A smart contract-based authentication authority evaluation method and device
A smart contract and authentication authority technology, applied in the field of identity authentication, can solve the problems that users cannot obtain authority in time, the application and review process is cumbersome, time-consuming and labor-intensive, etc., to improve credibility, reduce intentional or unintentional causes, and reduce security risks Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
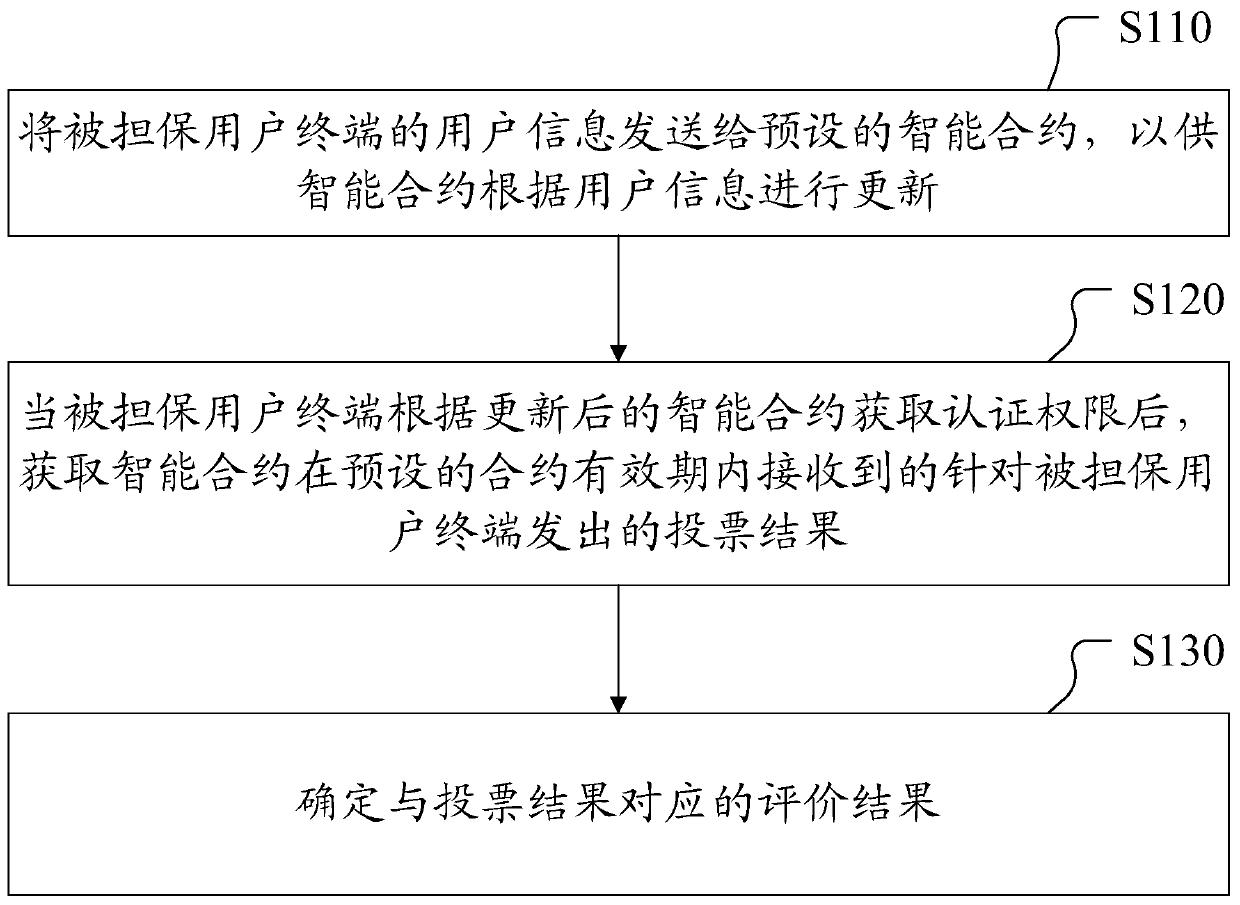
[0018] figure 1 It is a flow chart of a smart contract-based authentication authority evaluation method provided by Embodiment 1 of the present invention. Such as figure 1 As shown, the method includes:
[0019] Step S110: Send the user information of the guaranteed user terminal to the preset smart contract, so that the smart contract can be updated according to the user information.
[0020] In this step, the user terminal with identity authority (such as access control authority, login authority, etc.) acts as a guarantor and grants a certain temporary authority to the guaranteed user in the form of guarantee. After receiving the above information, the smart contract saves the above information To its own storage area, it is used in the steps of the guaranteed user terminal to apply for permission. Wherein, the user information includes at least the identity of the guaranteed user terminal, the identity of the guaranteed user terminal, and the content of the temporary au...
Embodiment 2
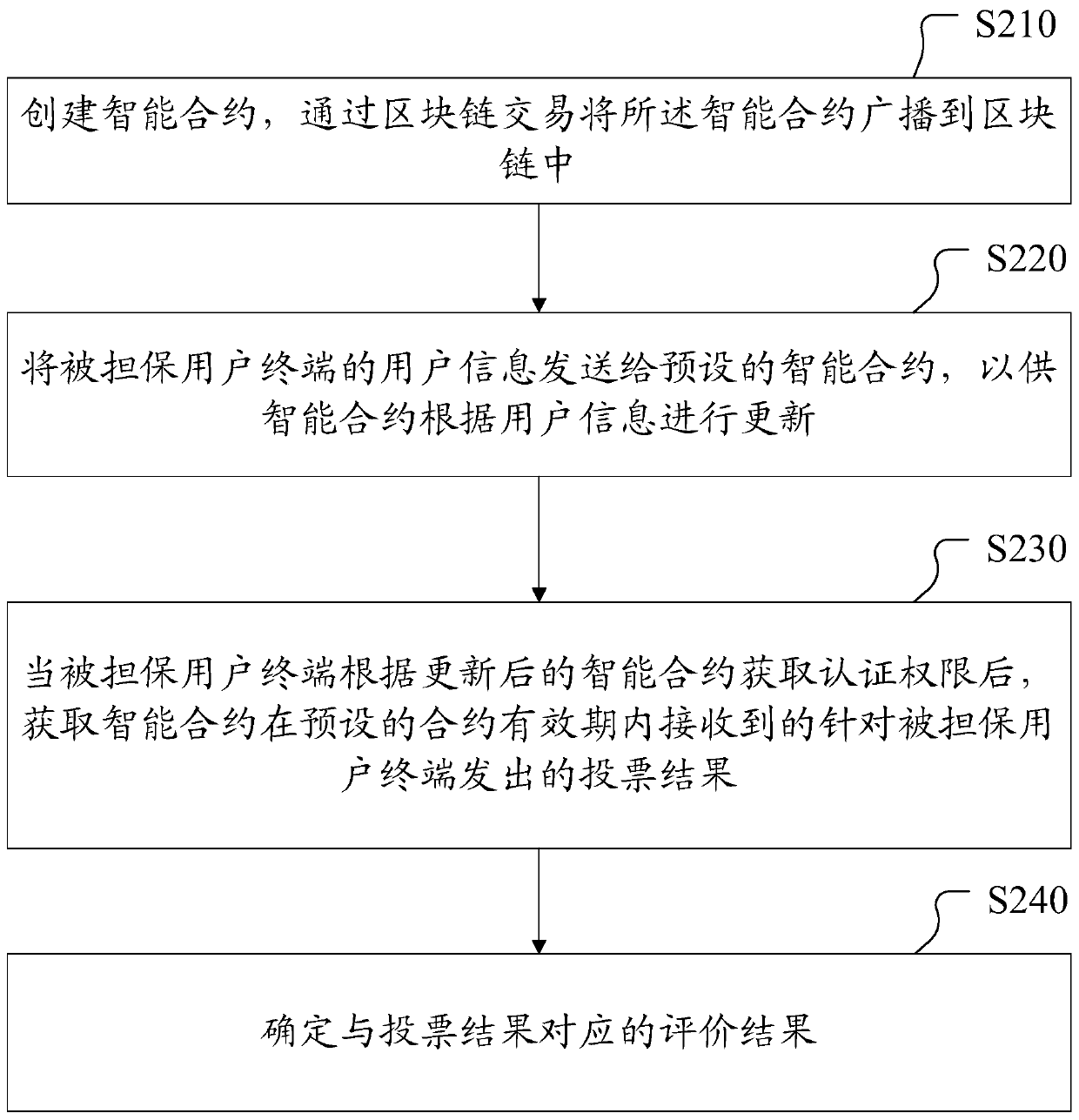
[0030] figure 2 It is a flow chart of a smart contract-based authentication authority evaluation method provided in Embodiment 2 of the present invention. The execution subject of the method may be a guarantee user terminal with identity authority in the blockchain network for realizing the guarantee function. Such as figure 2 As shown, the method includes:
[0031] Step S210: create a smart contract, and broadcast the smart contract to the blockchain through a blockchain transaction.
[0032] A smart contract is a collection of code and data that can automatically execute some functions driven by time or events. The smart contract combined with the blockchain can be deployed and run on the blockchain network. It has its own blockchain account and can automatically perform some functions under the drive of preset conditions, such as transmitting information between nodes and modifying the status of the blockchain such as account information. The biggest feature of smart ...
Embodiment 3
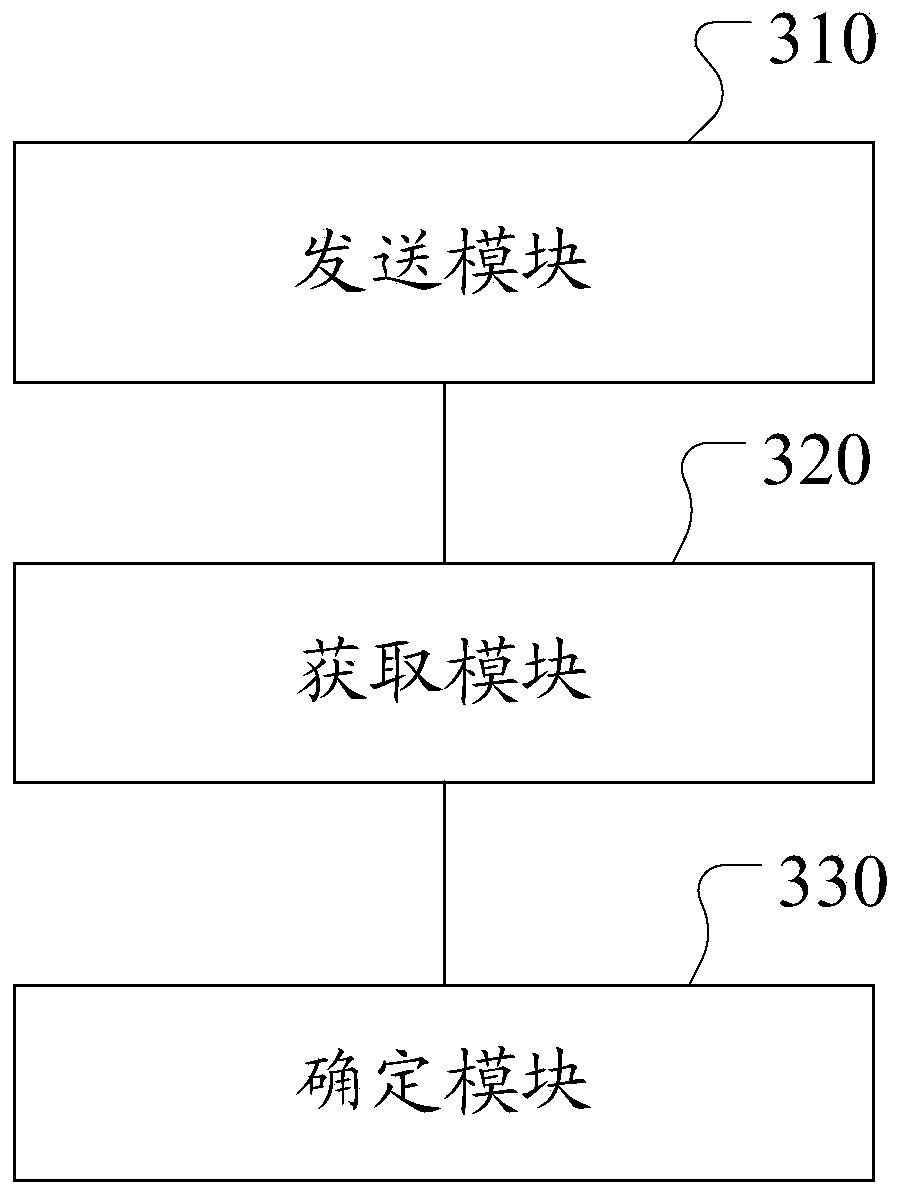
[0054] image 3 It is a schematic structural diagram of an authentication authority evaluation device based on a smart contract provided by Embodiment 3 of the present invention. Such as image 3 As shown, the device includes: a sending module 310 , an acquiring module 320 and a determining module 330 .
[0055] The sending module 310 is configured to send the user information of the guaranteed user terminal to a preset smart contract, so that the smart contract can be updated according to the user information.
[0056] A user terminal with identity authority (such as access control authority, login authority, etc.) acts as a guarantor and grants a certain temporary authority to the guaranteed user in the form of guarantee. The sending module 310 sends the above information to the smart contract, and the smart contract receives the above information. Afterwards, the above information is saved in its own storage area, and used for the operation of the guaranteed user terminal...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com