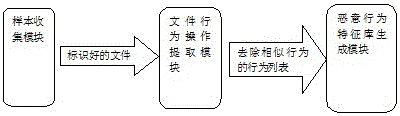
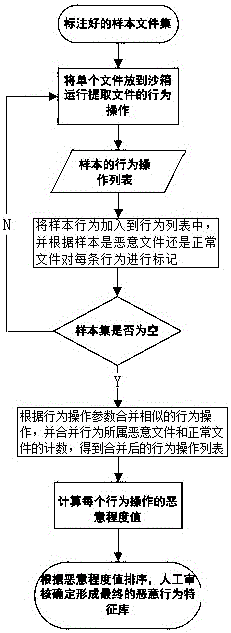
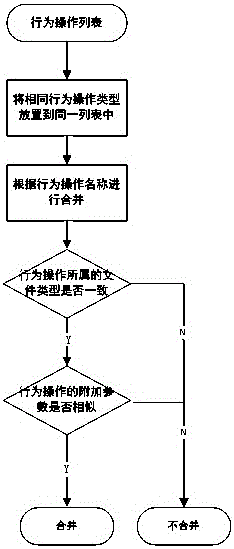
Malicious program behavior feature library construction method and device
A technology for malicious programs and construction methods, applied in computer security devices, instruments, electronic digital data processing, etc., can solve the problems of inability to detect new malicious programs, low efficiency, and low frequency of false positives.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0051] Embodiment 1: For example, 3 samples are collected, sample A and sample B are both malicious files, and sample C is a normal file. Put the sample set in the sandbox and run it to get the behavior operation list of each sample as follows:
[0052]Sample A Behavior Operation List 1:
[0053]
[0054] Sample B behavior operation list 2:
[0055]
[0056] Sample C Behavior Action List 3:
[0057]
[0058] Merge similar operation behaviors to get all operation behavior list 4 as follows:
[0059]
[0060] Count the sum of the total number of occurrences of all behavioral operations m=5
[0061] Calculate the maliciousness value for each behavioral action
[0062]
[0063] Sort according to the malicious degree value to get the following list of malicious behavior characteristics
[0064]
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com