Safety device threat intelligence sharing method based on lightweight field body
A technology of domain ontology and security equipment, applied in the field of threat intelligence, it can solve problems such as the difficulty of interconnection and interoperability of threat intelligence information, the huge workload of information adaptation and transfer, and the consistency of the concept of threat intelligence interaction, so as to achieve scalability. The effect of strong sexual ability, strong conceptual consistency ability, and strong content correlation ability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] The present invention will be further described below in conjunction with the accompanying drawings.
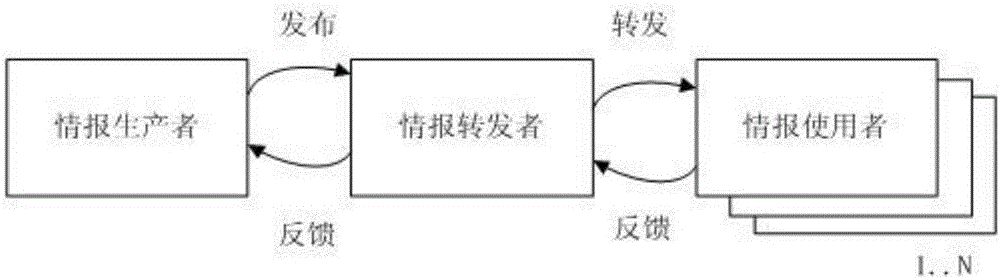
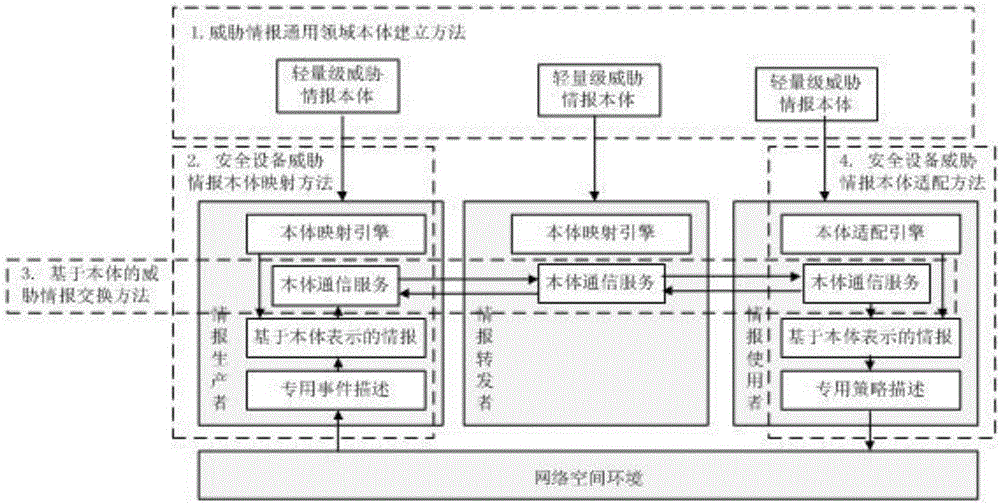
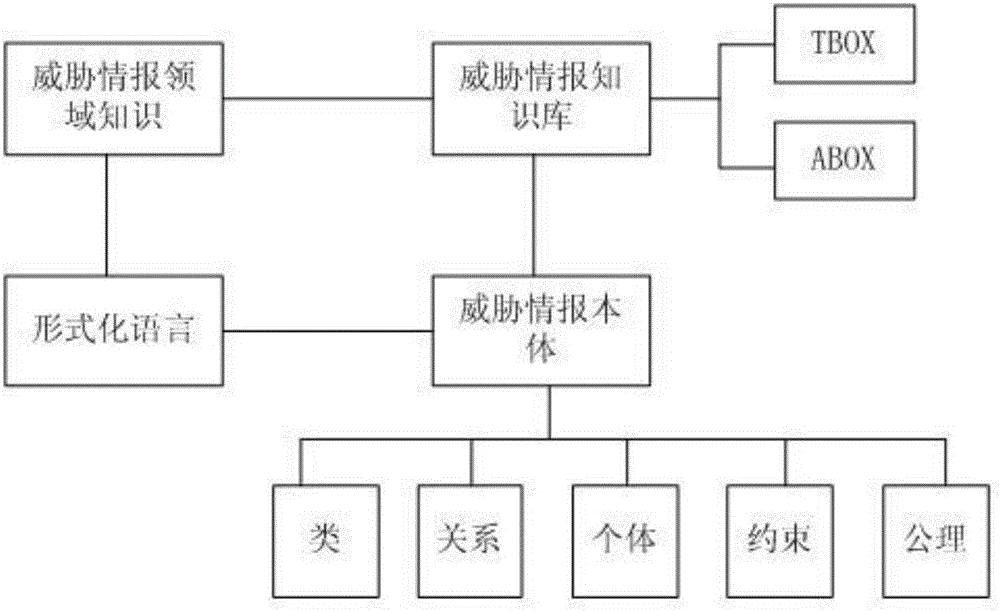
[0031] Such as figure 1 The overall framework of the present invention shown is composed of three different roles: information producer, information forwarder and information user. Intelligence producers are generally professional security analysis organizations that receive the information reported by the victim after the attacker launches an attack on information resources through the perception interface, and form intelligence and release it after processing, analysis, and arrangement; the producer is also responsible for detecting attacks. as well as the function of receiving and executing instructions from regulators. The intelligence forwarder is an ecological element that accurately collects, routes, and distributes intelligence information according to user needs, and transmits the user's demand feedback. The transmitter is generally composed of an intelligenc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com