Safe and valid signature scheme for electronic file and paper file thereof
A technology for electronic documents and paper documents, applied in the field of information security, can solve the problems of waste of resources, general use, not having the validity of recognizing the content of a certain document, etc., to achieve the effect of saving resources and convenient verification of signatures and seals
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] Below in conjunction with accompanying drawing, the present invention is described in further detail, and steps are as follows:
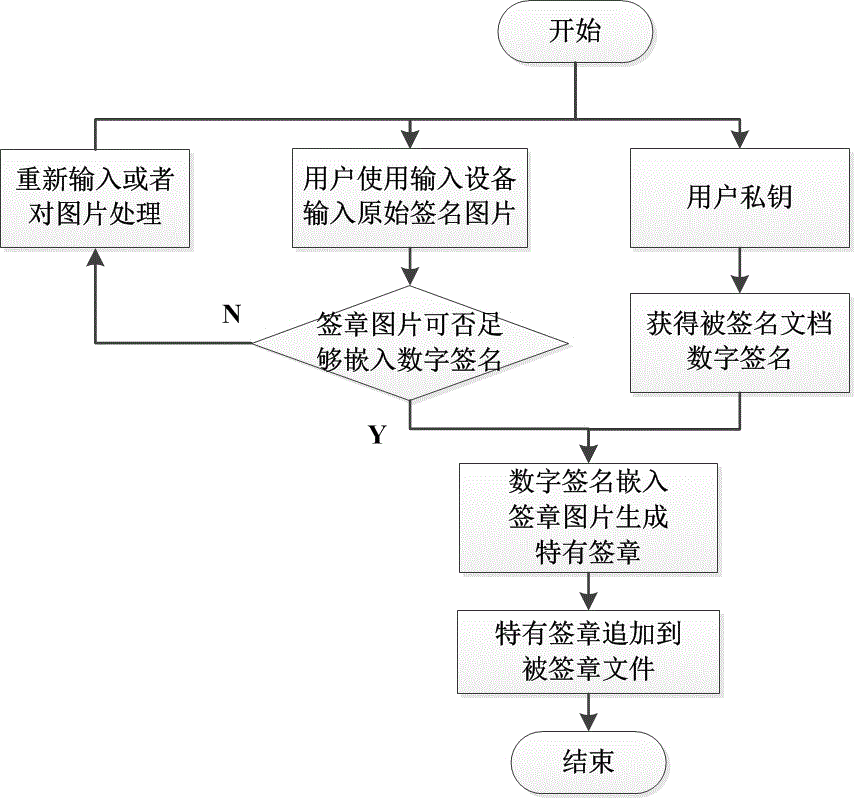
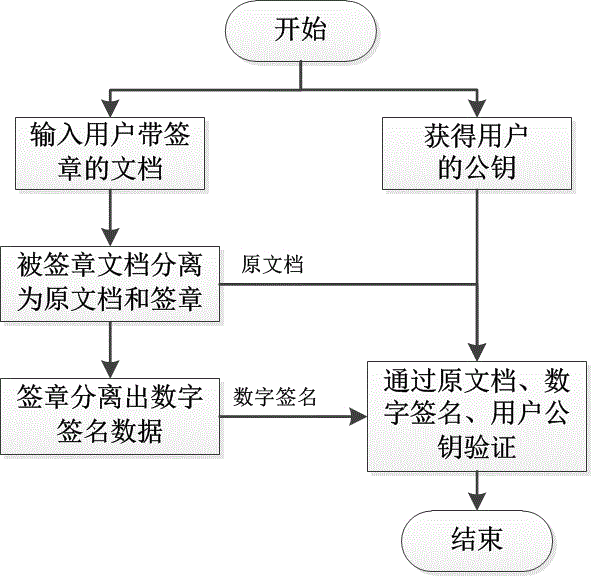
[0025] Such as figure 1 As shown in the figure, it is the process of the user signing a document in the scheme of the present invention. The present invention uses the user's private key and the signature pattern to sign the document requiring the user's visa, and the specific steps are as follows.
[0026] The document signed by the user can be a paper or electronic document, and the paper document can follow certain rules, and the information contained in it can be converted into an electronic document by means of electronic entry, and the scheme uses the user's private key to digitally sign the electronic document;
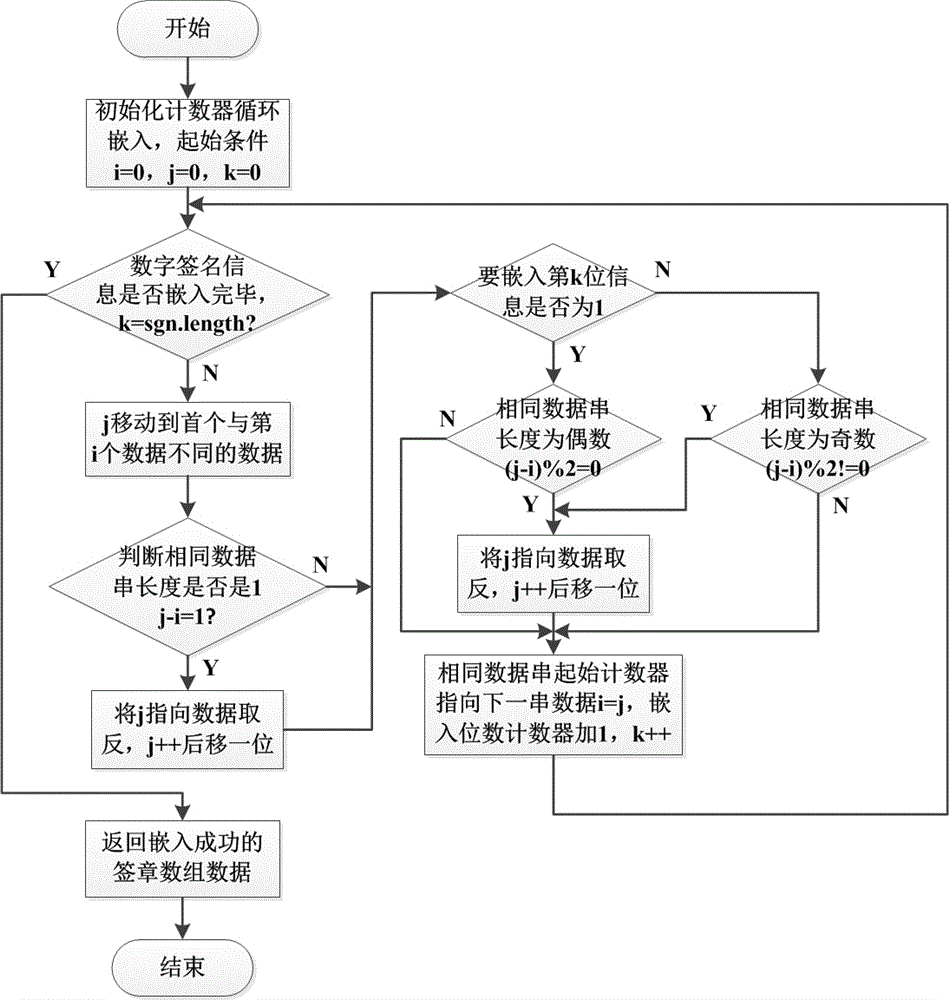
[0027] The user enters his signature or seal or logo as a binary image through input devices such as a mouse, tablet, and screen stylus, and judges whether the image can be embedded with the specified digital signature length...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com