Techniques for dynamically supporting different authentication algorithms
An authentication algorithm and dynamic technology, applied in machine-to-machine/machine-type communication services, electrical components, safety devices, etc., can solve problems such as unrealistic and limited flexibility of authentication algorithms
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] Representative applications of apparatus and methods according to the presently described embodiments are provided in this section. These examples are provided merely to add context and to aid in understanding the described embodiments. It will therefore be apparent to those skilled in the art that the presently described embodiments may be practiced without some or all of these specific details. In other instances, well known process steps have not been described in detail in order to avoid unnecessarily obscuring the presently described embodiments. Other applications are possible such that the following examples should not be considered limiting.
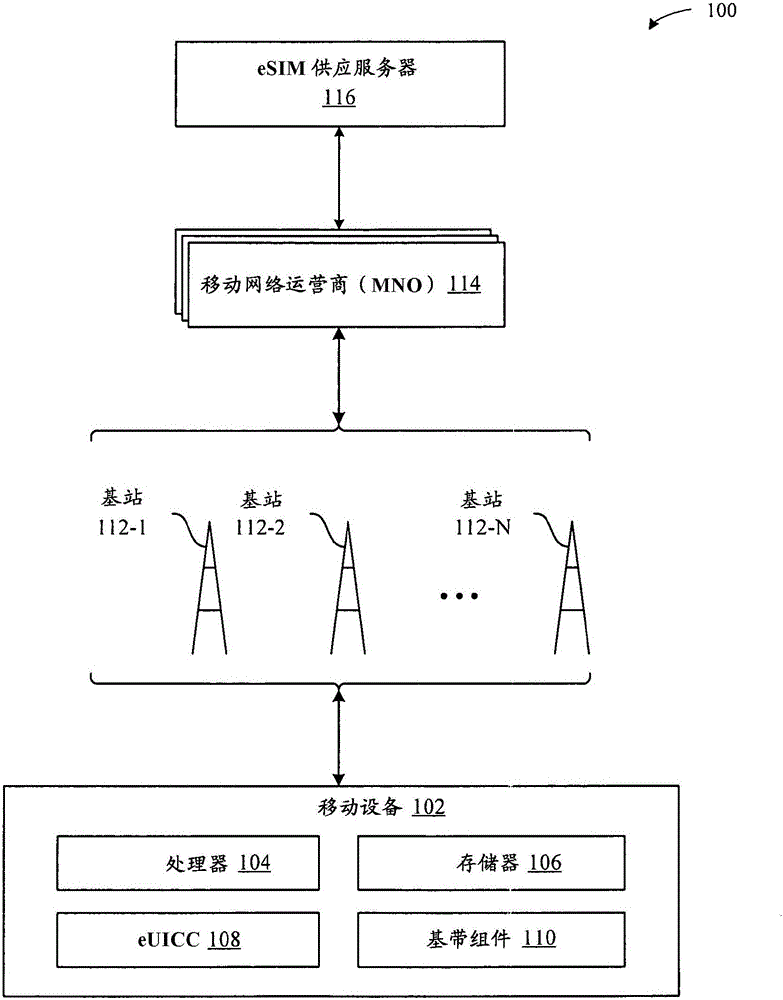
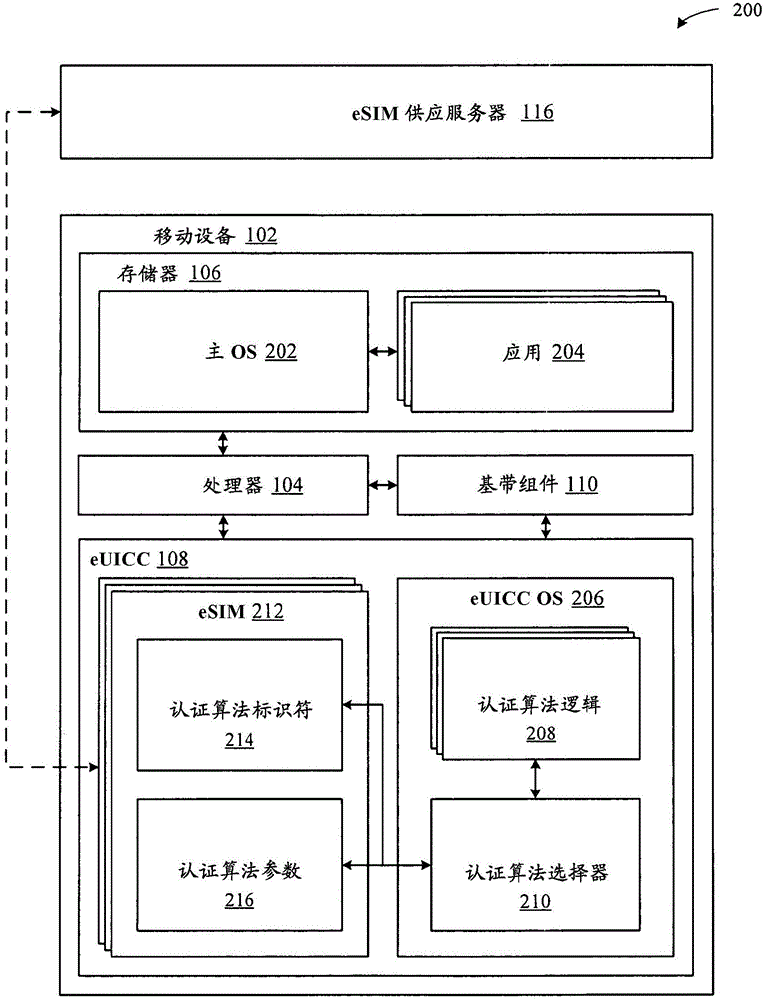
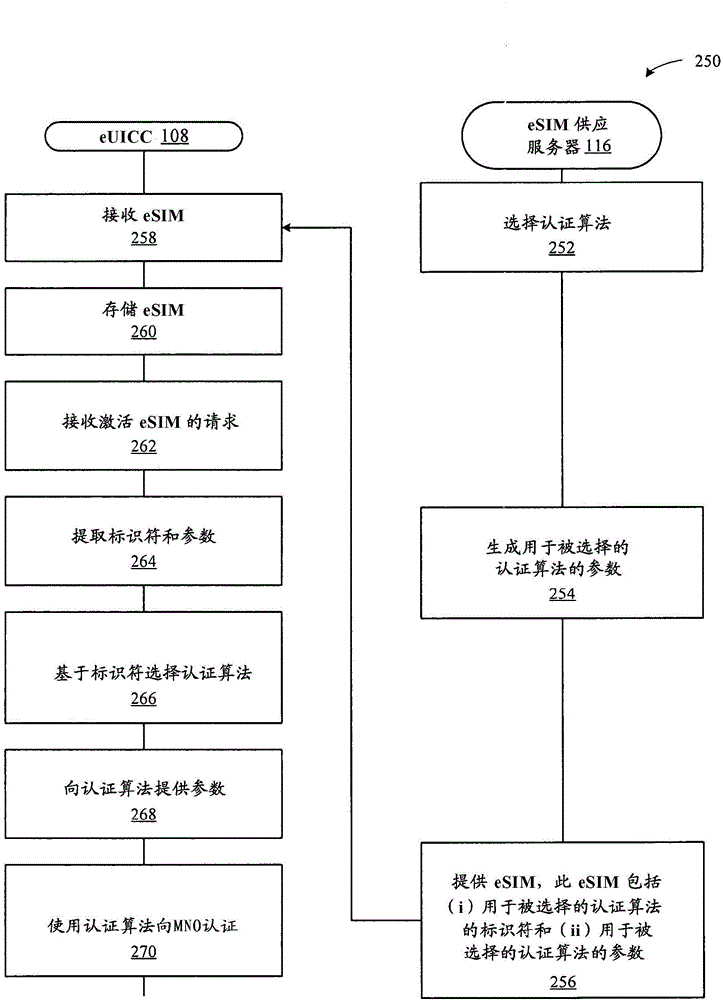
[0019] Embodiments described herein illustrate two different techniques for enabling a mobile device to dynamically support different authentication algorithms. The different authentication algorithms described herein relate to the algorithms used by the mobile device for establishing a secure connection with the MNO so ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com