A WeChat forensics method and system based on data collision
A technology of data collision and WeChat, applied in the direction of digital transmission system, transmission system, digital data protection, etc., can solve the problems of unrecognizable, unable to obtain and analyze UID, unable to analyze and collect evidence of WeChat data, etc., to achieve high security and convenient decryption Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
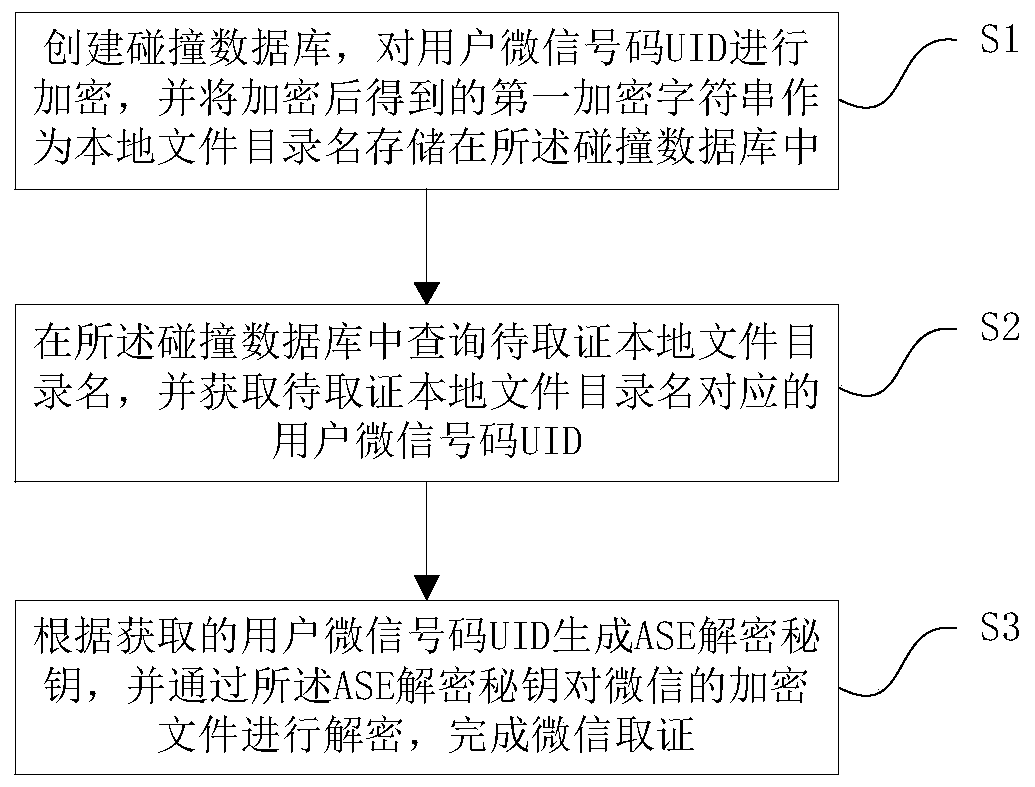
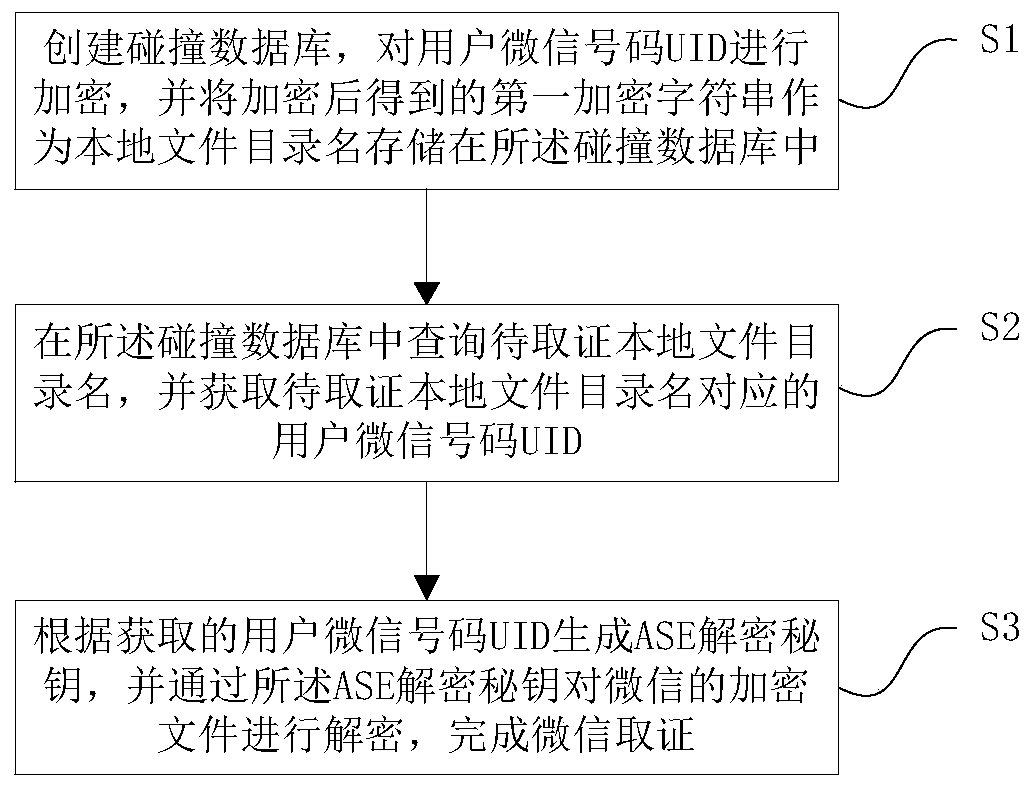
[0015] Embodiment 1. A WeChat forensics method based on data collision. The following will combine figure 1 A WeChat forensics method based on data collision in this embodiment is introduced in detail.
[0016] like figure 1 As shown, a WeChat forensics method based on data collision includes the following steps:
[0017] Step 1: Create a collision database, encrypt the UID of the user's WeChat ID, and store the first encrypted character string obtained after encryption as a local file directory name in the collision database;
[0018] Step 2: Query the directory name of the local file to be evidenced in the collision database, and obtain the UID corresponding to the directory name of the local file to be evidenced;
[0019] Step 3: Generate an AES decryption key according to the obtained user's WeChat code UID, and use the AES decryption key to decrypt the encrypted file of WeChat to complete WeChat evidence collection.
[0020] In this embodiment, in the step 1, the spec...
Embodiment 2
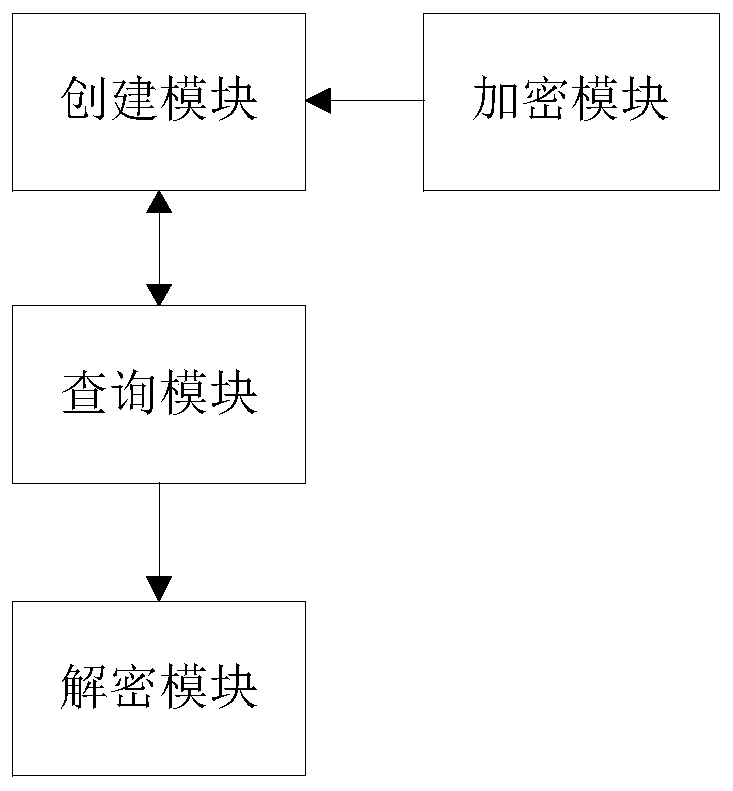
[0042] Embodiment 2. A WeChat forensics system based on data collision. The following will combine figure 2 A WeChat forensics system based on data collision in this embodiment is introduced in detail.
[0043] like figure 2 As shown, a WeChat forensics system based on data collision includes a creation module, an encryption module, a query module and a decryption module. The creation module is used to create a collision database; the encryption module is used for user micro-signal code UID to encrypt, and the first encrypted character string obtained after encryption is stored in the collision database as a local file directory name; the query The module is used to inquire about the local file directory name to be obtained in the collision database, and obtains the user micro-signal code UID corresponding to the local file directory name to be obtained; the decryption module is used to generate an AES decryption key according to the obtained user micro-signal code UID , ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com