Username locking method and server
A user name and server technology, applied in the computer field, can solve problems such as unfavorable network security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
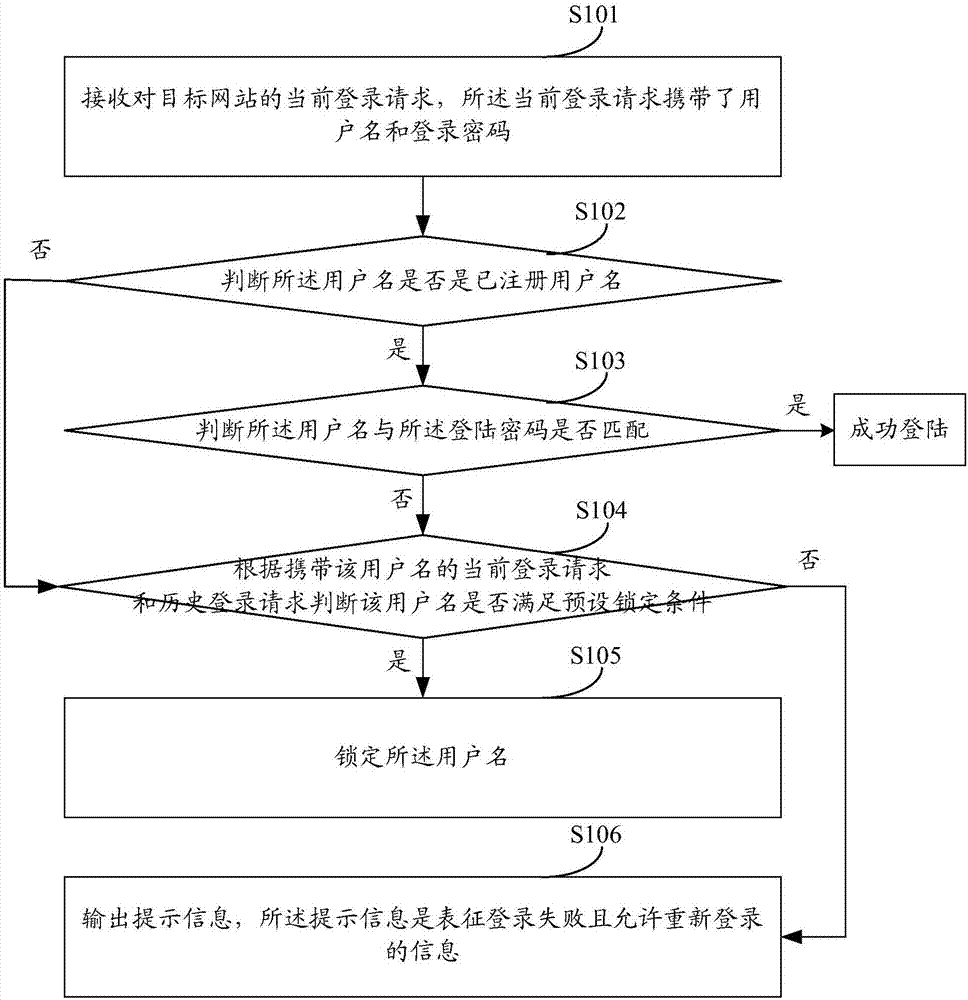
[0063] see figure 1 , this figure is a flow chart of the username locking method provided by this embodiment, and the username locking method provided by this embodiment includes the following steps:
[0064] S101: Receive a current login request to a target website, where the current login request carries a user name and a login password.
[0065] It should be noted that the user name locking methods provided in the following embodiments of the present application can be applied to servers. It should also be noted that, unless otherwise specified, the users mentioned in the following embodiments of the present application may be legitimate users of the target website (legal users for short), or network attackers.
[0066] In addition, this embodiment does not limit the type of the target website, for example, the target website may be a news website, a shopping website, a portal website and so on.
[0067] Such as figure 2 As shown, when the user sends a login request to ...
no. 2 example
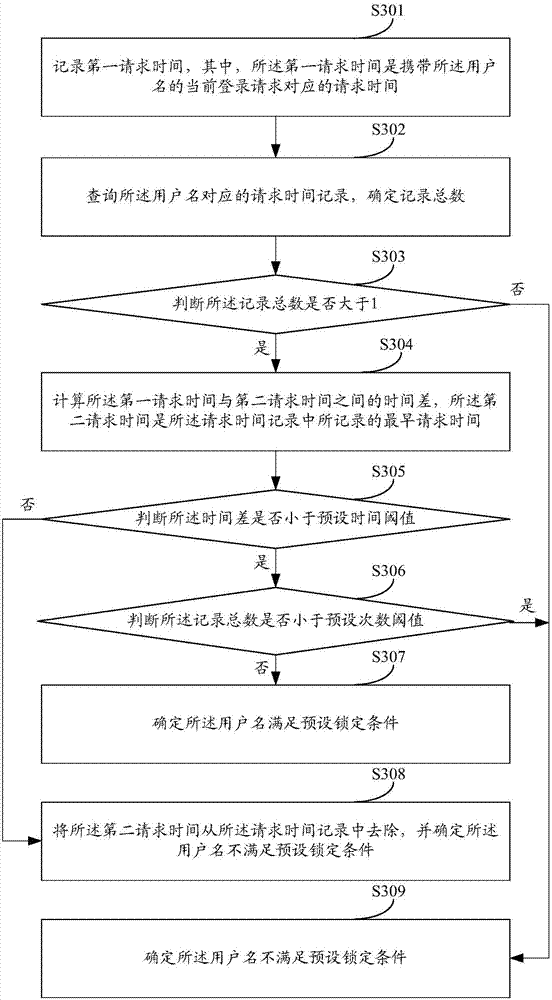
[0083] Regarding the user name locking method provided in the first embodiment, the second embodiment will specifically introduce an implementation method of S104 in the first embodiment with reference to the accompanying drawings.
[0084] see image 3 , this figure is a flow chart of the username locking method provided by this embodiment, and the username locking method provided by this embodiment includes the following steps:
[0085] S301: Record a first request time, where the first request time is a request time corresponding to a current login request carrying the username.
[0086] It should be noted that when implementing S301, a time queue can be maintained for each username that has not passed verification in the cache or other storage locations, that is, as long as a new username is parsed from the login request, and If the new user name is an unregistered user name, or the new user name is a registered user name but the login password is wrong, a time queue is c...
no. 3 example
[0115] Considering that in practical applications, before a legitimate user visits the target website for the first time, he needs to register a user name and set a corresponding password. Then, the legitimate user can use the user name and password to send a login request on the login interface provided by the target website, and the user can access the target website only after the login is successful.
[0116] In view of this, the embodiment of the present application also provides a user name locking method, which mainly introduces user registration and user access in detail, and the third embodiment will introduce the method with reference to the accompanying drawings.
[0117] see Image 6 , which is a flowchart of a method for locking a user name provided in this embodiment. The method for locking a user name provided in this embodiment includes the following steps:
[0118] S601: Receive a registration request to the target website, where the registration request carr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com