A Distributed Terminal Access Control Method and Device
An access control and distributed monitoring technology, applied in transmission systems, electrical components, etc., can solve the problems that server equipment cannot provide normal business services, and the number of server equipment filtering rules is limited.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
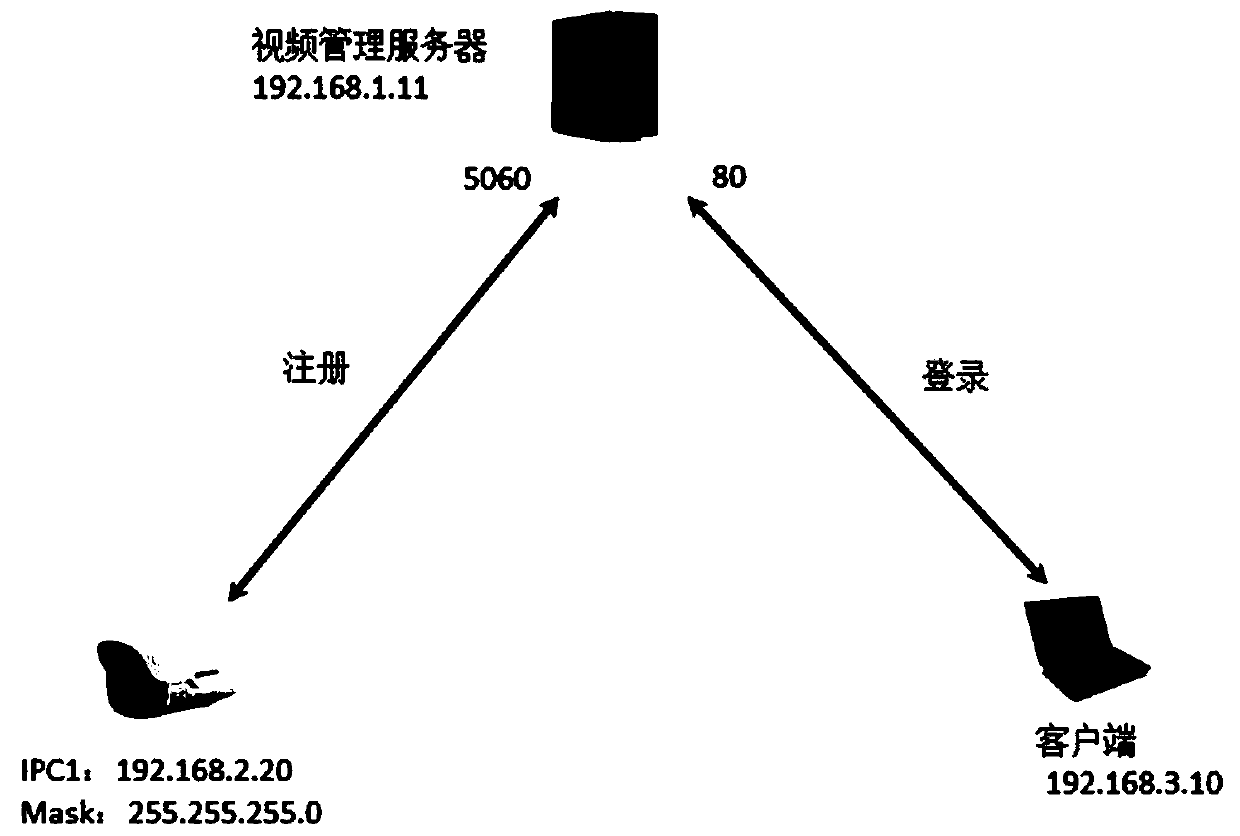
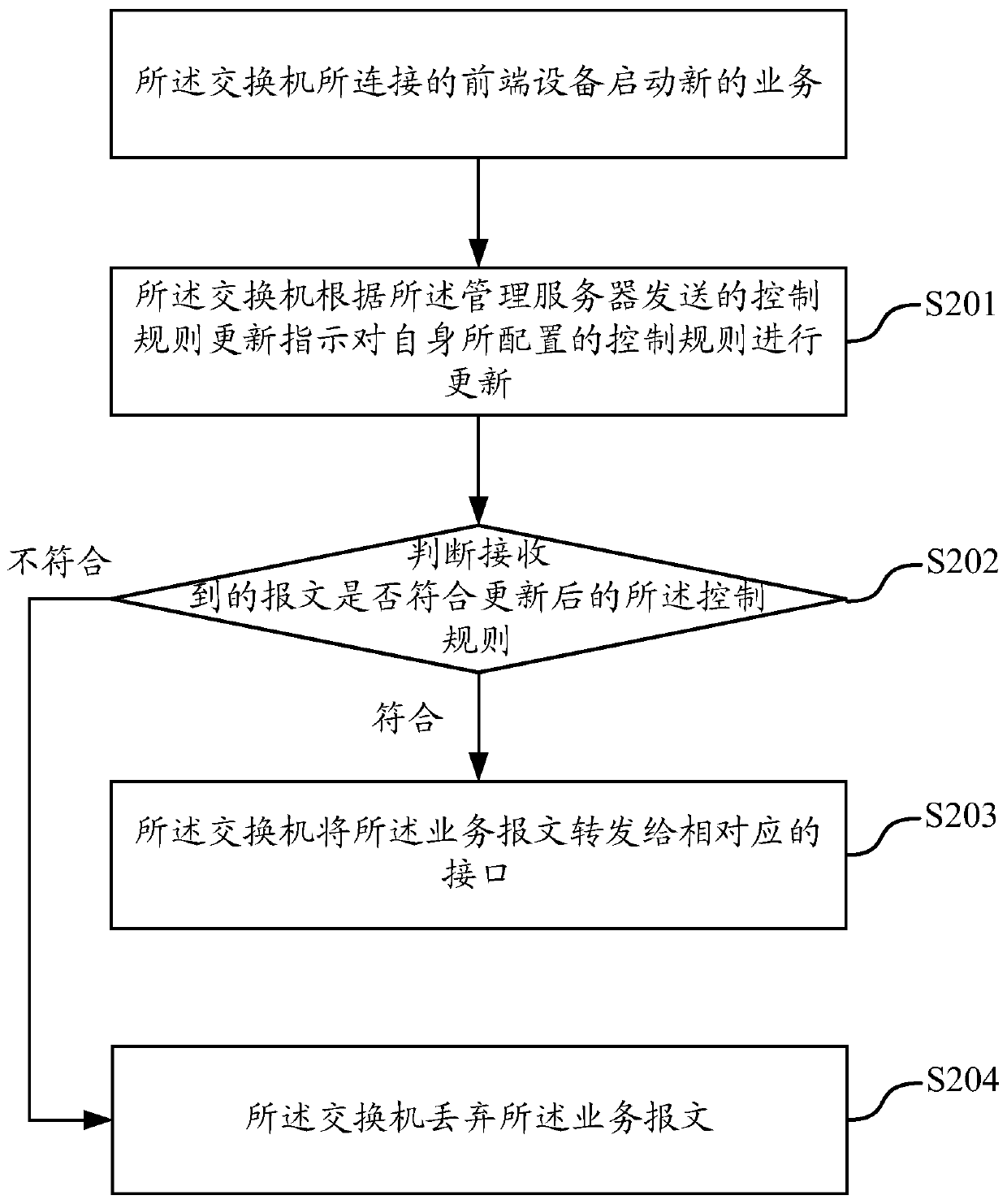
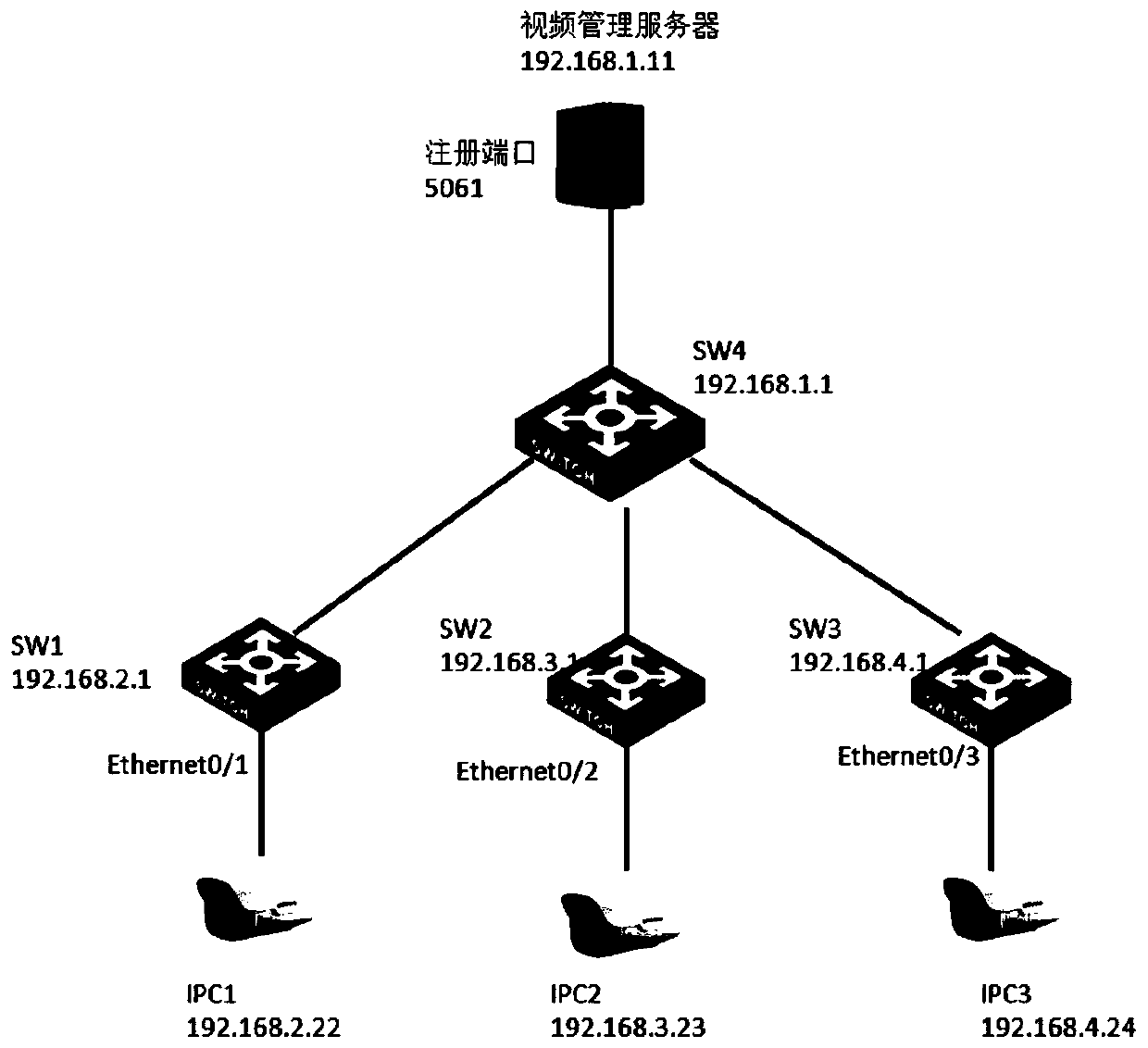
[0058] As stated in the background technology of this application, in the existing technology, the control rules are set on the server, and the corresponding filtering operations need to be processed by the server, which increases the processing burden of the server. Moreover, with the increase of front-end devices, the server The number of control rules that need to be configured has also increased significantly, which not only increases the processing capacity of the server for rule screening, but also, due to the limitation of the number of rules stored in the server itself, once the number of front-end rules requires too many rules, it will cause some control rules to fail. Configured on the server, the control strategy cannot be implemented.
[0059] The inventor of the present application hopes to use the method provided in this application to set corresponding control rules based on service types in each switch of the distributed monitoring system, and to update the corr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com