A security audit method and pc terminal
A security auditing and terminal technology, applied in the field of network security, can solve the problems of inability to perform auditing and monitoring
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
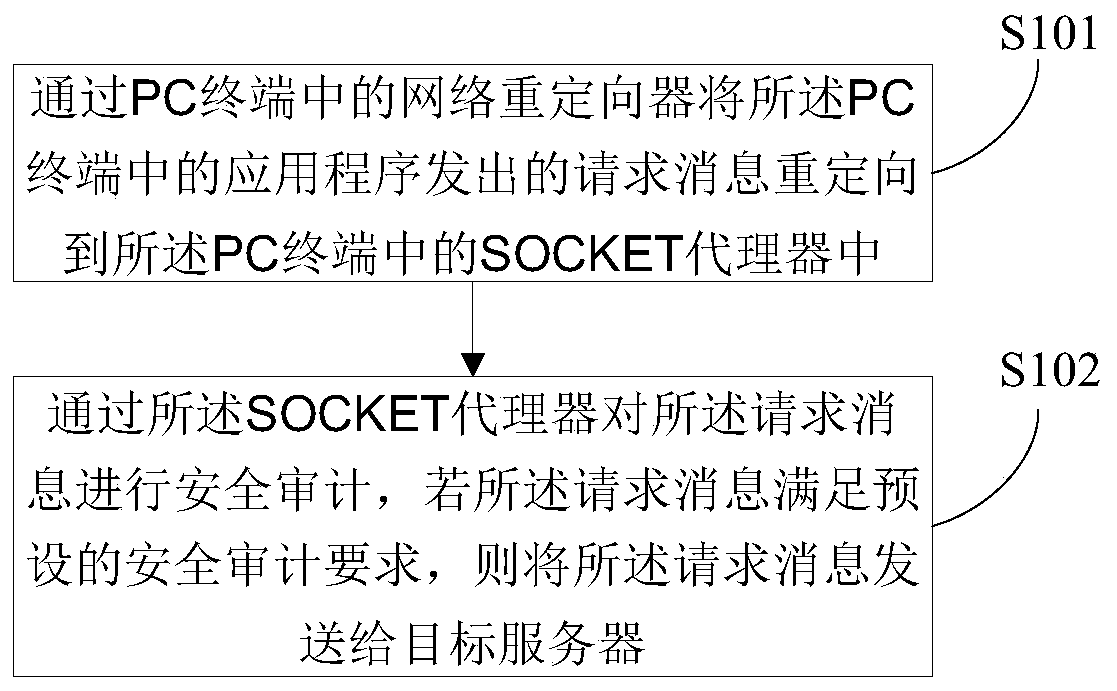
[0030] In the first embodiment of the present invention, a method for security auditing, such as figure 1 shown, including the following specific steps:
[0031] Step S101: Redirect the request message sent by the application program in the PC terminal to the SOCKET proxy in the PC terminal through the network redirector in the PC terminal.
[0032] Specifically, step S101 includes:
[0033] Intercepting the request message sent by the application program through the network redirector, modifying the original destination address in the request message to the interface address of the SOCKET proxy and sending it to the SOCKET proxy. The original destination address of the request message is modified to prevent the request message from being sent to the target server.
[0034] Step S102: Perform a security audit on the request message through the SOCKET proxy, and send the request message to a target server if the request message satisfies a preset security audit requirement. ...
no. 2 example
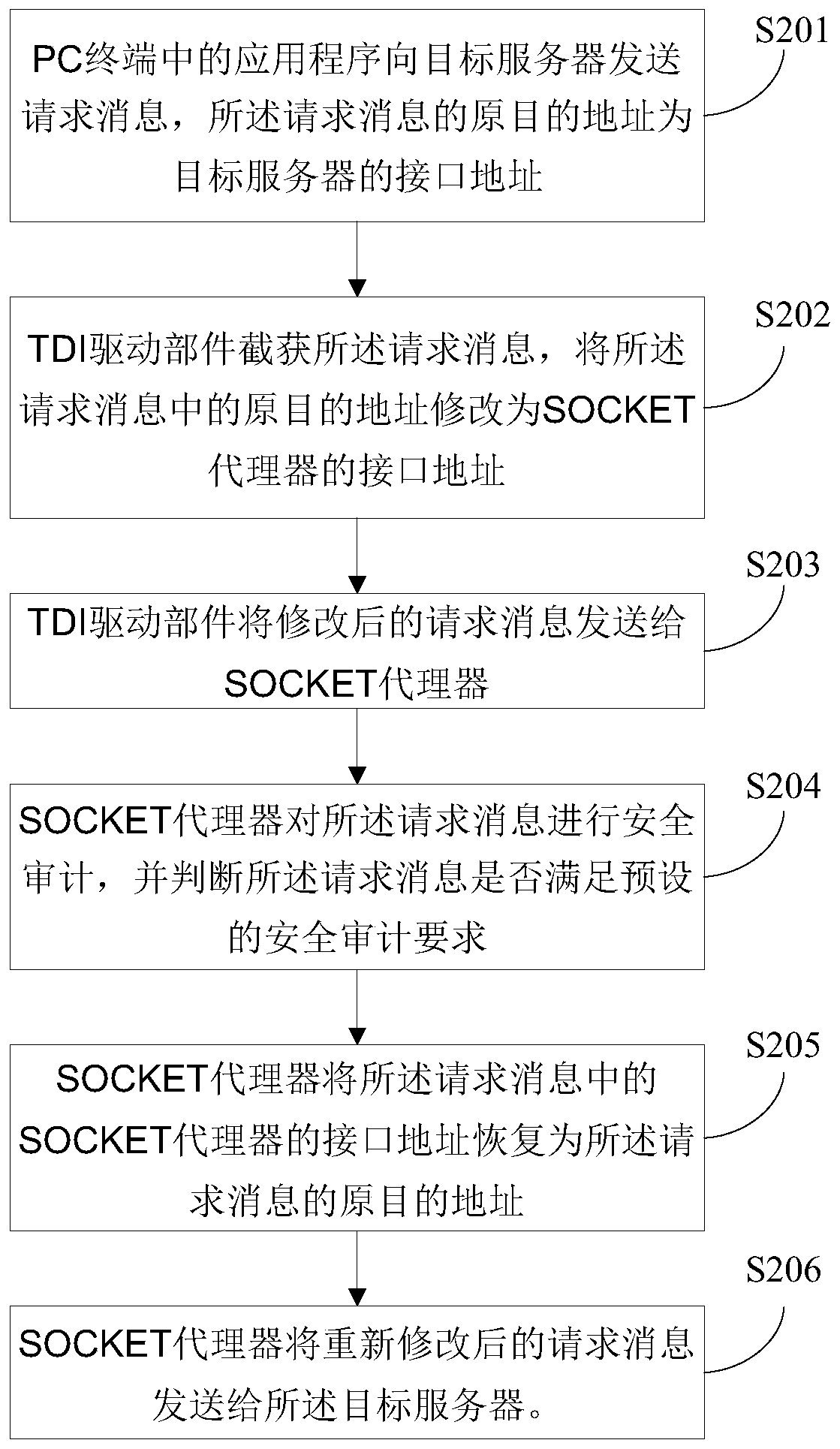
[0043] In the second embodiment of the present invention, a method for security auditing includes the following specific steps:
[0044] Step S201: the application program in the PC terminal sends a request message to the target server, and the original destination address of the request message is the interface address of the target server.
[0045] Step S202: The TDI (Transport Driver Interface, transmission driver interface) driver component intercepts the request message, and modifies the original destination address in the request message to the interface address of the SOCKET agent, thereby preventing the request message from being sent to the target server. The TDI driver component is equivalent to the network redirector in the first embodiment of the present invention, and is used to redirect application-level request messages to the SOCKET proxy.
[0046] Step S203: The TDI driver component sends the modified request message to the SOCKET agent.
[0047] Specificall...
no. 3 example
[0060] In the third embodiment of the present invention, a PC device, such as Figure 4 shown, including the following components:
[0061] 1) The network redirector 401 is used to redirect the request message sent by the application program in the PC terminal to the SOCKET proxy.
[0062] Specifically, the network redirector 401 is used for:
[0063] Intercepting the request message sent by the application program, modifying the original destination address in the request message to the interface address of the SOCKET agent and sending it to the SOCKET agent. The network redirector 401 prevents the request message from being sent to the target server by modifying the original destination address in the request message.
[0064] 2) SOCKET proxy 402, configured to perform security audit on the request message, and send the request message to the target server if the request message meets the preset security audit requirements.
[0065] Specifically, the SOCKET proxy 402 is u...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com