Method for communicating in a network comprising a virtual network, and a communication node comprising a virtual network entity
A technology of virtual network entities and communication nodes, which is applied in the field of communication in wireless networks and can solve problems such as interference performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
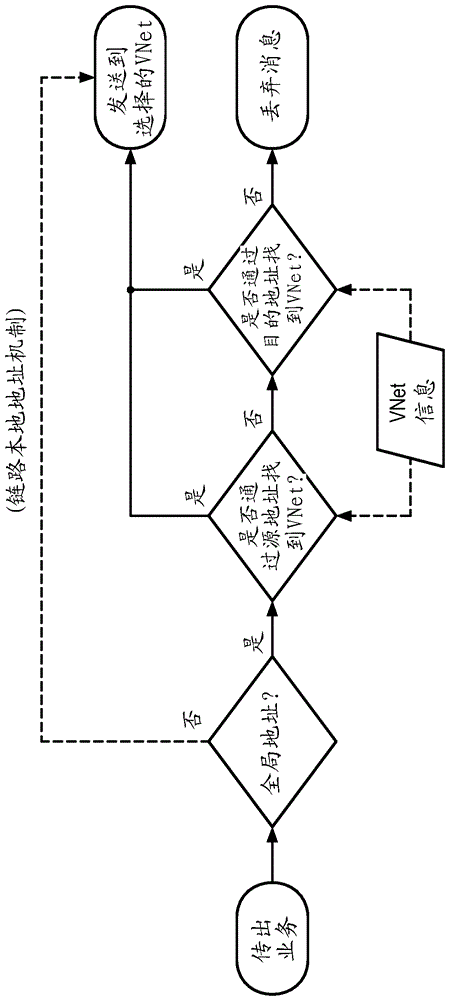
[0029] The invention relates to a network comprising a plurality of communication nodes. In an example of the invention, the network includes various applications linked to different services. Thanks to the embodiments of the invention described below, different services can reuse the infrastructure while maintaining logical isolation between them.
[0030] By way of illustration, embodiments of the invention which will now be described are aimed at the various following objectives.
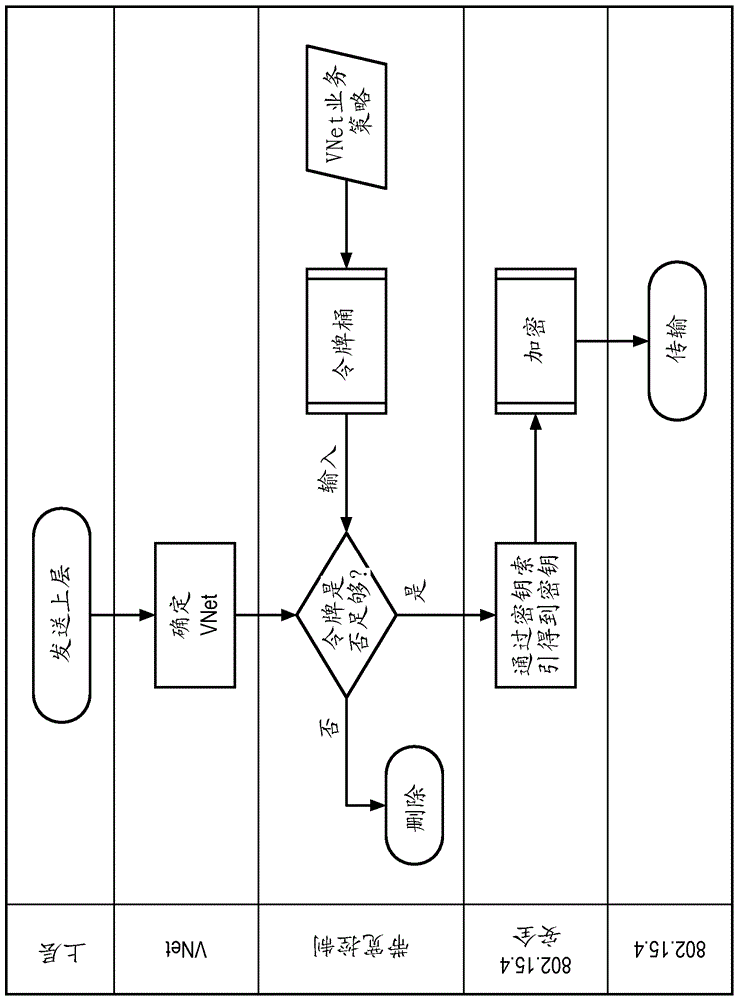
[0031] The first aspect addressed by these embodiments is the security of the network. As an example, the IEEE 802.15.4 security sublayer provides basic network security for other communication protocols. It is aimed at protecting against a wide range of cyber threats and situations that cause a network to fail or provide defective service that prevents it from functioning properly. In addition to the network security provided by the 6LoWPAN network security mechanism that ensures network-wide...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap