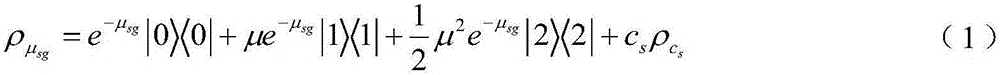RFID system bidirectional authentication method based on decoy state quantum random key
A decoy state quantum, two-way authentication technology, applied in the field of RFID system two-way authentication based on decoy state quantum randomization keys, can solve the problems of limited computing power and easy theft of private data, and achieve the effect of enhancing security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
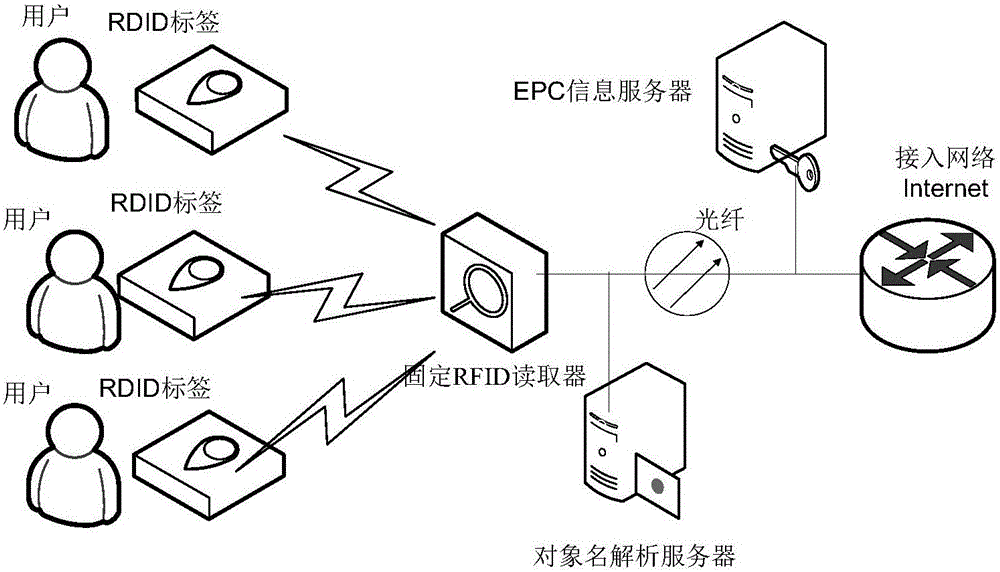
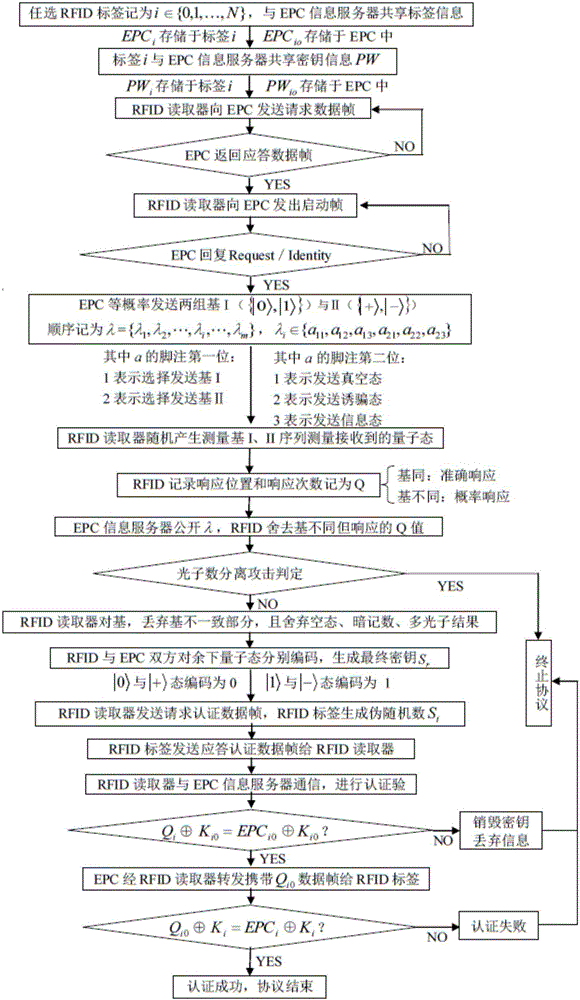
[0042] In embodiment one, the RFID system two-way authentication method based on decoy state quantum randomization key of the present invention comprises the following steps:
[0043] Step (1): The RFID reader associates with the EPC information server, and starts the EPC information server;
[0044] Step (2): After the EPC information server is started, the EPC information server sends two kinds of weakly coherent lights, the information state and the decoy state, to the RFID reader with equal probability;
[0045] Step (3): The RFID reader receives two kinds of weakly coherent lights, the information state and the decoy state, and extracts the key;
[0046] Step (4): The RFID reader sends the key to the RFID tag; the RFID tag encrypts the tag information, and forwards the encrypted tag information to the EPC information server through the RFID reader for authentication. If the authentication is successful, then Go to the next step; otherwise, the authentication fails;
[0...
Embodiment 2
[0101] The two-way authentication method in Embodiment 2 includes the following steps:
[0102] Step (1): The RFID reader associates with the EPC information server, and starts the EPC information server;
[0103] Step (2): The RFID reader receives two weakly coherent lights, the information state and the decoy state, sent by the EPC information server with equal probability, extracts the key, and sends the key to the RFID tag;
[0104] Step (3): The RFID reader receives the tag information encrypted by the RFID tag, and forwards it to the EPC information server for authentication. If the authentication is successful, enter the next step; otherwise, the authentication fails;
[0105] Step (4): The RFID reader receives the tag information encrypted by the EPC information server and stored in the EPC information server, and forwards it to the RFID tag for authentication. If the authentication is successful, the two-way authentication of the RFID system is successful; otherwise, ...
Embodiment 3
[0126] The RFID system two-way authentication method based on the decoy state quantum randomization key comprises the following steps:
[0127] Step (1): After the EPC information server receives the associated information sent by the RFID reader, start the EPC information server;
[0128] Step (2): The EPC information server sends two weakly coherent lights, the information state and the decoy state, to the RFID reader with equal probability;
[0129] Step (3): The EPC information server receives the encrypted tag information and performs authentication, and if the authentication is successful, enters the next step; otherwise, the authentication fails;
[0130] The encrypted tag information is the tag information that the RFID tag encrypts according to the received key, and the key is the key extracted by the RFID reader according to two kinds of weak coherent light in the information state and the decoy state;
[0131] Step (4): The EPC information server encrypts the tag i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com