Long connection tunnel establishment method based on server hardware information
A hardware information and tunnel establishment technology, applied in the field of information security, can solve the problems of easy interception of transmitted data and hidden dangers of data security, and achieve the effect of ensuring the security of data transmission and improving the security of entry.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
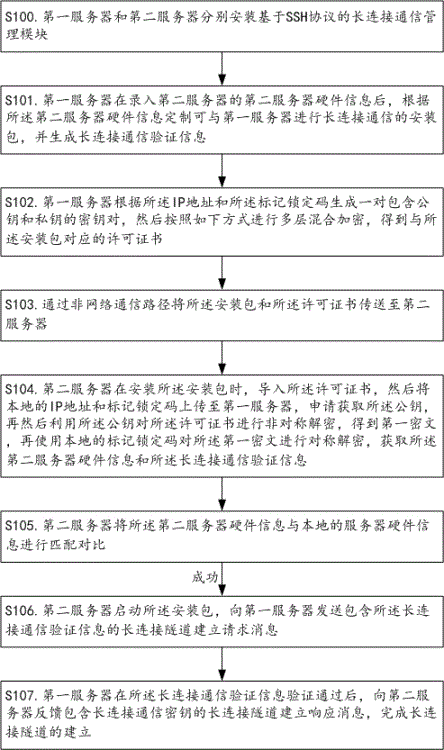
[0018] figure 1 A flow chart of the method for establishing a long connection tunnel based on server hardware information provided by the present invention is shown. The method for establishing a long connection tunnel based on server hardware information provided in this embodiment includes the following steps.
[0019] S101. After entering the second server hardware information of the second server, the first server customizes an installation package that can perform persistent connection communication with the first server according to the second server hardware information, and generates persistent connection communication verification information, the The second server hardware information includes the IP address and token lock code of the second server.
[0020] In the step S101, the first server and the second server are two servers that need to interact with each other. For example, when the first server is an authentication server, the second server is a business ser...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com