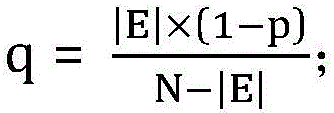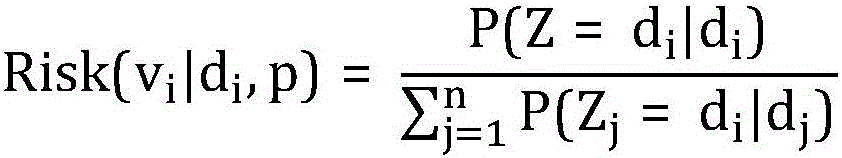Randomized privacy protection method for graph data release
A technology of randomizing privacy and graph data, which is applied in digital data protection, electronic digital data processing, computer security devices, etc., can solve the problems of data publishing privacy leakage, and achieve the effect of good probability distribution characteristics
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
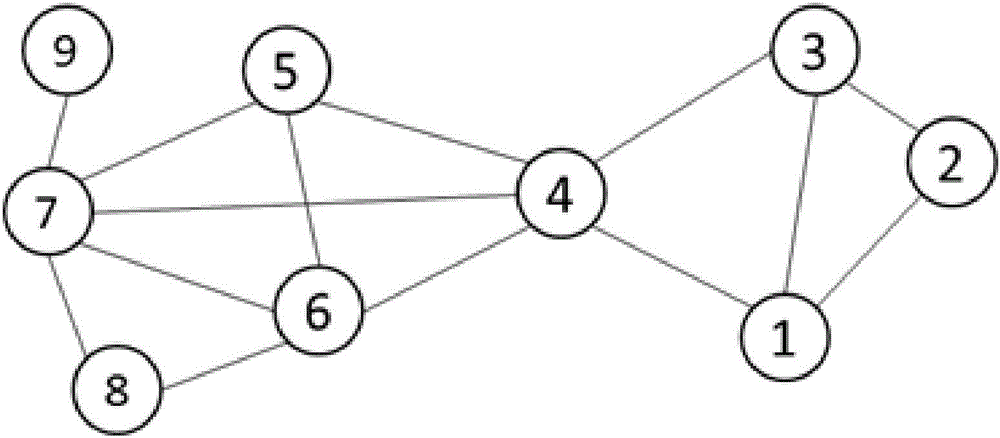
[0027] This embodiment takes figure 1 The original graph network data shown is taken as an example to illustrate the proposed randomized graph data publishing privacy protection method.
[0028] figure 1 The original graph data shown is simple undirected graph data G=(V, E), where V is an entity participating in the network, and E is a relationship between entities.
[0029] Adjacency matrices are commonly used in computers to store and process graph data. Adjacency matrix A=[a ij ] is an n×n 0-1 matrix, where when node v i and v j a ij = 1, otherwise a ij =0. figure 1 The original graph data shown, that is, the matrix of the adjacency matrix A corresponding to the graph data G is expressed as:
[0030]
[0031] The adjacency matrix A is a symmetric matrix, and each edge in the data corresponds to two symmetric non-zero entries in the matrix. In order to realize the random disturbance algorithm of the present invention, the upper triangular matrix B is introduced. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com