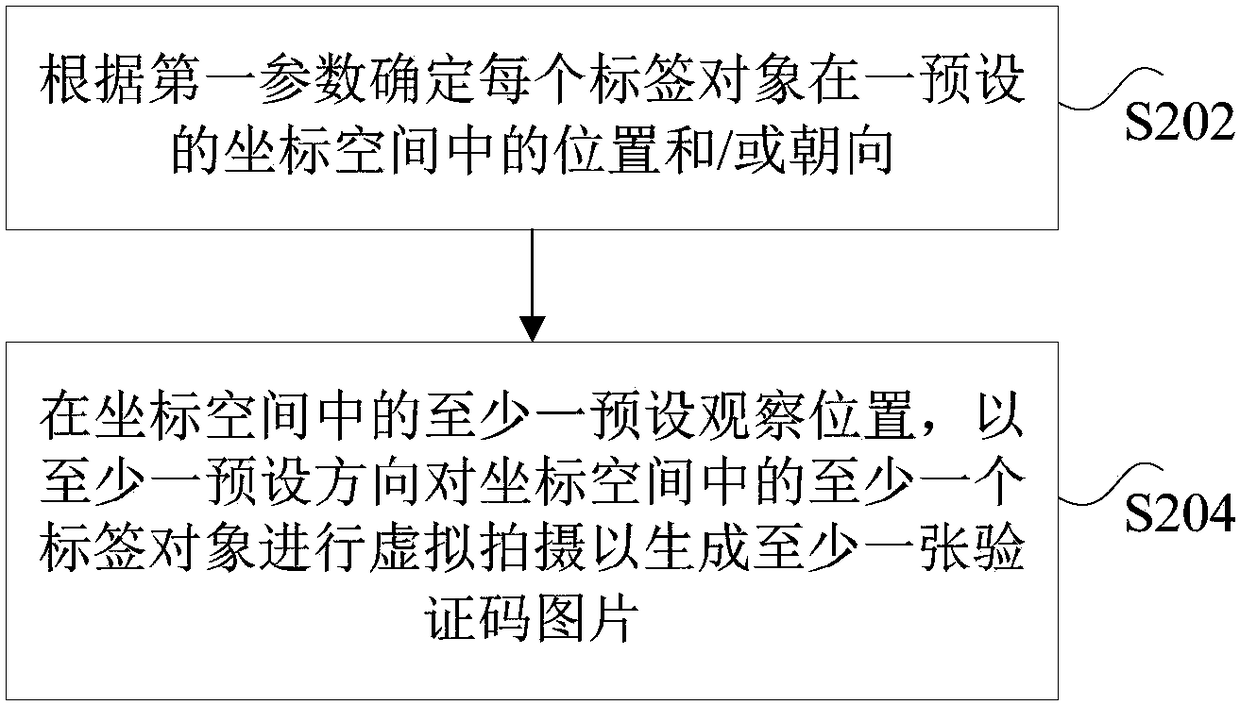
The invention discloses a method and device, a storage medium, a processor and a terminal for generating a verification code. The method comprises the steps that at least one tag object is obtained, at least one tag object has preset tag information; according to the at least one tag object, a verification code picture is generated; according to the tag information of the tag object contained in the verification code picture, the tag information of the verification code picture is determined; according to the tag information of the verification code picture, at least one set of questions and answers corresponding to the verification code picture is generated. The method and device, storage medium, processor and terminal for generating the verification code solve the technical problem in the prior art that the implementation of a verification code scheme by using a dot or puzzle scheme needs a large number of databases and is easy to be solved by a machine recognition technology.
Owner:NETEASE (HANGZHOU) NETWORK CO LTD
Picture detection method and device, storage medium and electronic device
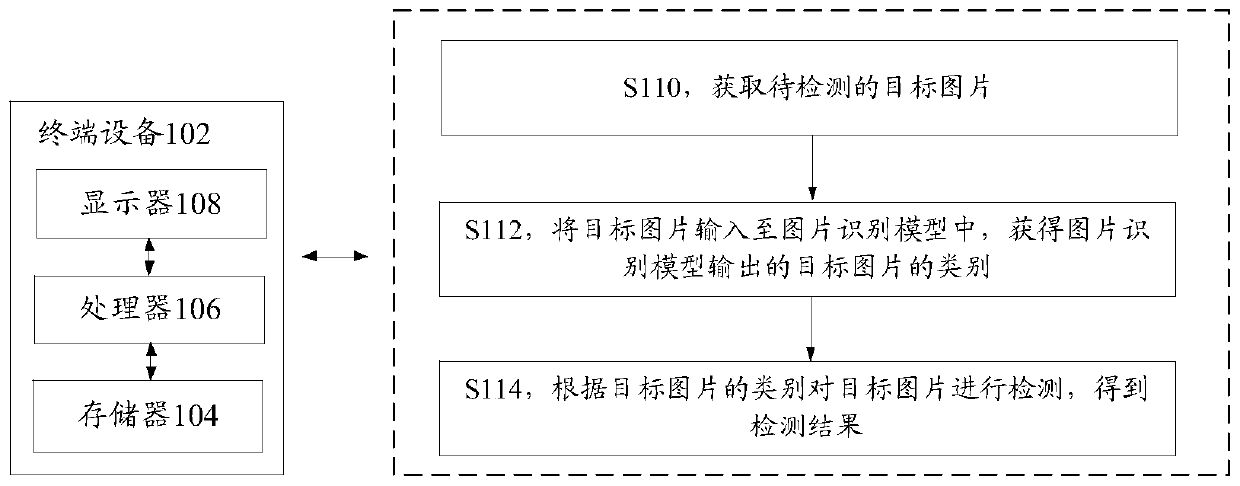
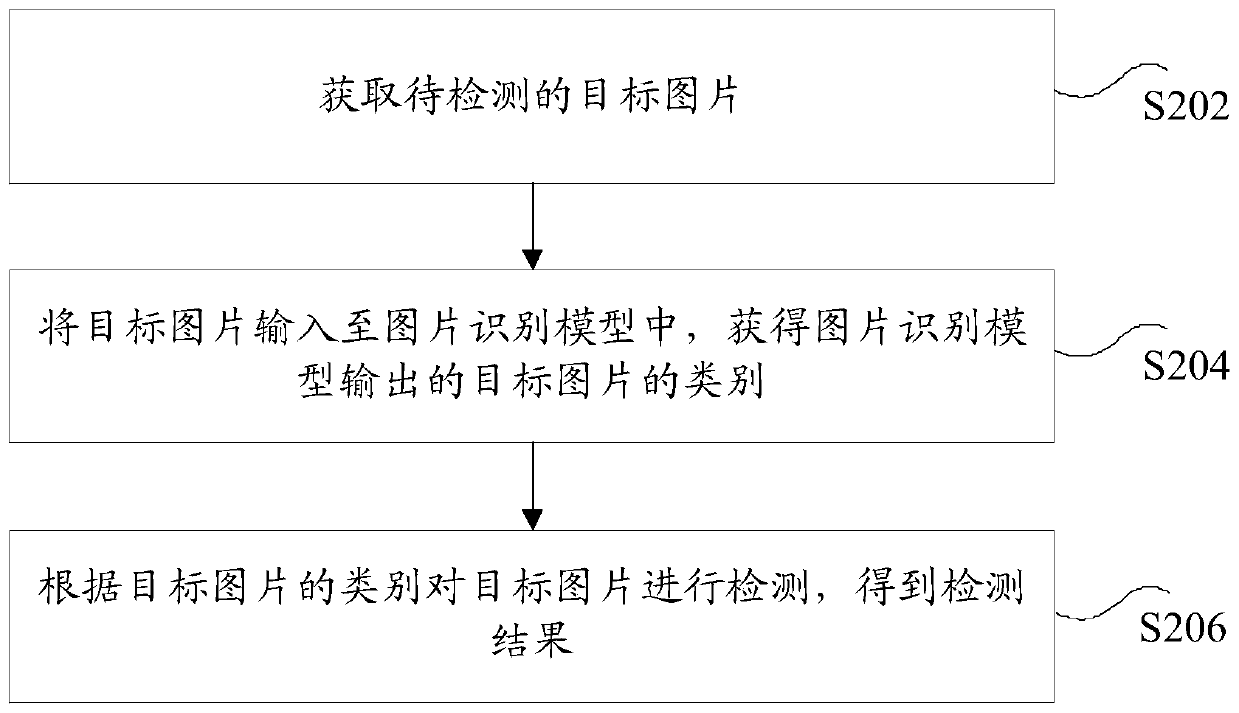
ActiveCN110414581AIncrease the difficulty of recognitionImprove recognition accuracyCharacter and pattern recognitionMachine learningSample imagePicture recognition
The invention discloses a picture detection method and device, a storage medium and an electronic device. The method comprises the steps of obtaining a to-be-detected target picture; inputting the target picture into a picture recognition model to obtain the category of the target picture output by the picture recognition model, with the picture recognition model being a model obtained by using sample pictures in a plurality of first sample picture sets to perform multiple rounds of training on the initial picture recognition model; and detecting the target picture according to the category ofthe target picture to obtain a detection result, the detection result being used for indicating whether the target picture is an abnormal picture. According to the invention, the technical problem oflow accuracy of detection through a picture recognition model is solved. According to the picture detection method provided by the embodiment of the invention, the picture recognition model is obtained by training through a machine learning method, so that the picture category is recognized.
Owner:TENCENT TECH (SHENZHEN) CO LTD
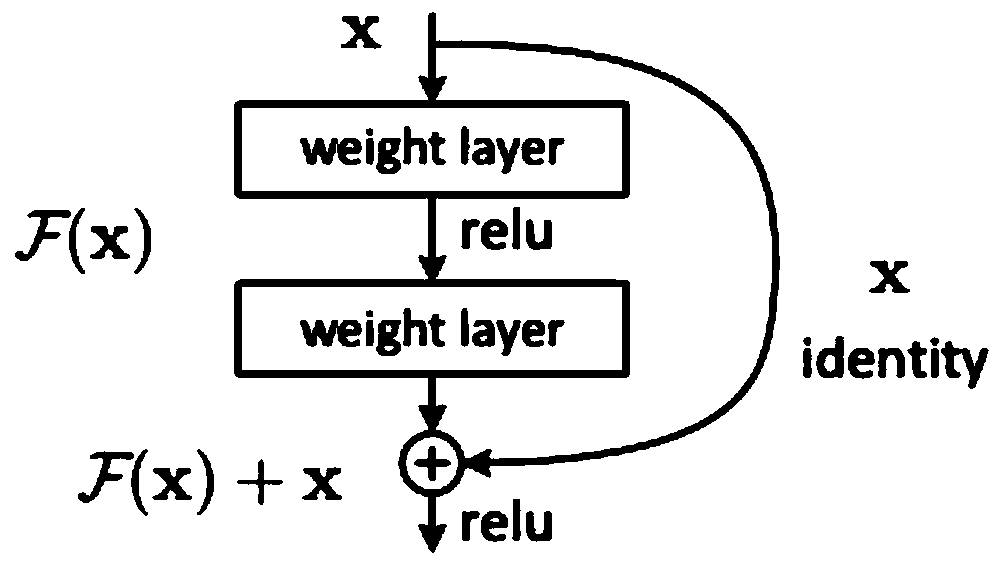
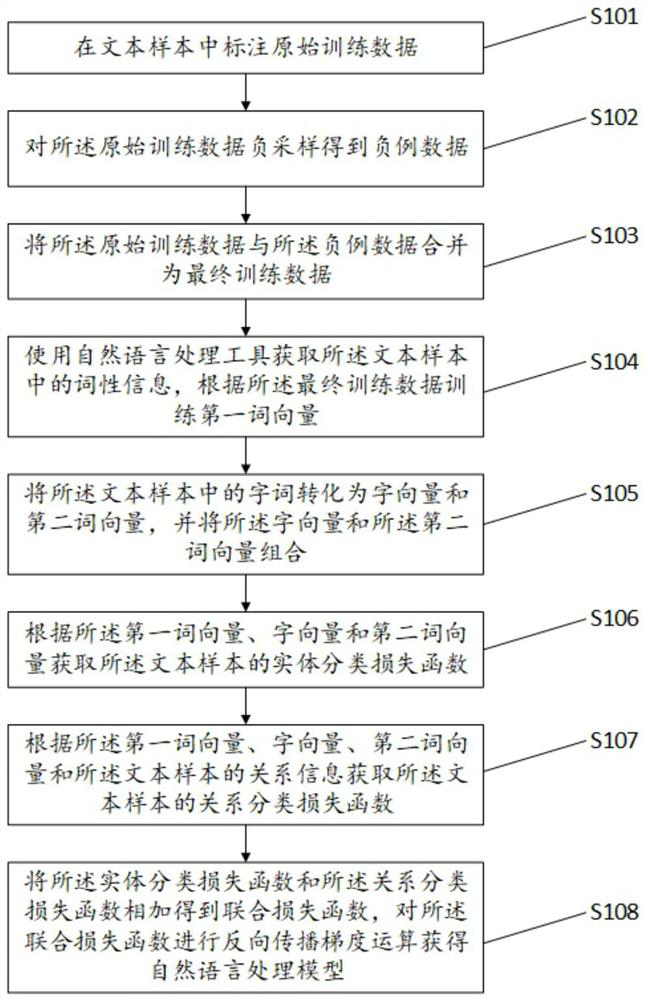
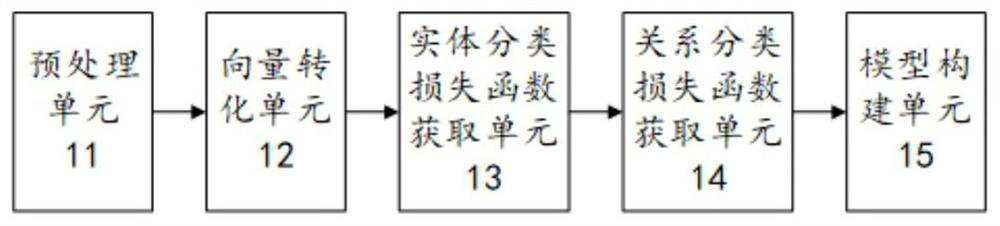
Natural language processing model construction method and system, electronic equipment and storage medium
PendingCN112232070AReduce error accumulationEasy to deployNatural language data processingNatural languageData science
The invention provides a natural language processing model construction method and system, electronic equipment and a storage medium, and the technical scheme of the method comprises the steps: carrying out the information extraction through employing a combined extraction method, and mining the information of different granularities, including a word vector and a character vector corresponding topart-of-speech information; besides, negative sampling is performed on the original training data so that a batch of negative samples are obtained, the problem of low resources of the model can be solved and the identification difficulty of the model can be enhanced. According to the method, the implementation effect of unstructured text information extraction is improved, and the robustness of the model is improved.
Owner:BEIJING XUEZHITU NETWORK TECH
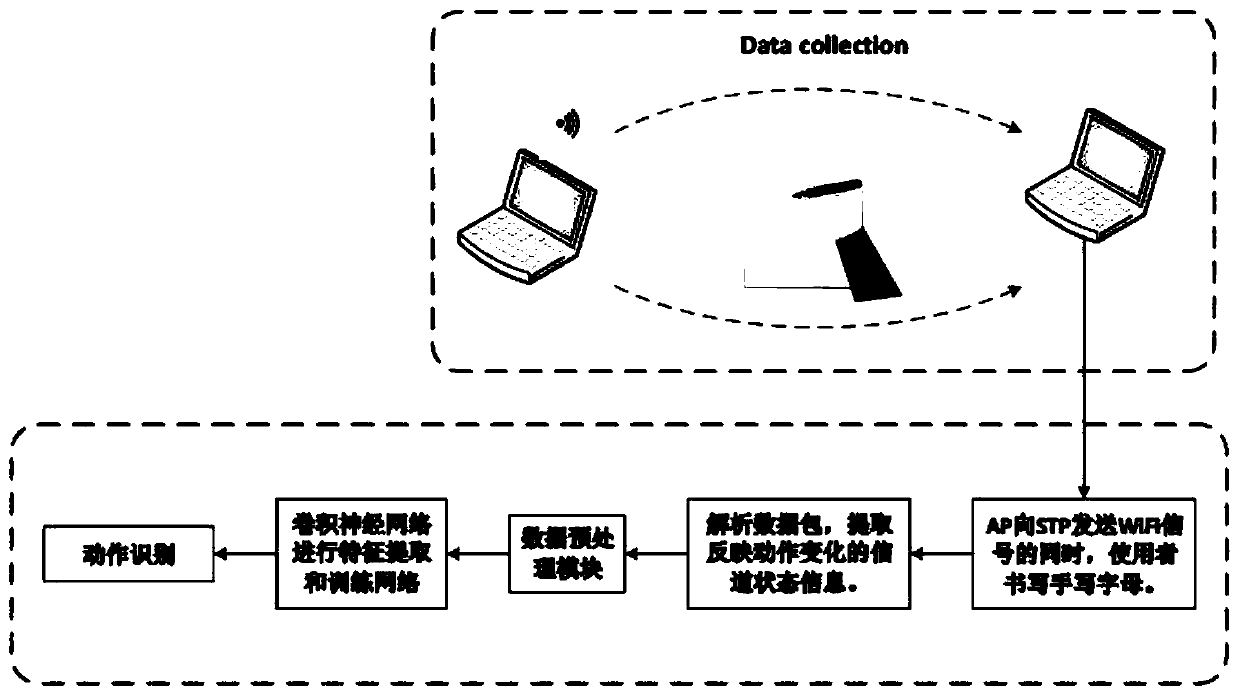
Handwritten letter recognizing method and system based on WiFi
InactiveCN110353693AAccurate identificationLower requirementDiagnostic recording/measuringSensorsChannel state informationAlgorithm
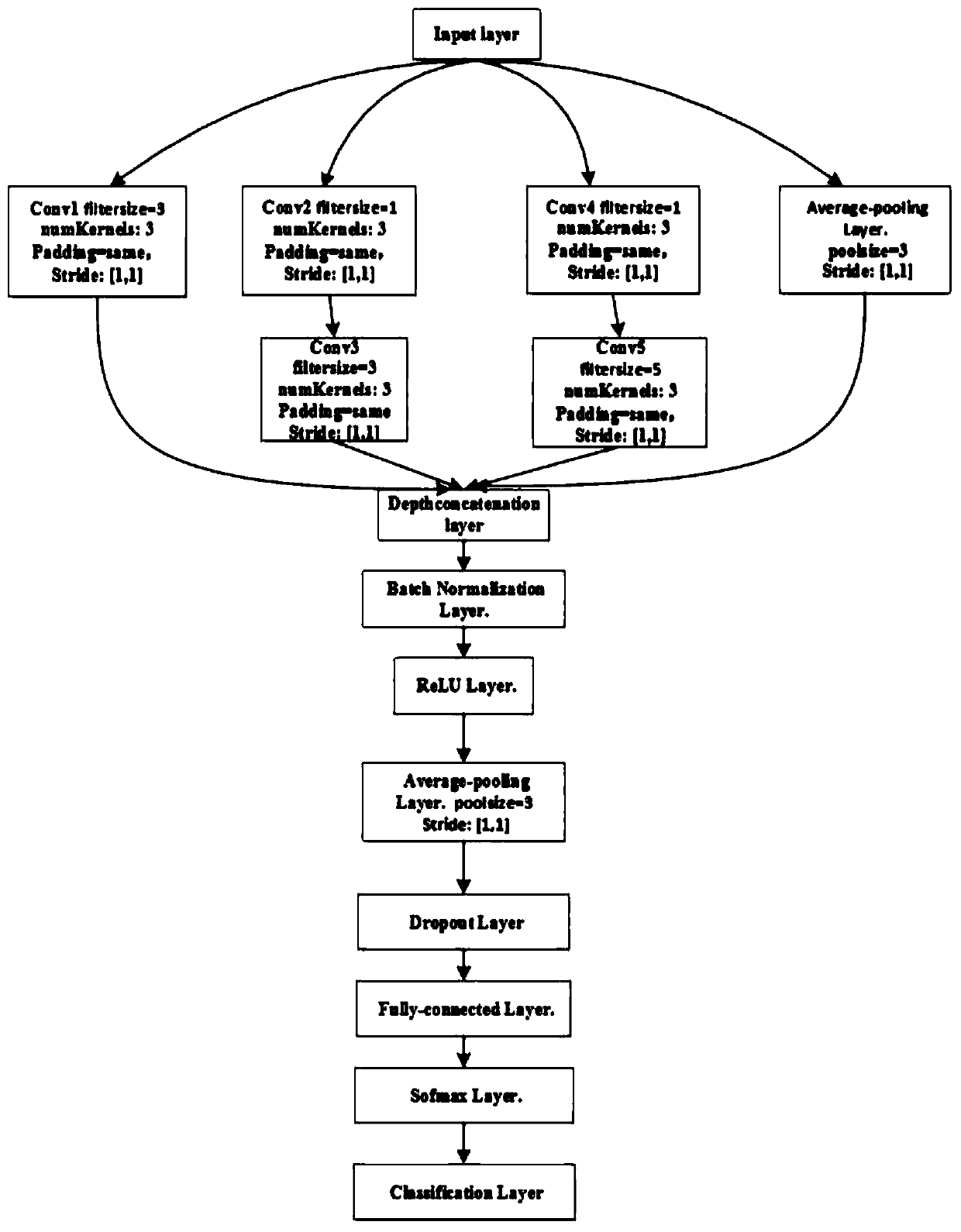
The invention discloses a handwritten letter recognizing method and system based on WiFi. The method includes the following steps of A1, collecting WiFi signals for reflecting environment state changes through a data collecting module when a user writes handwritten letters between an AP and an STP; A2, extracting channel state information from the WiFi signals; A3, conducting phase unwinding and phase correcting operations on the channel state information; A4, inputting data into a convolutional neural network, wherein the convolutional neural network comprises an input layer, an Inception module, a depth connecting layer, a batch standardization layer, a ReLU layer, an average pooling layer, a dropout layer, a full-connection layer, a softmax layer and a classification layer, and the network is trained through a momentum gradient descending method; A5, applying a trained convolutional neural network model to handwritten letter recognizing. The limitation that a wearable device needs to be carried during traditional action recognition and the risk of privacy leakage are overcome. Action recognition is conducted by means of the improved convolutional neural network, and the recognizing precision is improved.
Owner:CHINA UNIV OF PETROLEUM (EAST CHINA)
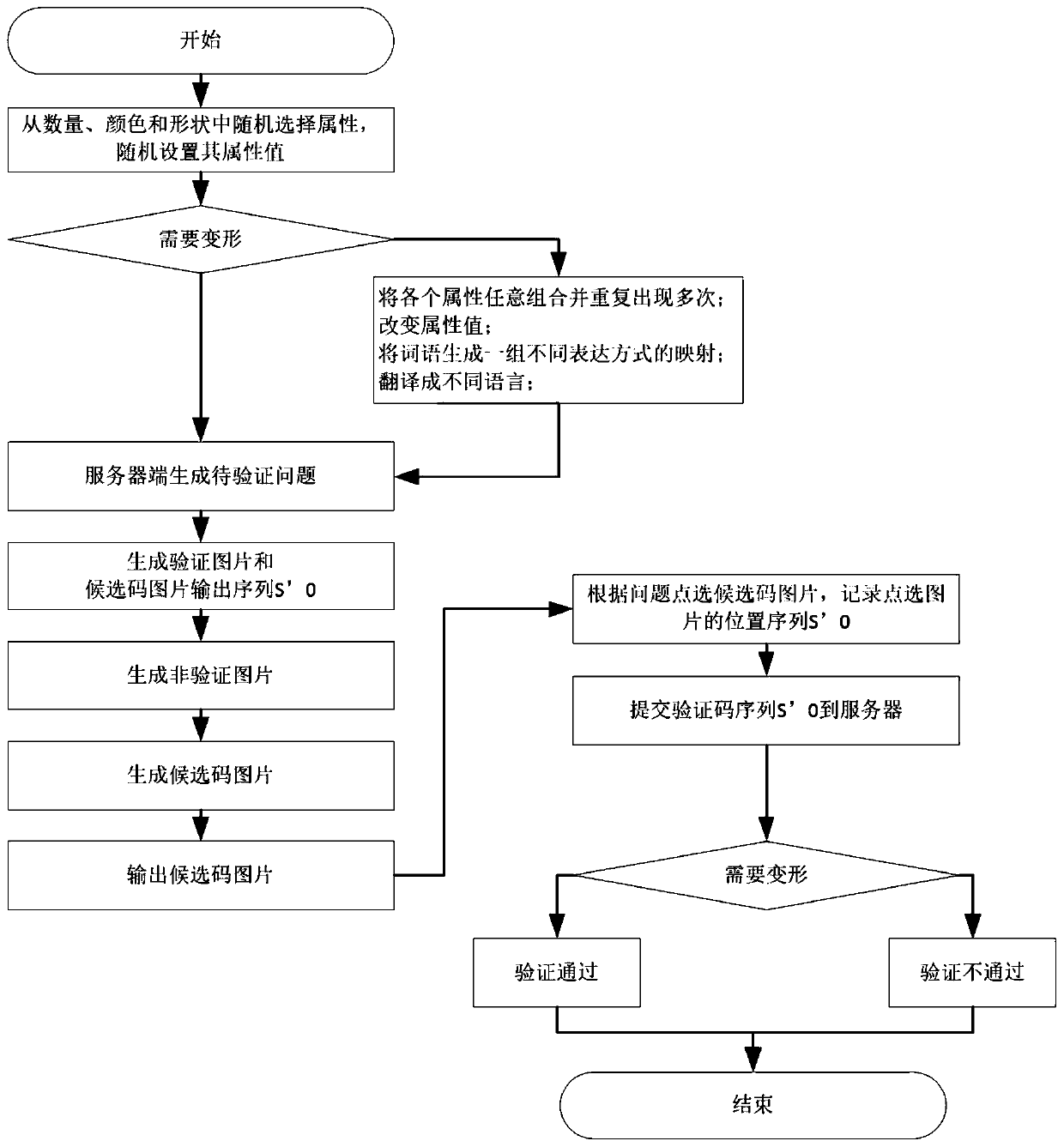
Interactive picture verification method based on semantic comprehension
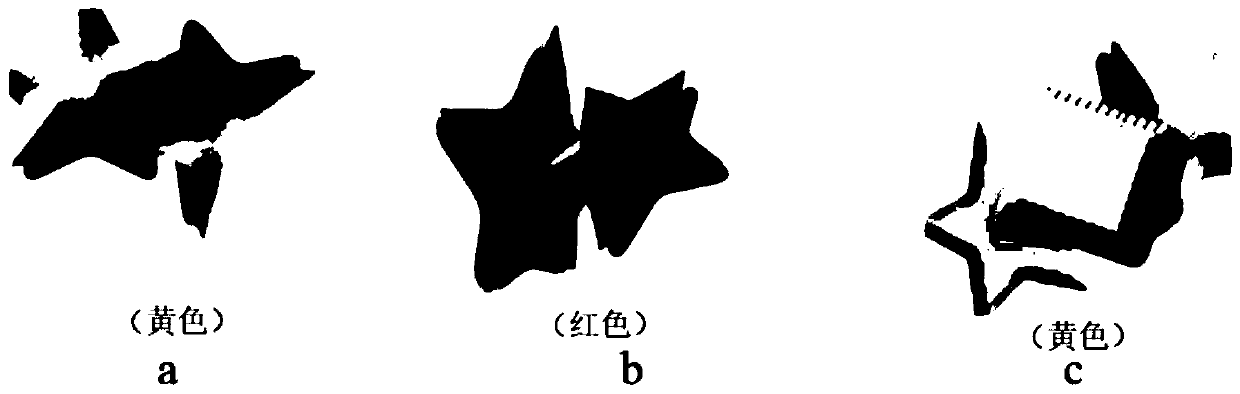
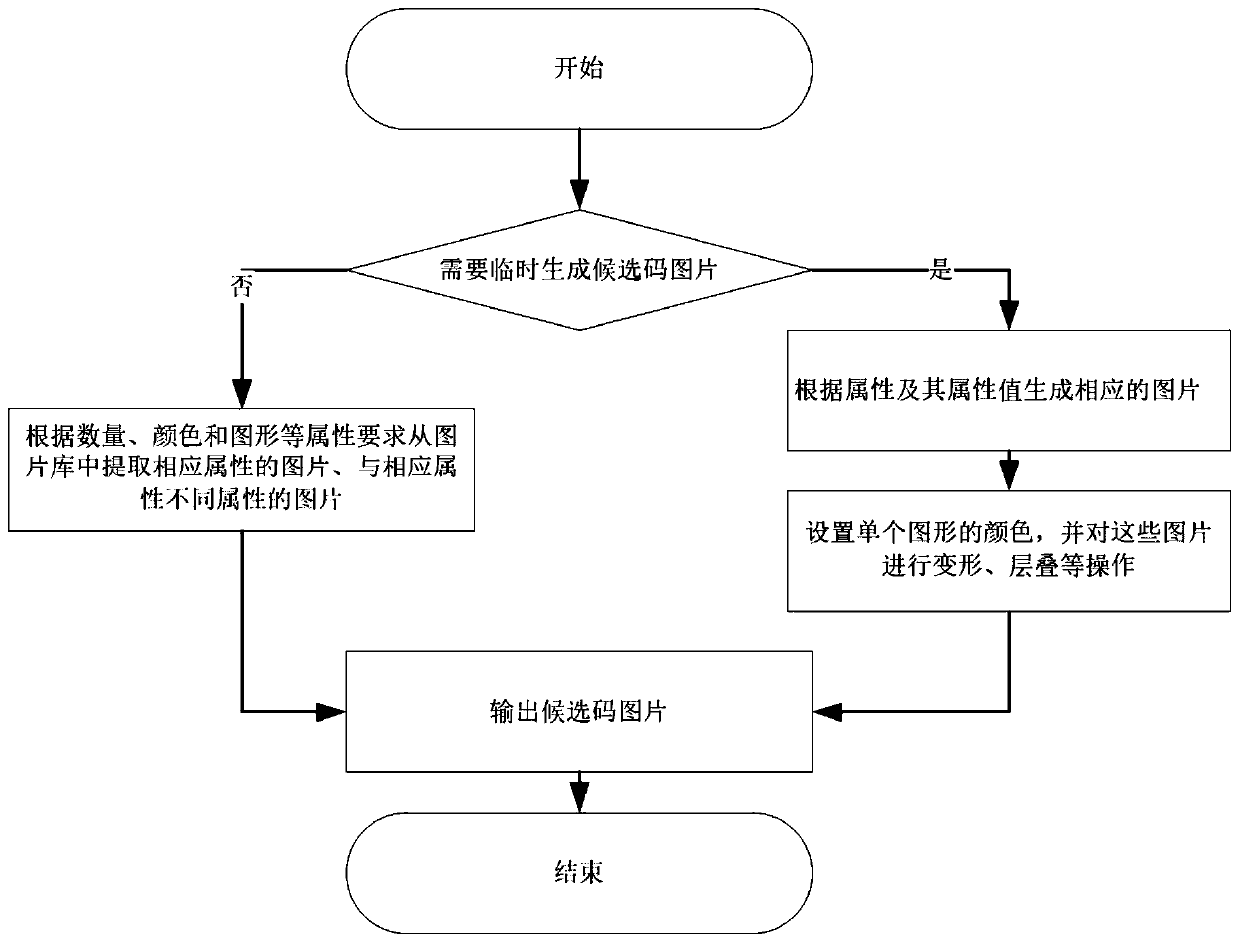
ActiveCN111523105APrevent automatic identificationEasy to operateDigital data authenticationVerification problemAlgorithm
The invention belongs to the technical field of network verification, and discloses an interactive picture verification method based on semantic comprehension, which comprises the following steps: 1)generating a to-be-verified problem: randomly selecting a plurality of attributes from a basic attribute library for generating the to-be-verified problem, and randomly setting attribute values of theattributes; generating a to-be-verified problem according to the selected attribute and attribute value; 2) generating a specified number of verification pictures according to attributes and attribute values corresponding to the to-be-verified problem, generating a verification picture output sequence, generating non-verification pictures, and forming candidate code pictures according to the verification picture output sequence; 3) displaying the to-be-verified problem and the candidate code picture; 4) receiving pictures clicked by the user in the candidate code pictures, and recording a position sequence of the clicked pictures; and 5) comparing the position sequences of the verification picture output sequence and the click picture, if the position sequences are the same, the verification is passed, If the position sequences are different, the verification is not passed. The to-be-verified problem and the candidate code picture generated by the method are easy to identify and operate by a user, but are not easy to automatically identify by a machine.
Owner:闽南科技学院
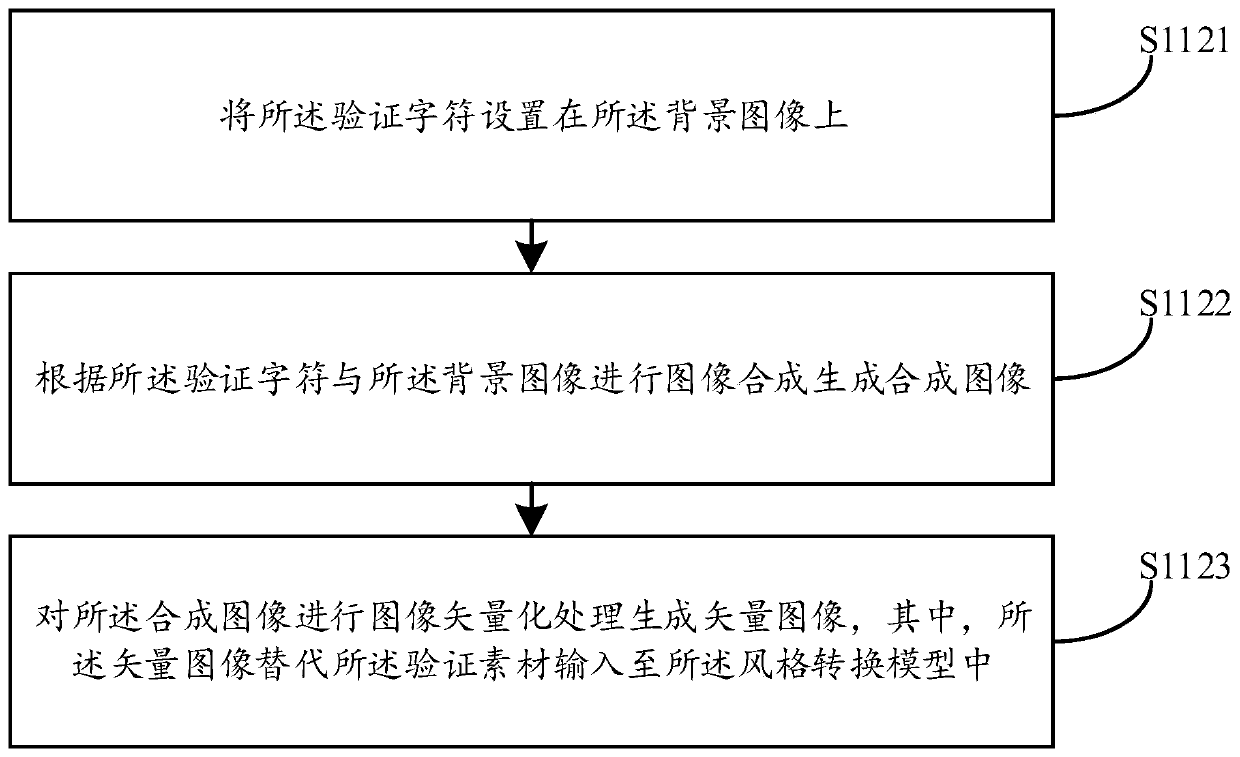
Character verification method and device, computer equipment and storage medium
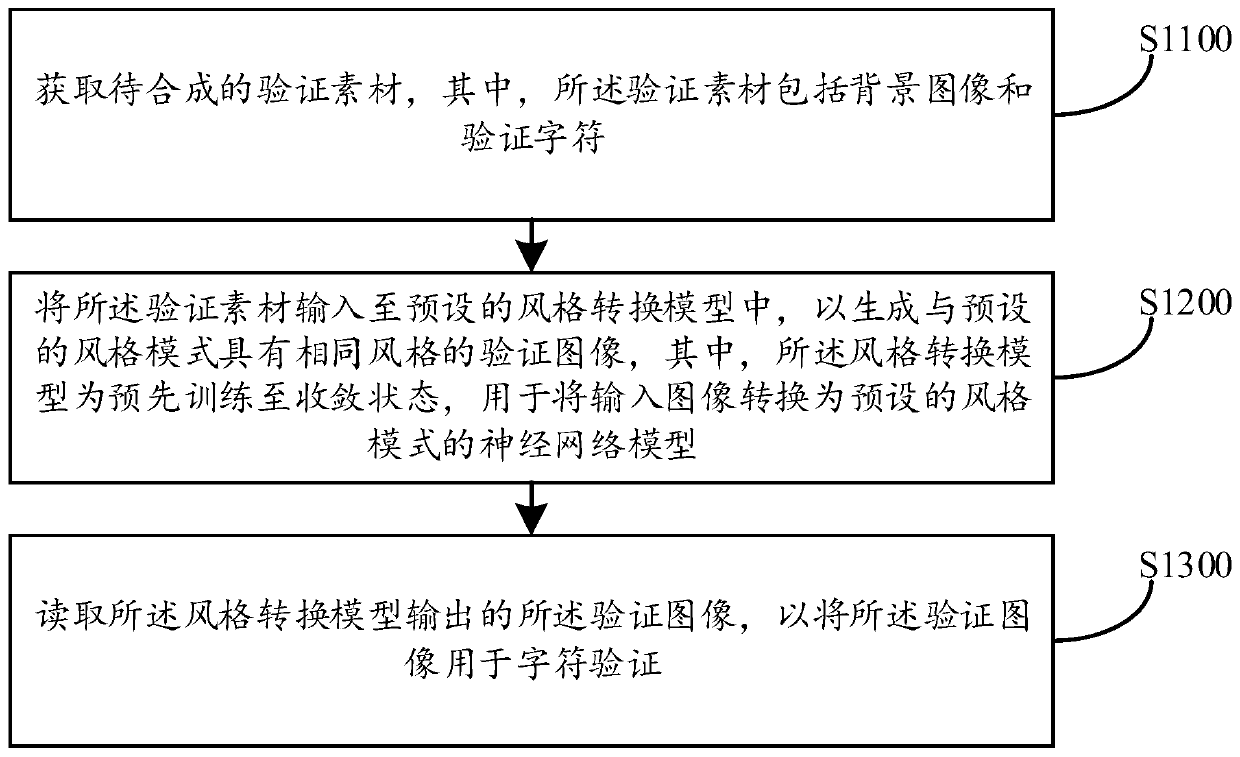
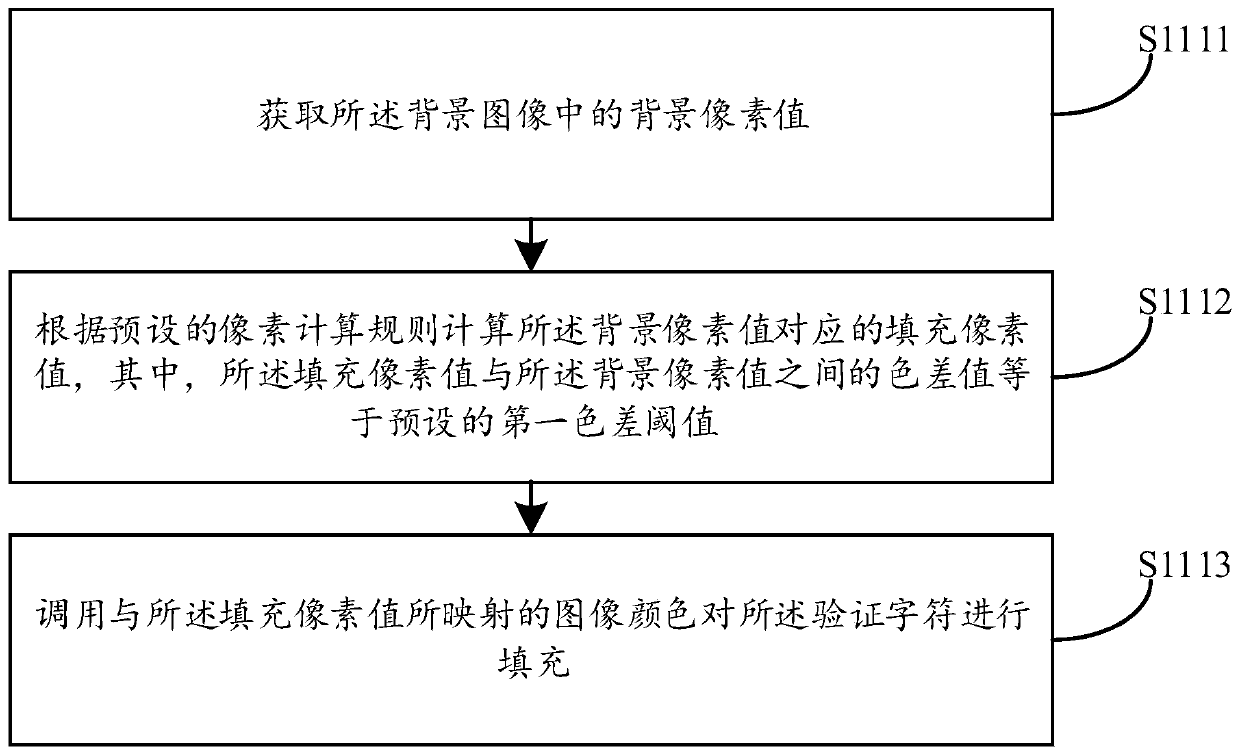
PendingCN110675308AIncrease confusionIncrease the difficultyGeometric image transformationDigital data authenticationImaging processingAlgorithm
The embodiment of the invention discloses a character verification method and device, computer equipment and a storage medium, and the method comprises the steps: obtaining a to-be-synthesized verification material which comprises a background image and a verification character; inputting the verification material into a preset style conversion model to generate a verification image having the same style as the preset style mode; and reading the verification image output by the style conversion model so as to use the verification image for character verification.The background image and the verification character are converted into the same style images, and then the grain change in the whole verification image is coherent and smooth; and the background image and the verification characterdo not have sharp pixel comparison, so that the difficulty of extracting the verification character through an image processing technology is improved, the confusion degree between the background image and the verification character is further improved, the recognition difficulty and the error rate are increased, and the safety of character verification is effectively guaranteed.
Owner:PING AN TECH (SHENZHEN) CO LTD
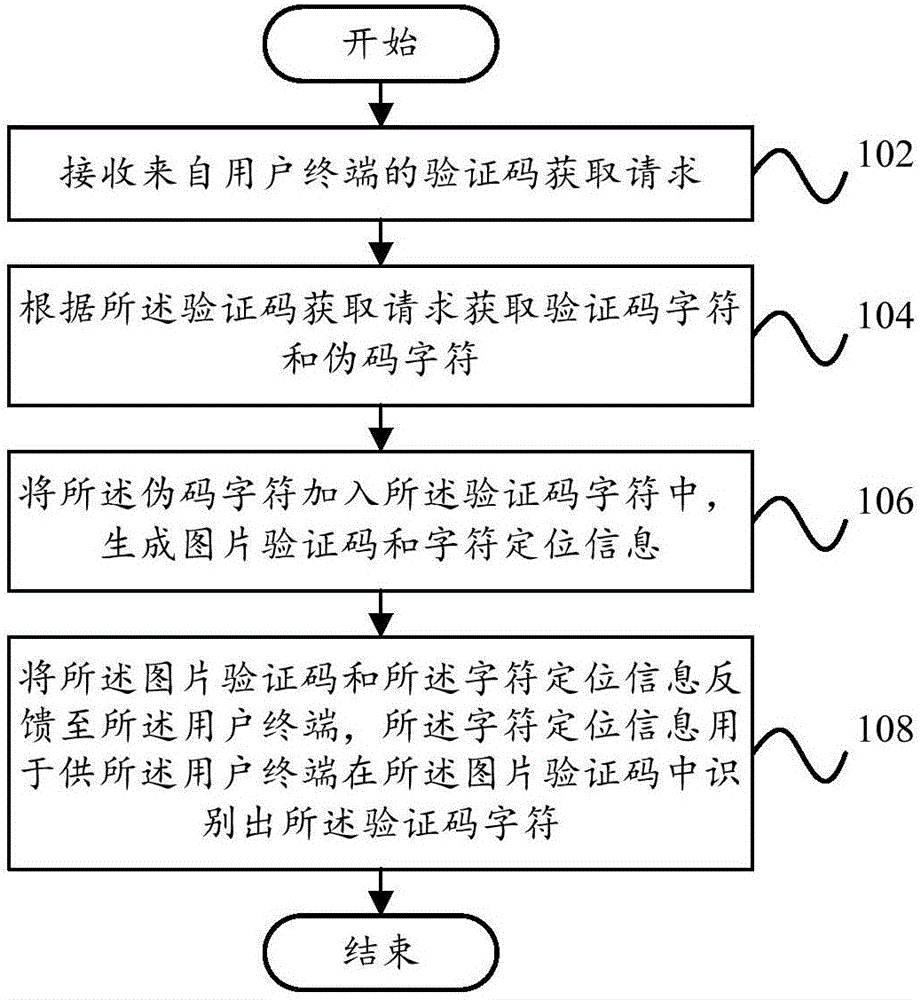
Processing method and processing device for image verification code
InactiveCN106778199AIncrease the difficulty of recognitionImprove experienceDigital data authenticationProgramming languageComputer terminal
The invention provides a processing method and processing device for an image verification code. The processing method for the image verification code comprises the steps that a verification code acquisition request from a user terminal is received; verification code characters and pseudo code characters are acquired according to the verification code acquisition request; the pseudo code characters are added into the verification code characters, and the image verification code and character positioning information are generated; the image verification code and the character positioning information are fed back to the user terminal, wherein the character positioning information is used for allowing the user terminal to identify the verification code characters from the image verification code. According to the technical scheme, the identification difficulty of the image verification code can be effectively increased, and therefore the information security and the user experience are improved.
Owner:ZICT TECH CO LTD
Method and apparatus for suppressing passive wireless earphones through pulsed magnet field
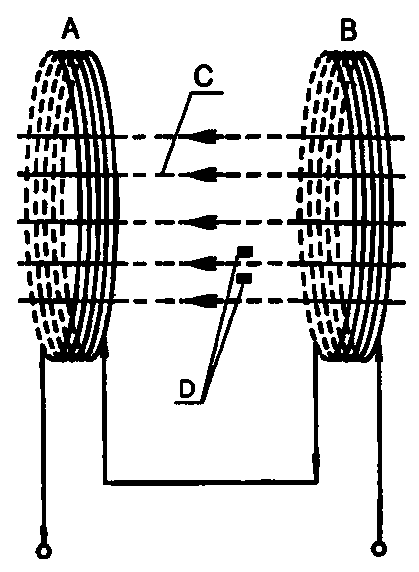
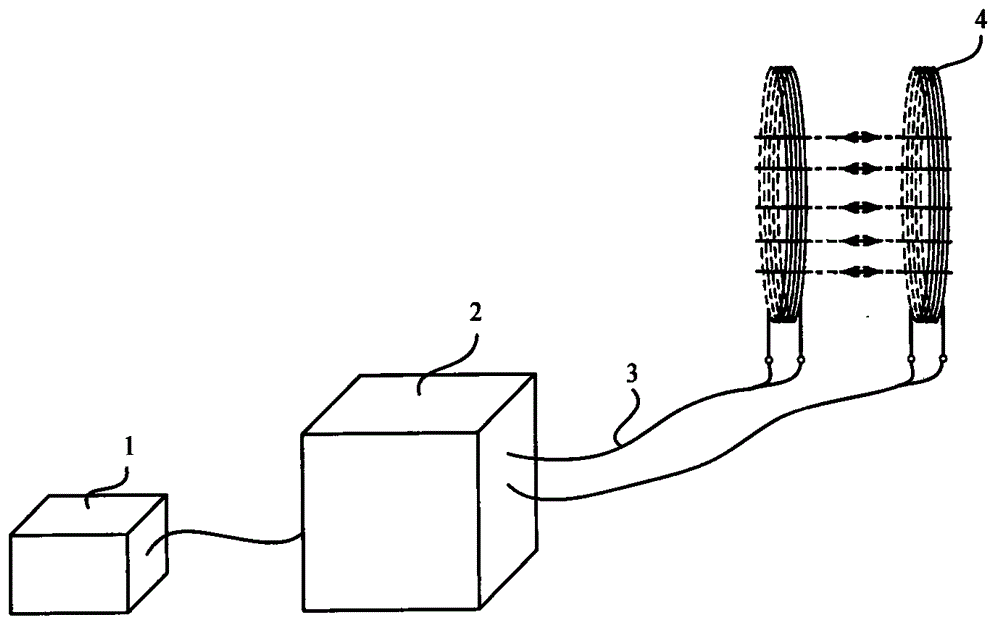
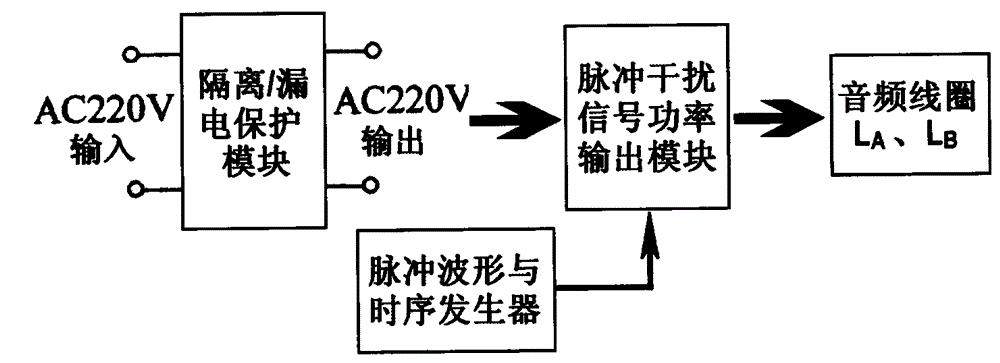
ActiveCN105101007AIncrease the difficulty of recognitionLarge range of electromagnetic fieldsElectric pulse generatorTransducer circuitsMicrocontrollerHigher order harmonics
The present invention relates to a method and an apparatus for suppressing passive wireless earphones through a pulsed magnet field. According to the method, a continuous pulse wave with the pulse duty factor of 50%:50% and a continuous pulse wave with the pulse duty factor changing within the range from 75%:25% to 25%:75% are adopted, a magnetic field coil is directly driven by superposition of base wave pulses and high-order harmonic pulses, an auditory discrimination mode of human is simulated, and reception of passive wireless earphones is suppressed, so as to interfere and destroy information transmission paths and conditions of cheating-used earphones. Various interference pulse signals are generated by a single chip microcomputer, and power complementary pair transistors are directly driven, the technology and the method are mature, reliable and easy to operate, and audio language classrooms or laboratory site facilities can be directly utilized.
Owner:胡建人
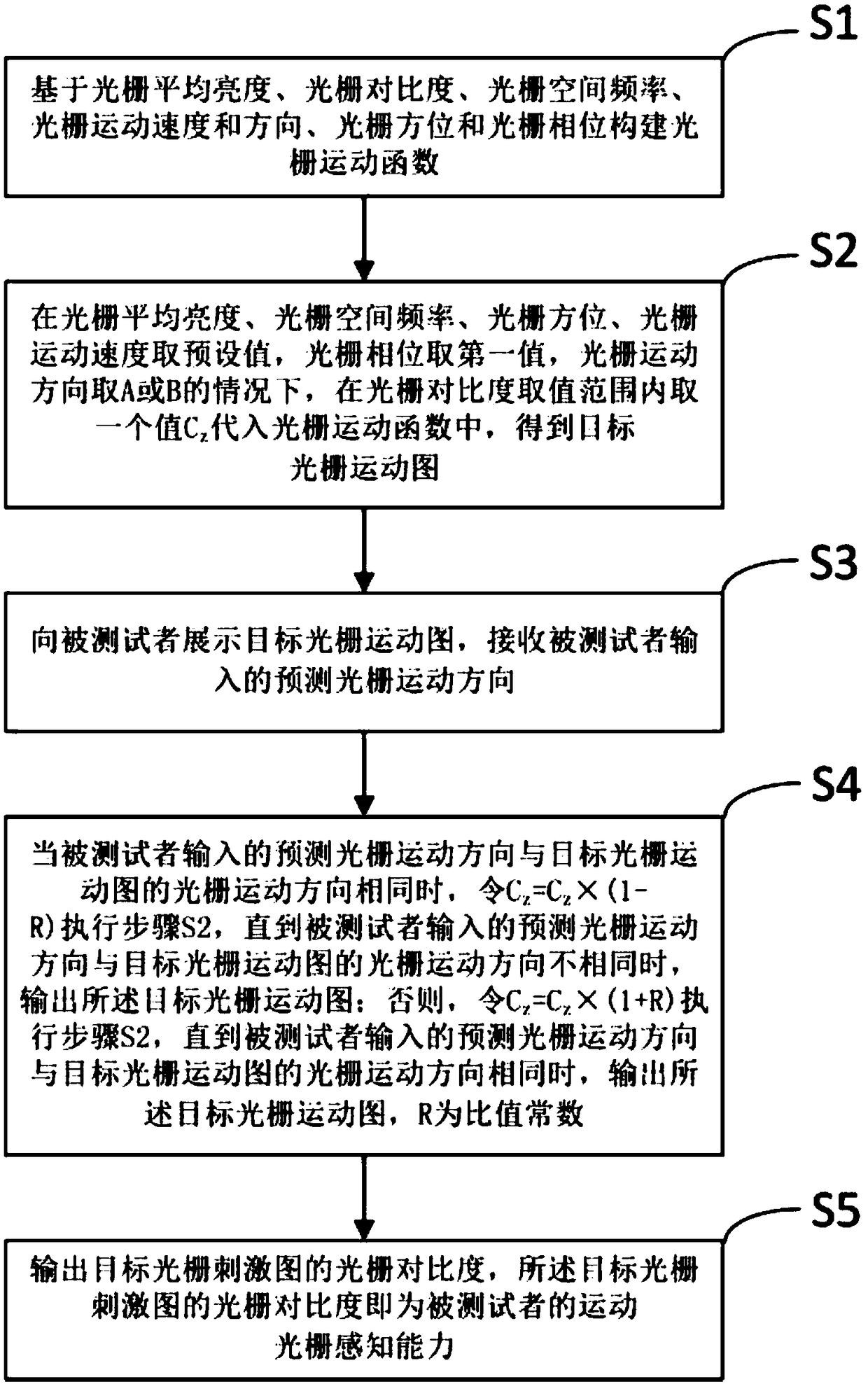
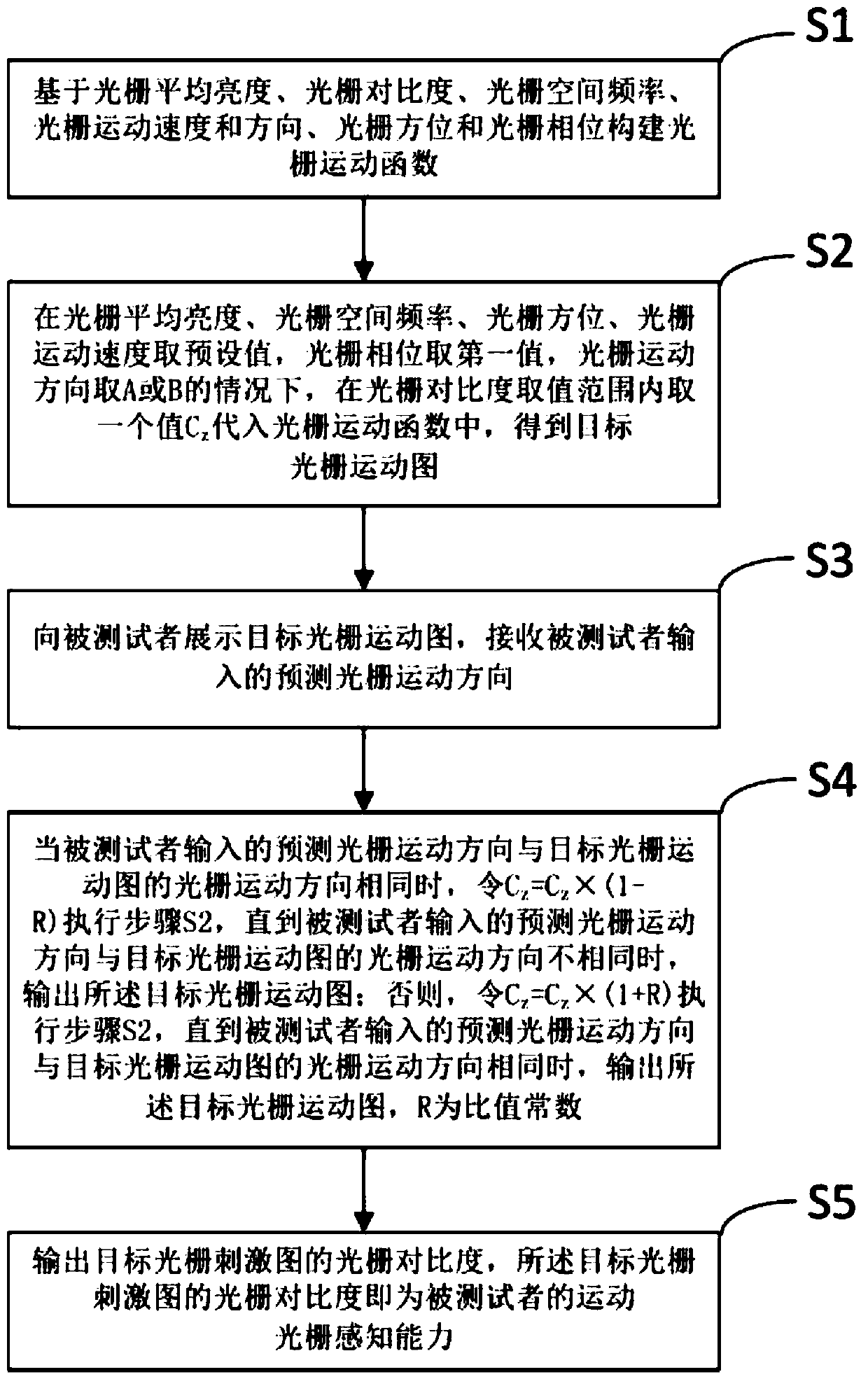
Method for detecting perception capacity of motion sinusoidal grating for brightness modulation
ActiveCN108742502AIncrease the difficulty of recognitionReduce the difficulty of identificationEye diagnosticsSinusoidal gratingClassical mechanics
The invention discloses a method for detecting the perception capacity of a motion sinusoidal grating for brightness modulation. The method includes the steps that a grating motion function is established based on the grating average brightness, the grating contrast,, the grating space frequency, the grating motion speed and direction, the grating azimuth and the grating phase; a first value is taken as the grating phase, A or B is taken as the grating motion direction, under the condition that other values are fixed values, the grating contrast Cz is taken and substituted into the grating motion function, and a grating motion graph is obtained; the grating motion graph is displayed to a testee; when the grating motion direction input by the testee and the grating motion direction of the grating motion graph are identical, Cz=Cz*(1-R) is substituted into the grating motion function till the input grating motion direction and the grating motion direction of the grating motion graph aredifferent, and a target grating motion graph is output; or else, Cz=Cz*(1+R) is substituted into the grating motion function till the input grating motion direction and the grating motion direction ofthe grating motion graph are identical, and the grating motion graph is output; the perception capacity of the testee is acquired according to the grating contrast of the grating motion graph.
Owner:科飞云视(天津)高新科技有限公司
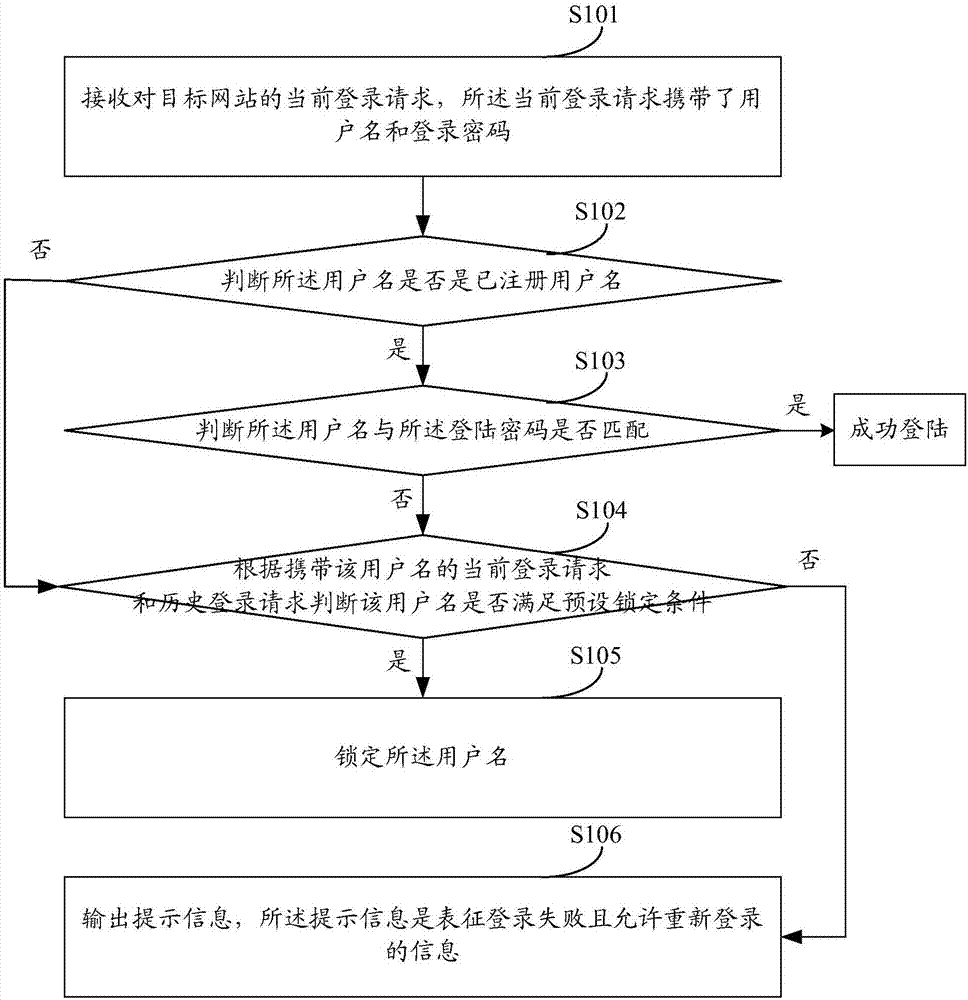
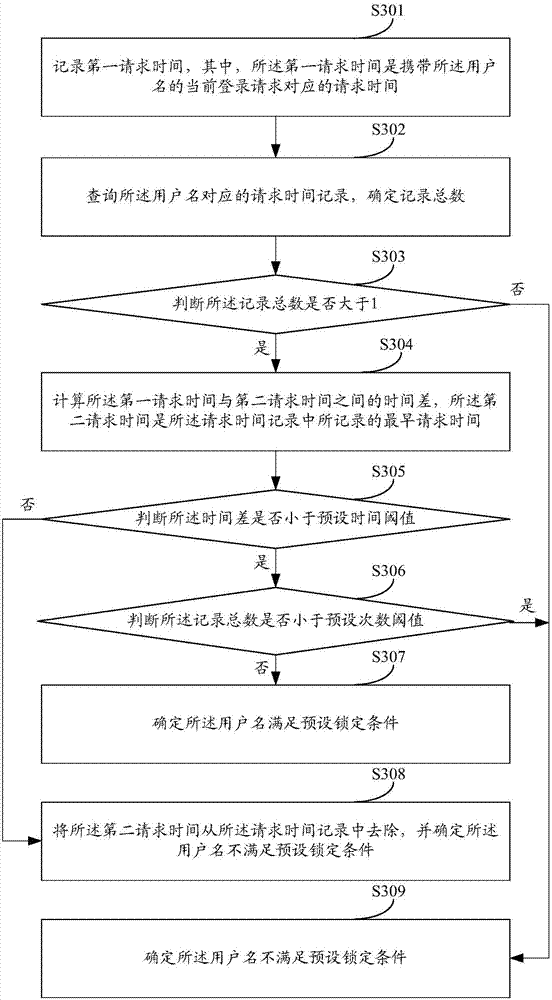
Username locking method and server
ActiveCN107959683AIncrease the difficulty of recognitionImprove securityTransmissionNetwork attackData mining
The invention discloses a username locking method and server. No matter a username used by a user to try to log in a target website is a registered username or an unregistered username, identical treatment is adopted as long as login failure occurs. Namely, whether the username meets a preset locking condition is determined. If the username meets the preset locking condition, the username is locked. If the username does not meet the preset locking condition, prompt information is output. Therefore, since identical treatment is adopted for each username that cannot achieve login success, network attacks cannot identify whether the current username is a registered username or not, so that the registered username identification difficulty is improved and network safety is further improved.
Owner:NEUSOFT CORP
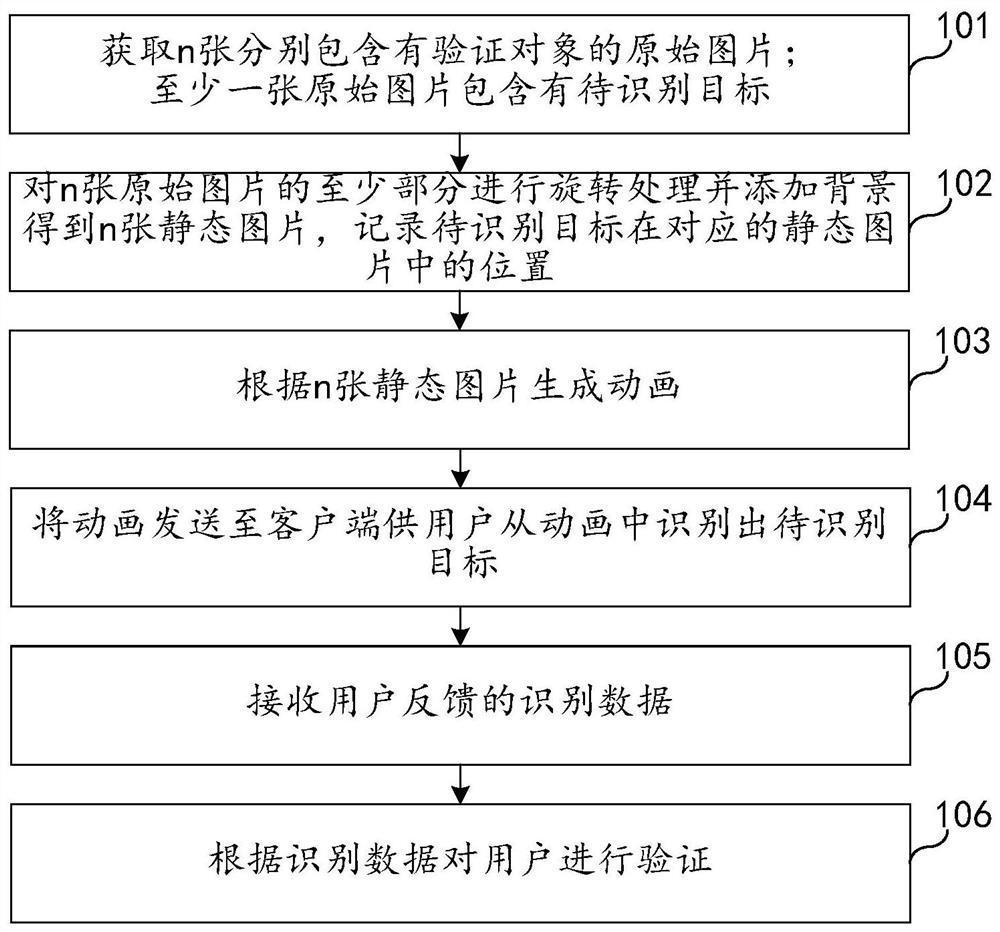
Dynamic graphic code verification method and device, electronic equipment and storage medium
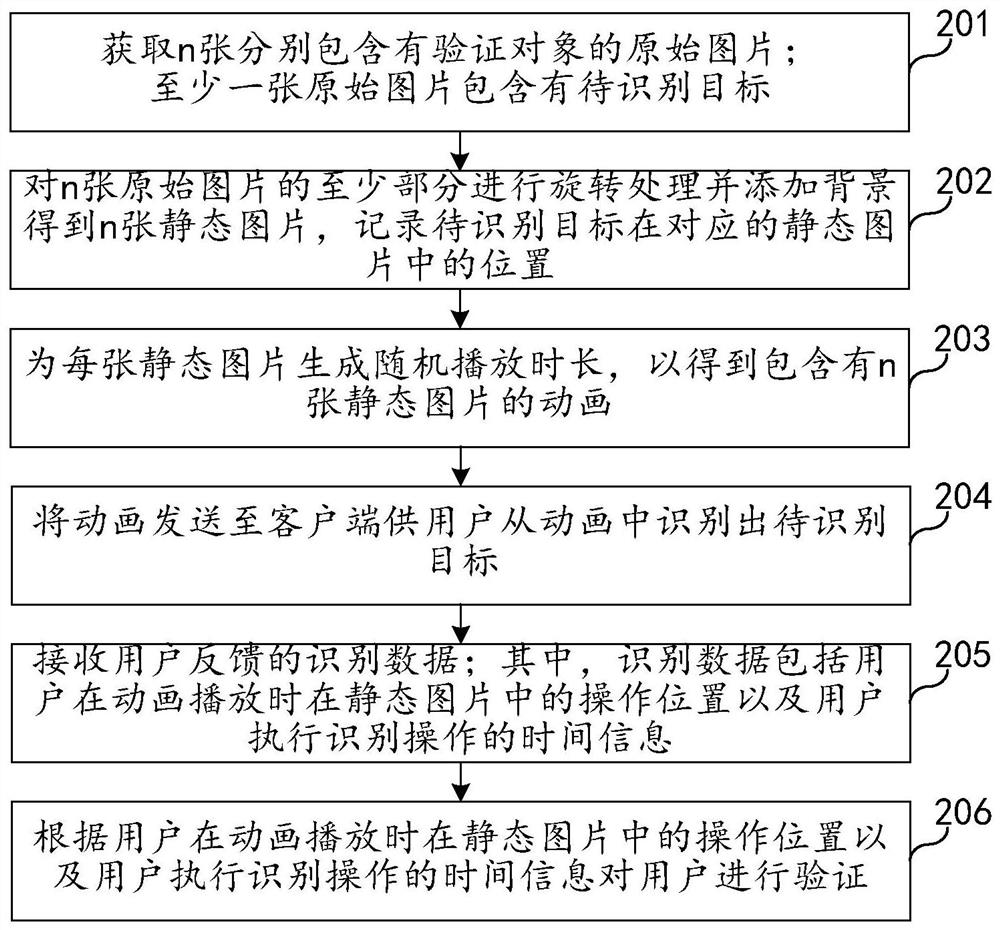
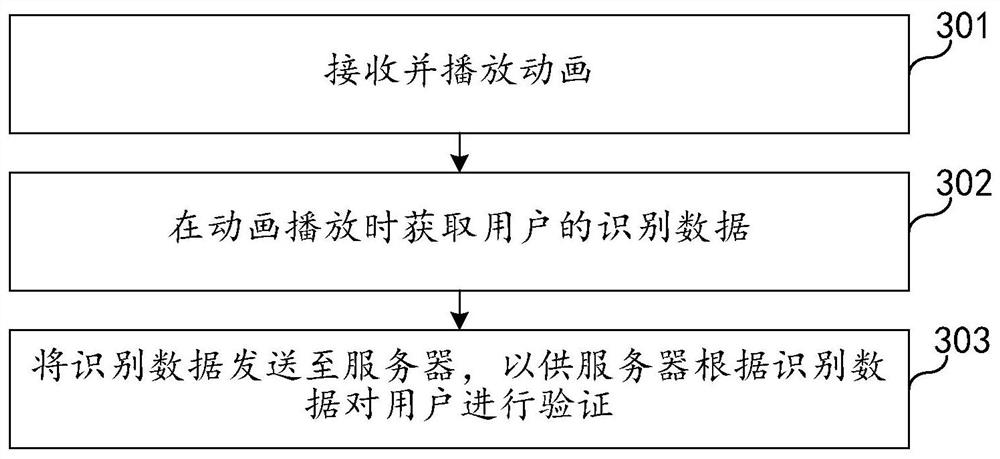
PendingCN111860482AIncrease the difficulty of recognitionRecognition difficulty does not affectCharacter and pattern recognitionAnimationData feedProgramming language
The embodiment of the invention relates to the technical field of Internet, and discloses a dynamic graphic code verification method and device, electronic equipment and a storage medium. The method comprises the following steps: acquiring n original pictures containing verification objects respectively, wherein the at least one original picture comprises a to-be-identified target; rotating at least part of the n original pictures, adding a background to obtain n static pictures, and recording the position of the to-be-identified target in the corresponding static picture; generating an animation according to the n static pictures; sending the animation to a client for a user to identify a to-be-identified target from the animation; receiving identification data fed back by the user, wherein the identification data at least comprises an operation position of the user in the static picture when the animation is played; and verifying the user according to the identification data. According to the embodiment of the invention, the machine identification difficulty can be effectively improved while the usability and the accuracy of a real user are ensured.
Owner:CHINA MOBILEHANGZHOUINFORMATION TECH CO LTD +1
HPLC transformer area identification test system, test method, test device and processor
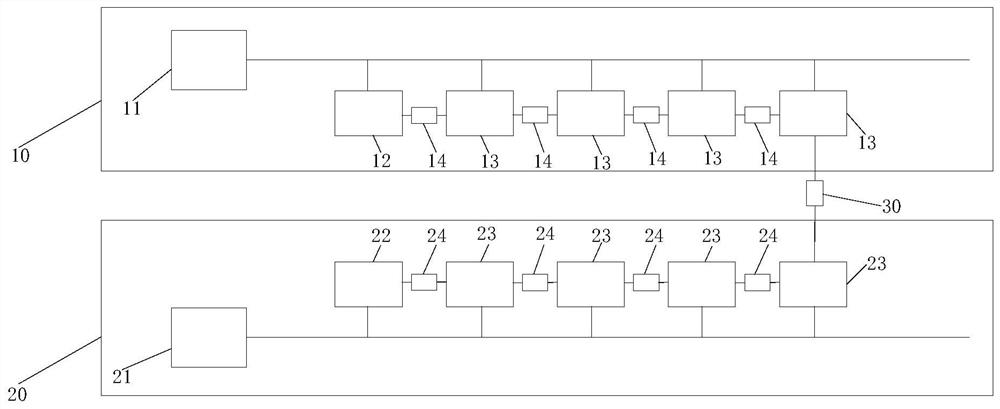
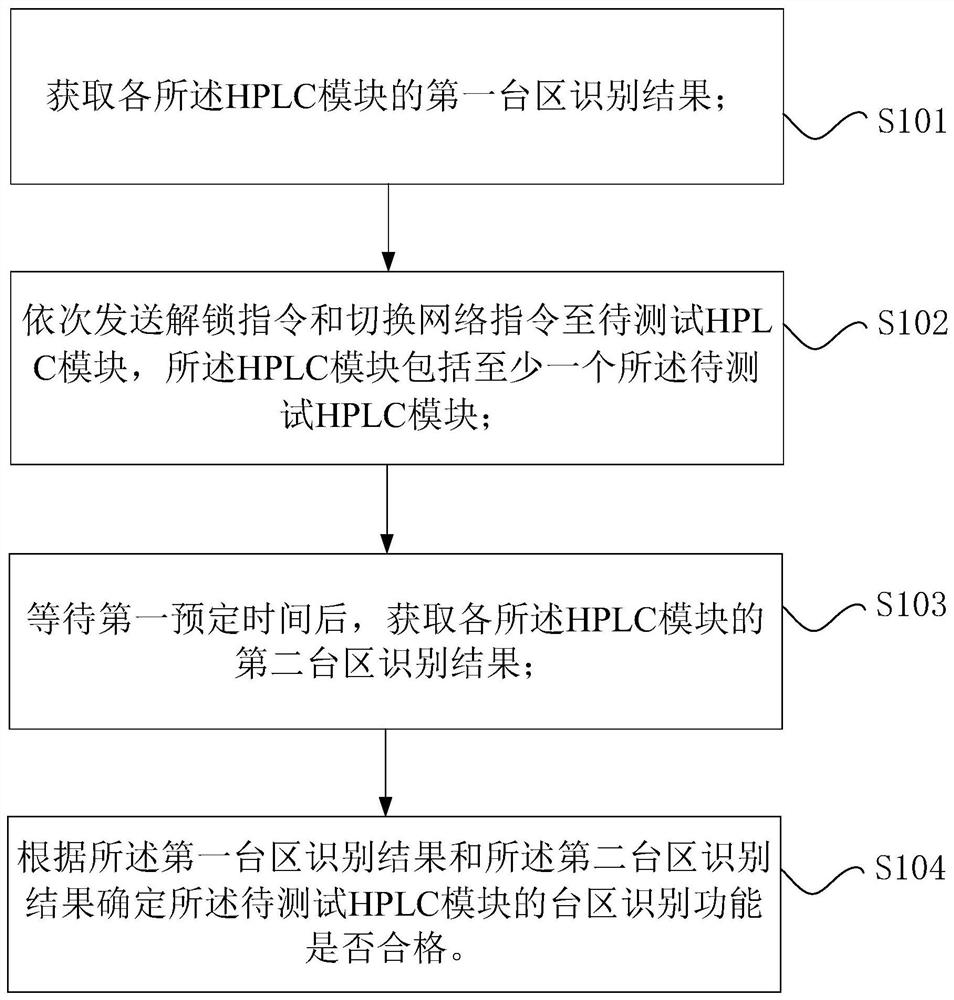
ActiveCN112422154AIncrease the difficulty of recognitionEnsure consistencyPower distribution line transmissionLine-transmission monitoring/testingTest efficiencyTransformer
The invention provides an HPLC transformer area identification test system, a test method, a test device and a processor. The system comprises a first simulation transformer area which comprises a first transformer, a first main shielding box, a first sub-shielding box and a first attenuator, wherein the first main shielding box and the first sub-shielding box are electrically connected with the output end of the first transformer, and the first main shielding box and the first sub-shielding box are in communication connection through a first attenuator in sequence; a second simulation transformer area which comprises a second transformer, a second main shielding box, a second sub-shielding box and a second attenuator, wherein the second main shielding box and the second sub-shielding boxare electrically connected with the output end of the second transformer, and the second main shielding box and the second sub-shielding box are in communication connection through the second attenuator in sequence; a third attenuator, wherein one end of the third attenuator is in communication connection with the first communication shielding box, and the other end is in communication connectionwith the second communication shielding box; and test software which is in communication connection with an HPLC module. Compared with the prior art, the system improves the test efficiency.
Owner:STATE GRID BEIJING ELECTRIC POWER +1
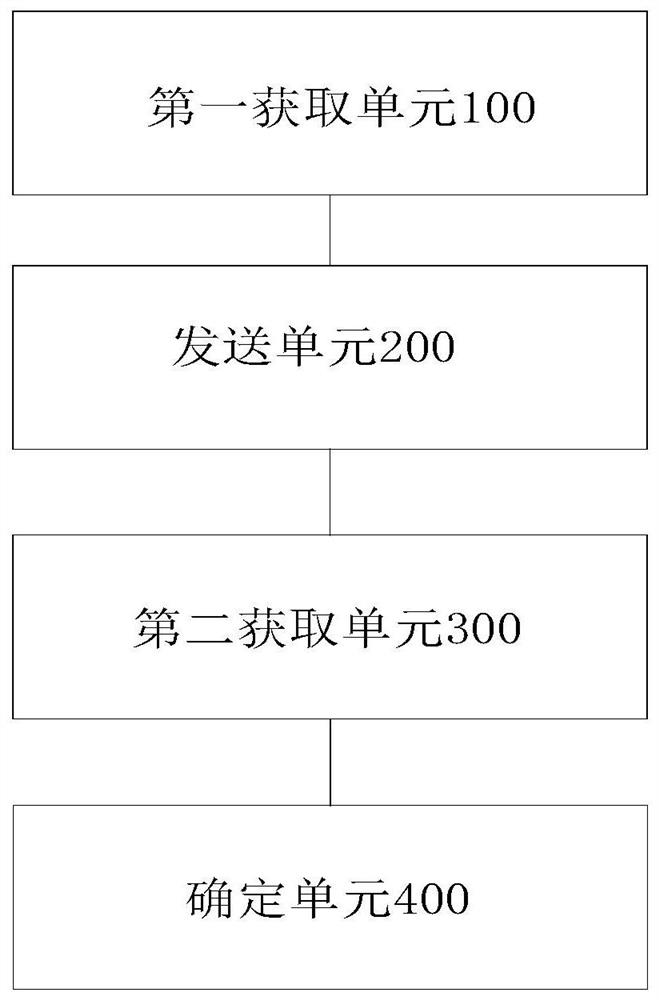
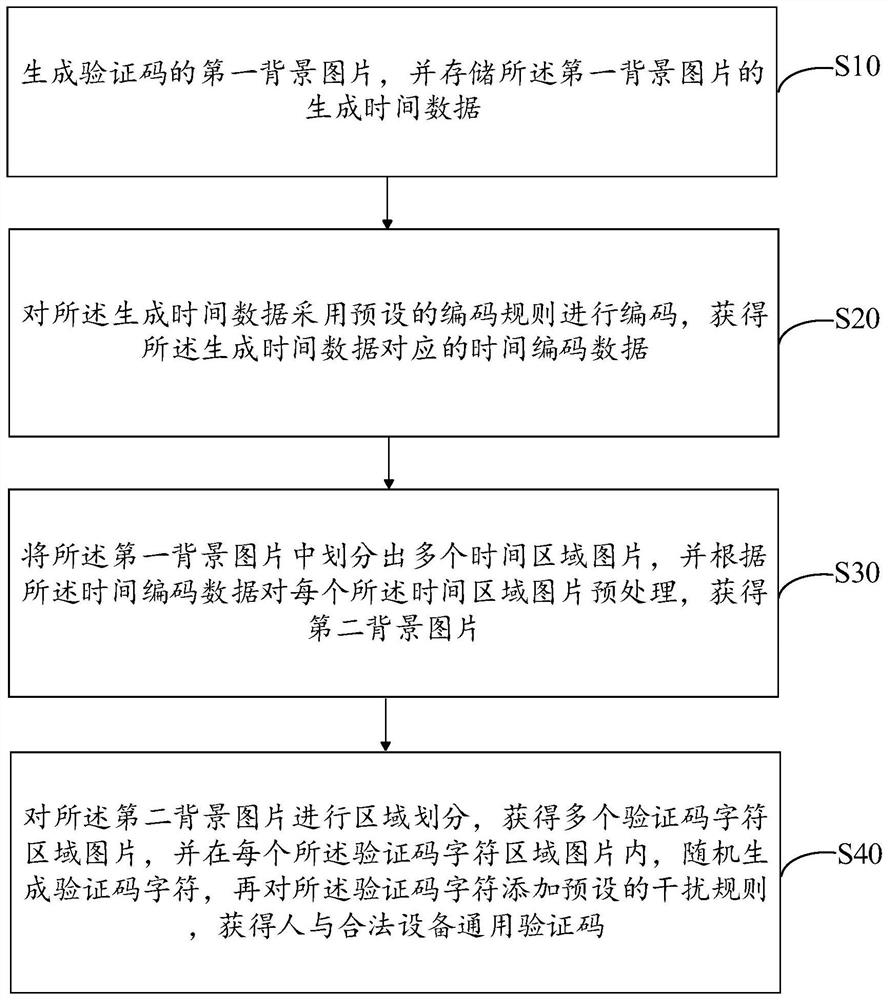
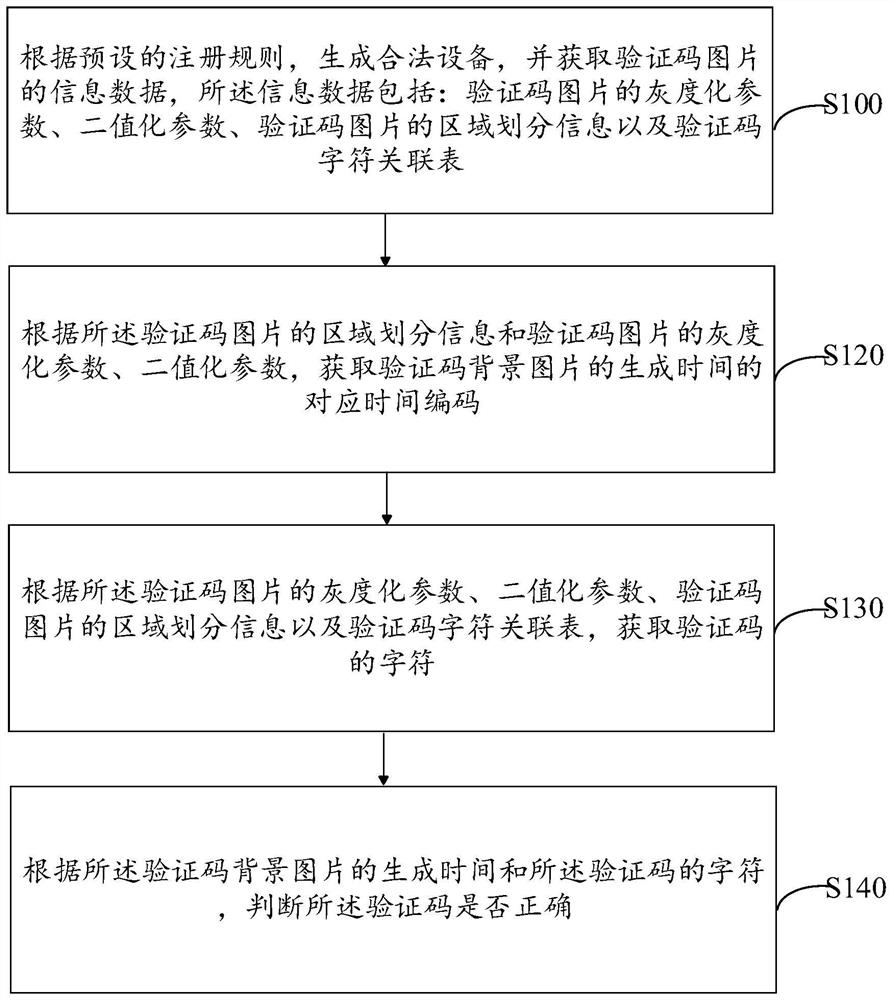
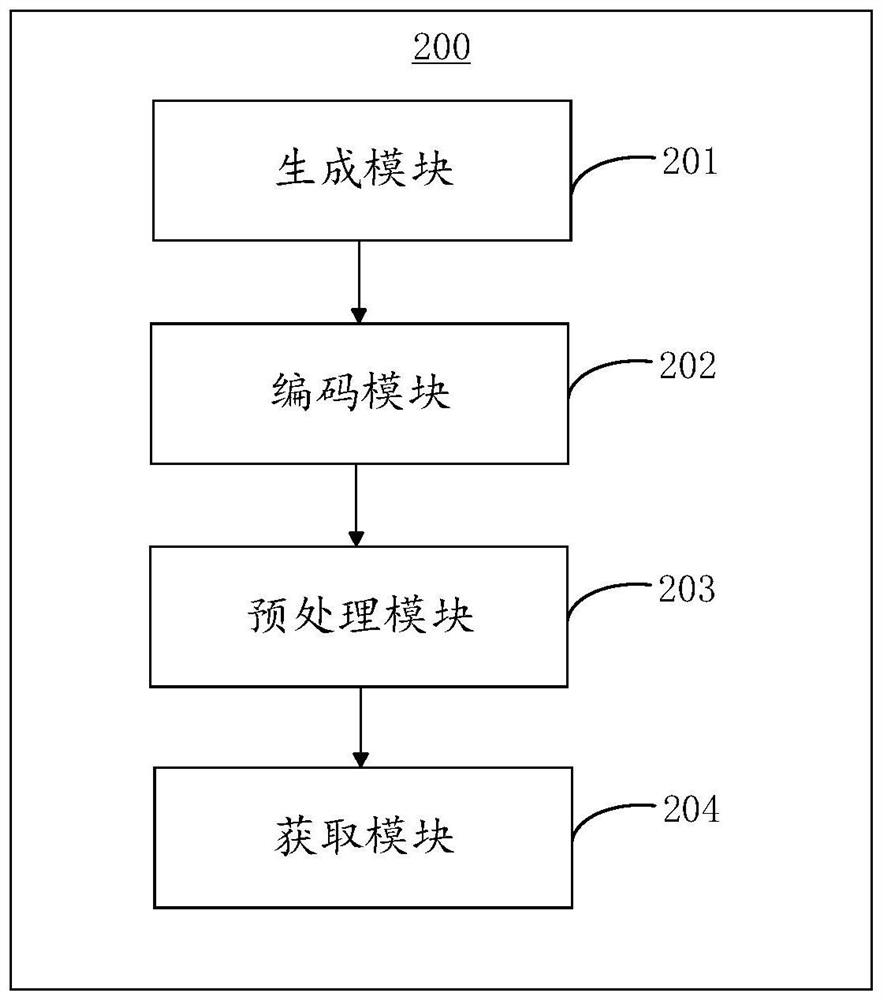
Generation method, verification method and device for universal verification code of person and legal equipment
ActiveCN114494474AReduce workloadReal identity is goodImage analysisImage codingAlgorithmProgramming language
The invention discloses a generation method, a verification method and a device for a universal verification code of a person and legal equipment, and the method comprises the steps: generating a first background picture of the verification code, and storing the corresponding generation time; encoding the generation time by adopting an encoding rule to obtain encoded data corresponding to the generation time; dividing the first background picture into a plurality of time region pictures, and preprocessing the time region pictures to obtain a second background picture; performing region division on the second background picture to obtain a verification code character region picture, randomly generating a verification code character in the verification code character region picture, randomly generating a verification code character in the verification code character region picture, and adding an interference rule to the verification code character to obtain a universal verification code for people and legal equipment. And universal verification of people and legal equipment is realized. According to the verification code generated by the method, the universality between a person and legal equipment can be realized, the identification speed of the equipment is higher, and the authentication efficiency is high.
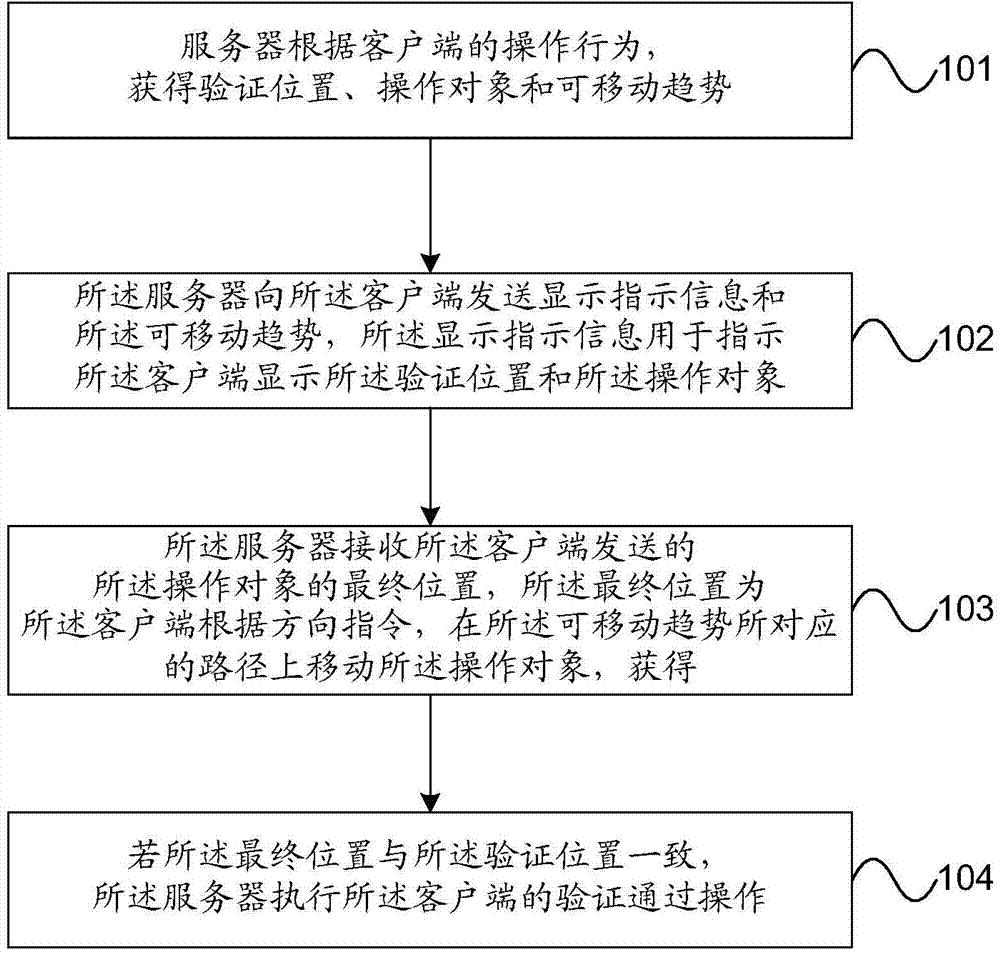
Owner:GUANGDONG UNIV OF PETROCHEMICAL TECH
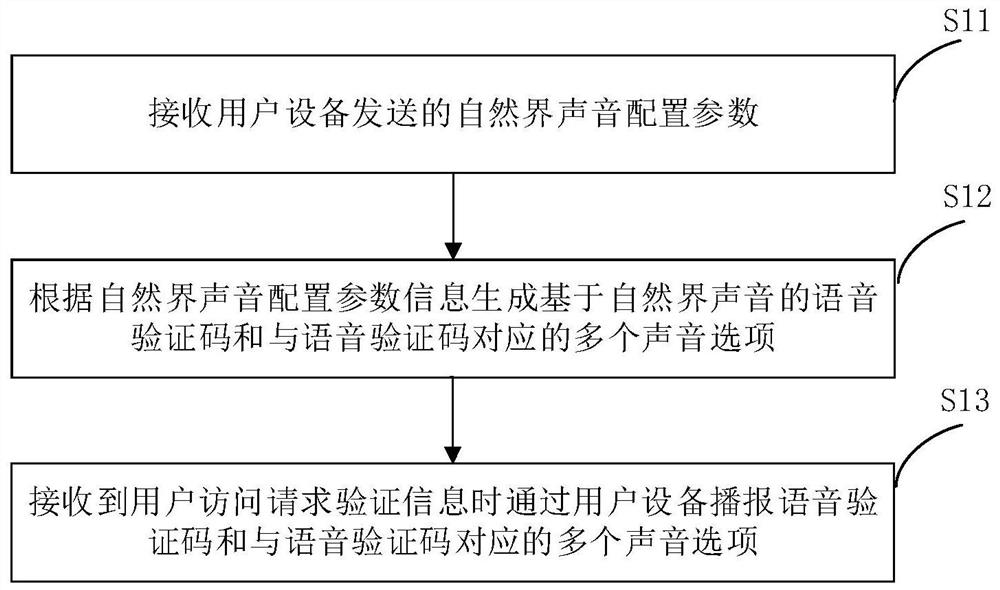
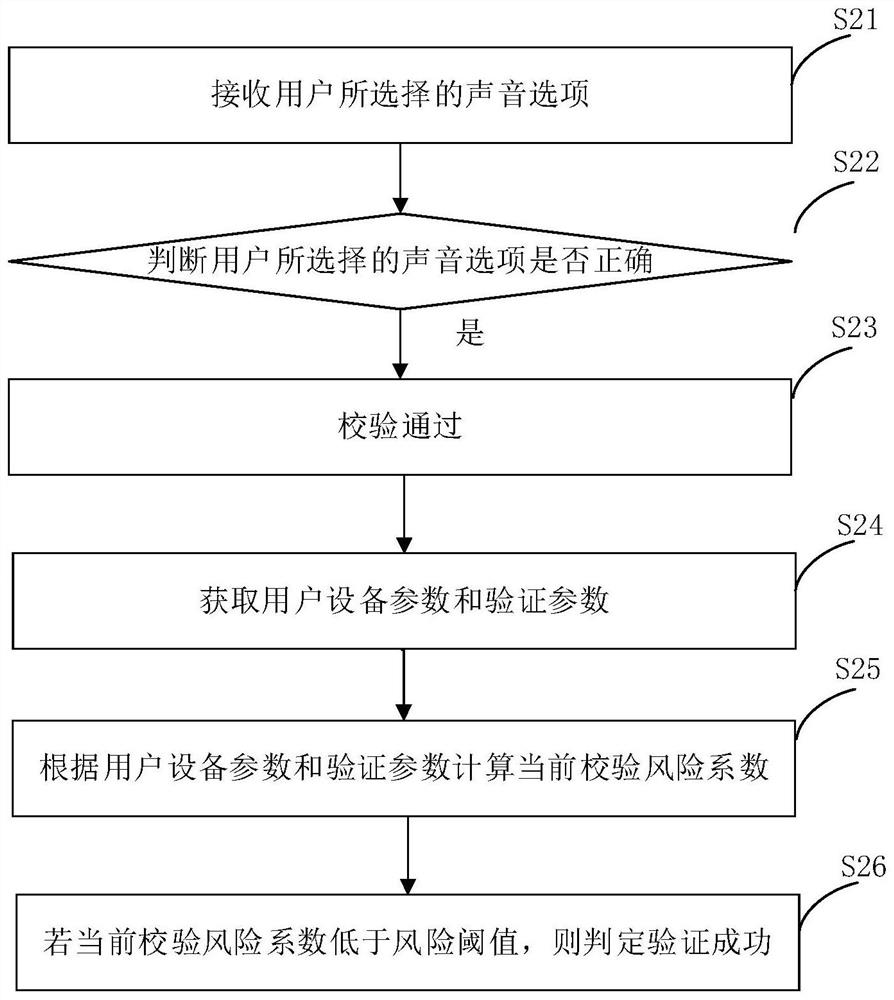
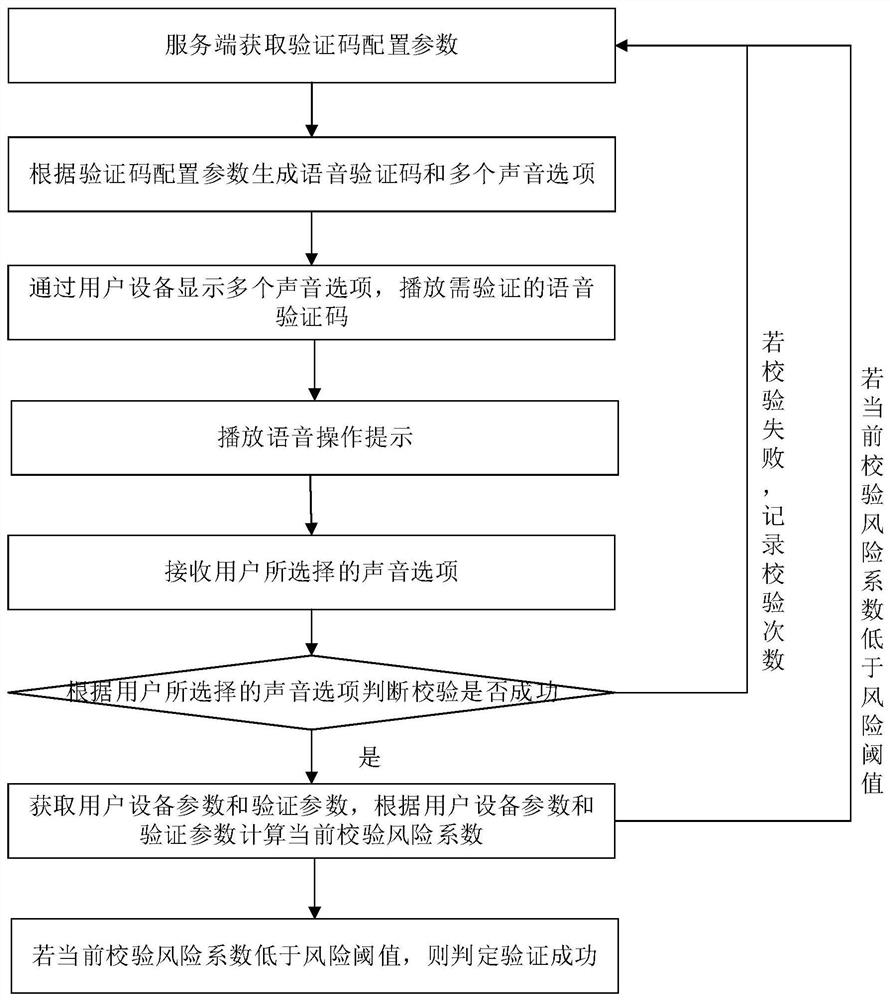
Voice verification code implementation method and device
PendingCN113114660AIncrease the difficulty of recognitionAvoid lostTransmissionTelecommunicationsMachine identification
The invention relates to a voice verification code implementation method and device, and the method comprises the steps of: receiving a natural sound configuration parameter sent by user equipment, generating a voice verification code based on the natural sound and a plurality of sound options corresponding to the voice verification code according to the natural sound configuration parameter information, and when user access request verification information is received, broadcasting the voice verification code and the plurality of voice options corresponding to the voice verification code through the user equipment. Man-machine behavior verification method for visually impaired people can be implemented, and the machine identification difficulty is improved through the voice verification code based on the natural sound, so that the service loss caused by hostile attacks is avoided, and the overall security of the system and the service is improved.
Owner:北京顶象技术有限公司
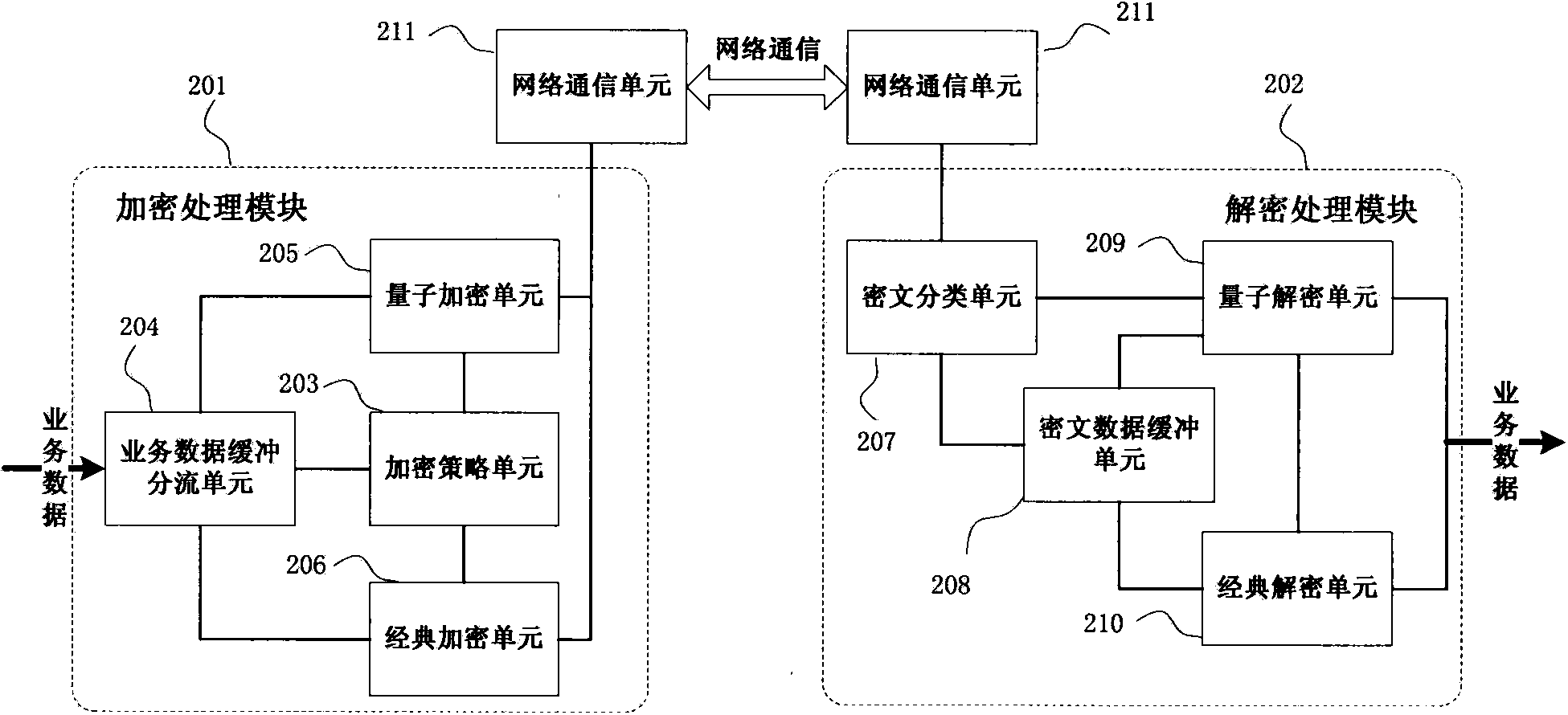
Quantum cryptography network reliable encrypted transmission system and method
ActiveCN103840936BImprove continuityImprove reliabilityKey distribution for secure communicationSynchronising transmission/receiving encryption devicesCiphertextDependability
The invention provides a reliable encrypted transmission system of quantum cryptography network, which includes an encryption processing module composed of an encryption strategy unit, a business data buffering and shunting unit, a classical encryption unit and a quantum encryption unit, and a ciphertext classification unit and a ciphertext data buffer unit. , a decryption processing module composed of a classical decryption unit and a quantum decryption unit. At the same time, the present invention also provides a reliable encryption transmission method for a quantum cryptography network, which adopts a classical encryption method and a quantum one-time pad encryption method for split transmission of business data, which can be changed in time according to the change in the supply and demand relationship of quantum keys. The proportion of business data distribution, on the basis of ensuring security, increases the continuity of encrypted transmission of business data, and improves the reliability of encrypted transmission of business data; at the same time, it reduces the consumption of quantum key data and the quantum cryptography network. The quantum key generation load reduces the cost of encrypted transmission of quantum cryptographic network business data.
Owner:SHANDONG INST OF QUANTUM SCI & TECH
Method and device for generating picture verification code
ActiveCN103106631BIncrease the difficulty of recognitionDifficulty will not increaseImage data processing detailsPattern recognitionMethod of images
Owner:ALIBABA GRP HLDG LTD
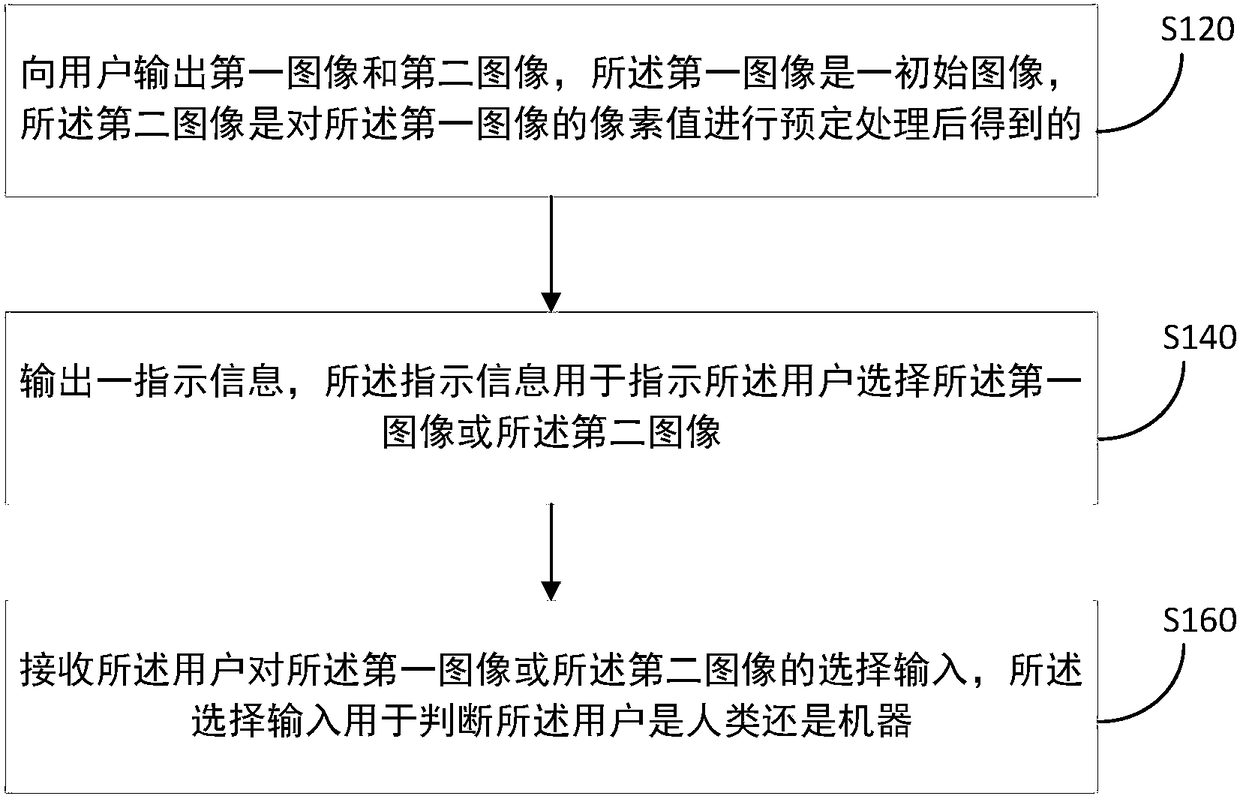
Method, terminal and server for authenticating user
ActiveCN109040001AReduce the difficulty of identificationIncrease the difficulty of recognitionImage enhancementImage analysisComputer terminalCAPTCHA
The present application provides a method, a terminal and a server for authenticating a user, and relates to the field of communications. The method includes: outputting a first image and a second image to a user, the first image being an initial image, and the second image being obtained by performing predetermined processing on pixel values of the first image; outputting an indication information for instructing the user to select the first image or the second image; receiving a selection input of the user to the first image or the second image, the selection input being used to determine whether the user is a human or a machine. The method significantly reduces the difficulty of human identification of the authentication code and enhances the user experience while maintaining or slightly increasing the difficulty of machine identification of the authentication code.
Owner:BEIJING BANGCLE TECH CO LTD
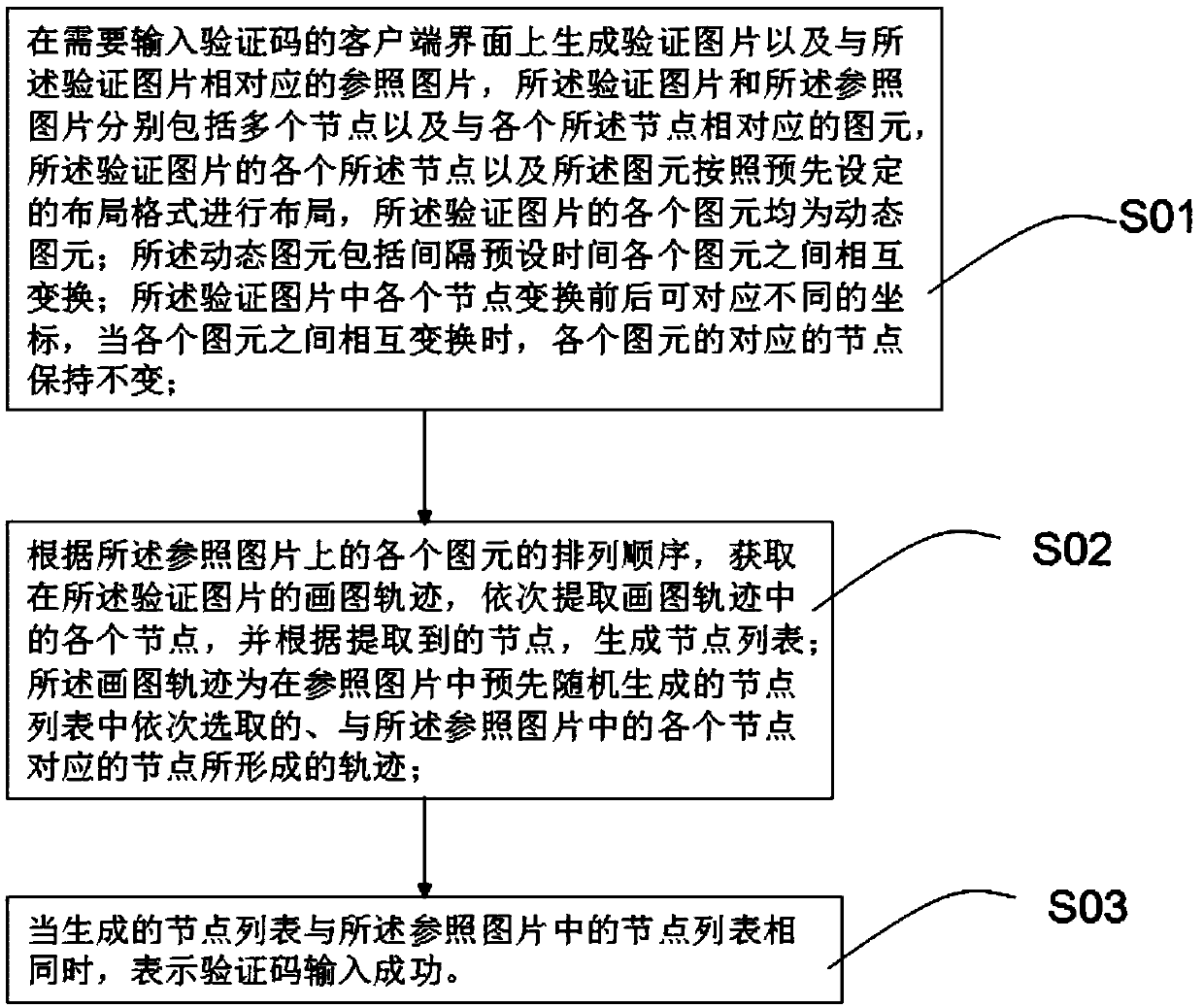
Verification code anti-brushing method
InactiveCN109614786AIncrease the difficulty of recognitionImprove securityDigital data authenticationMutual transformationThe Internet
The invention provides a verification code anti-brushing method, relating to the technical field of Internet. The method comprises the following steps: generating a verification picture and a reference picture corresponding to the verification picture on a client interface needing to input a verification code, wherein the verification picture and the reference picture respectively comprise a plurality of nodes and primitives corresponding to the nodes, the nodes and the primitives of the verification picture are arranged according to a preset layout format, and each primitive of the verification picture is a dynamic primitive; wherein the dynamic primitives comprise mutual transformation among the primitives at intervals of preset time; obtaining a drawing track of the verification picture, sequentially extracting each node in the drawing track, and generating a node list according to the extracted nodes; and when the generated node list is the same as the node list in the reference picture, indicating that the verification code is successfully input. According to the invention, the success rate of cracking the verification code by software can be effectively reduced, and the security of the verification code is improved.
Owner:TIANHE COLLEGE GUANGDONG POLYTECHNIC NORMAL UNIV
A detection method of brightness-modulated moving sinusoidal grating perception ability
ActiveCN108742502BIncrease the difficulty of recognitionReduce the difficulty of identificationEye diagnosticsSinusoidal gratingLightness
The invention discloses a method for detecting the perception capacity of a motion sinusoidal grating for brightness modulation. The method includes the steps that a grating motion function is established based on the grating average brightness, the grating contrast,, the grating space frequency, the grating motion speed and direction, the grating azimuth and the grating phase; a first value is taken as the grating phase, A or B is taken as the grating motion direction, under the condition that other values are fixed values, the grating contrast Cz is taken and substituted into the grating motion function, and a grating motion graph is obtained; the grating motion graph is displayed to a testee; when the grating motion direction input by the testee and the grating motion direction of the grating motion graph are identical, Cz=Cz*(1-R) is substituted into the grating motion function till the input grating motion direction and the grating motion direction of the grating motion graph aredifferent, and a target grating motion graph is output; or else, Cz=Cz*(1+R) is substituted into the grating motion function till the input grating motion direction and the grating motion direction ofthe grating motion graph are identical, and the grating motion graph is output; the perception capacity of the testee is acquired according to the grating contrast of the grating motion graph.
Owner:科飞云视(天津)高新科技有限公司
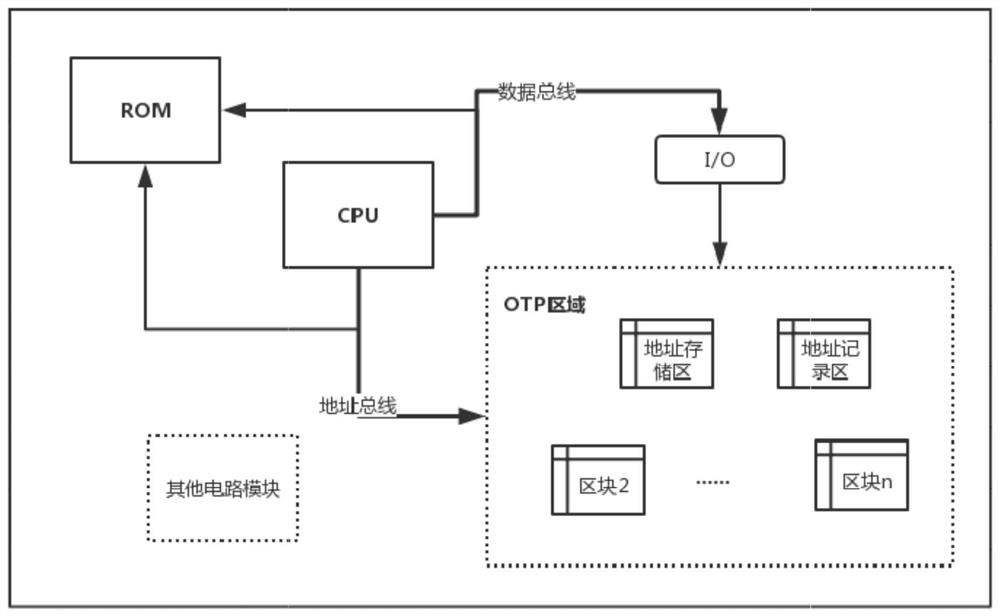
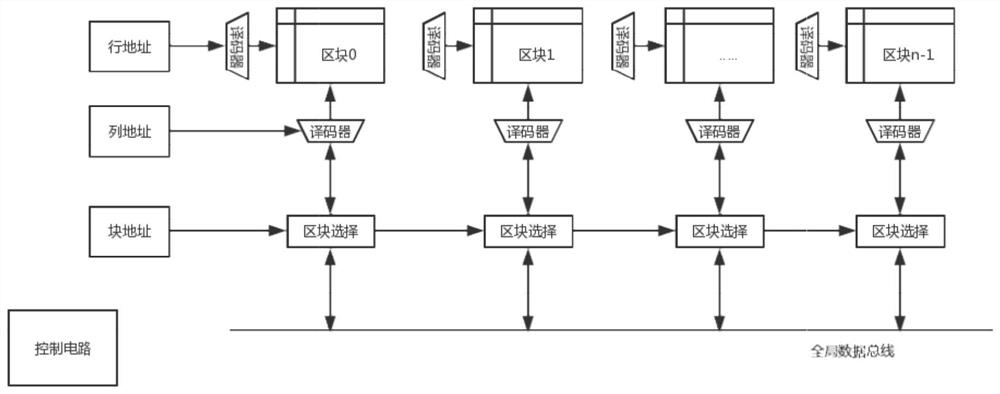
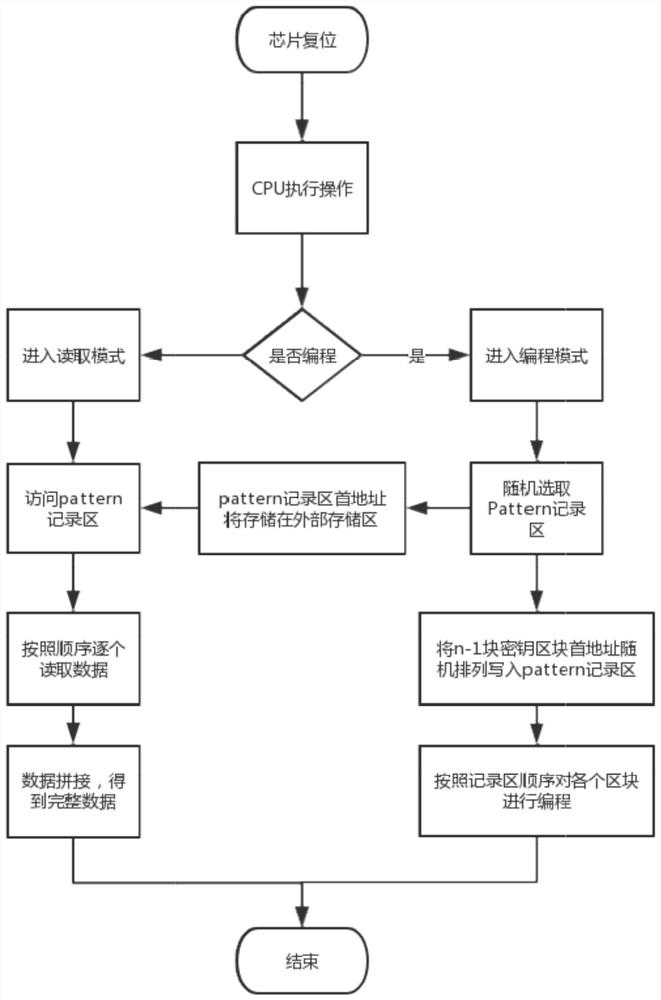
A kind of otp memory and its data writing and reading method, security chip
ActiveCN107908359BNot easy to break intoNot easy to findInput/output to record carriersInternal/peripheral component protectionComputer architectureStorage security
Owner:SHENZHEN GRADUATE SCHOOL TSINGHUA UNIV
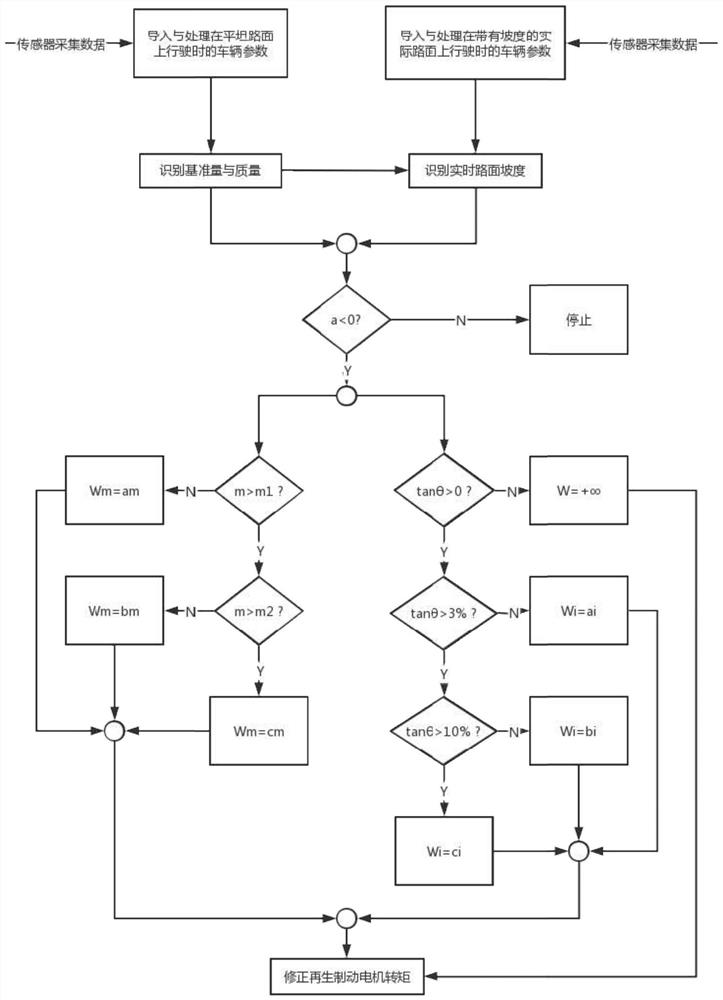
Braking energy recovery and correction method for vehicle mass and road slope recognition
PendingCN114771270AImprove adaptabilityLow costElectrodynamic brake systemsDriver input parametersMotor speedRegenerative brake
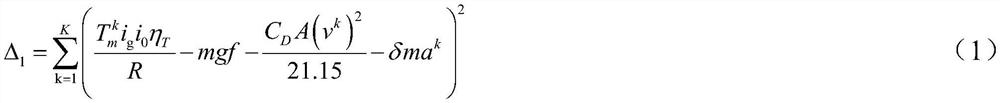
The invention provides a braking energy recovery correction method for vehicle mass and road slope recognition, which comprises the following steps of: acquiring an accelerator pedal opening signal, a driving motor rotating speed signal and a vehicle speed signal by using a standard accelerator pedal opening sensor, a driving motor rotating speed sensor and a vehicle speed sensor on a vehicle, and calculating related parameters; vehicle mass and ramp gradient identification is completed as an identification sample; according to the method, vehicle parameters and dynamic balance equation parameters of a flat road surface are packaged and simplified into reference quantities, and the reference quantities are used as known quantities for identifying the slope gradient, so that the identification difficulty and precision of the slope gradient are improved; by recognizing the vehicle mass and the ramp gradient, the motor negative torque for regenerative braking is corrected, and braking energy recovery correction control is conducted on the pure electric vehicle during ramp braking, so that the adaptability of vehicle braking energy recovery is improved.
Owner:JILIN UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com