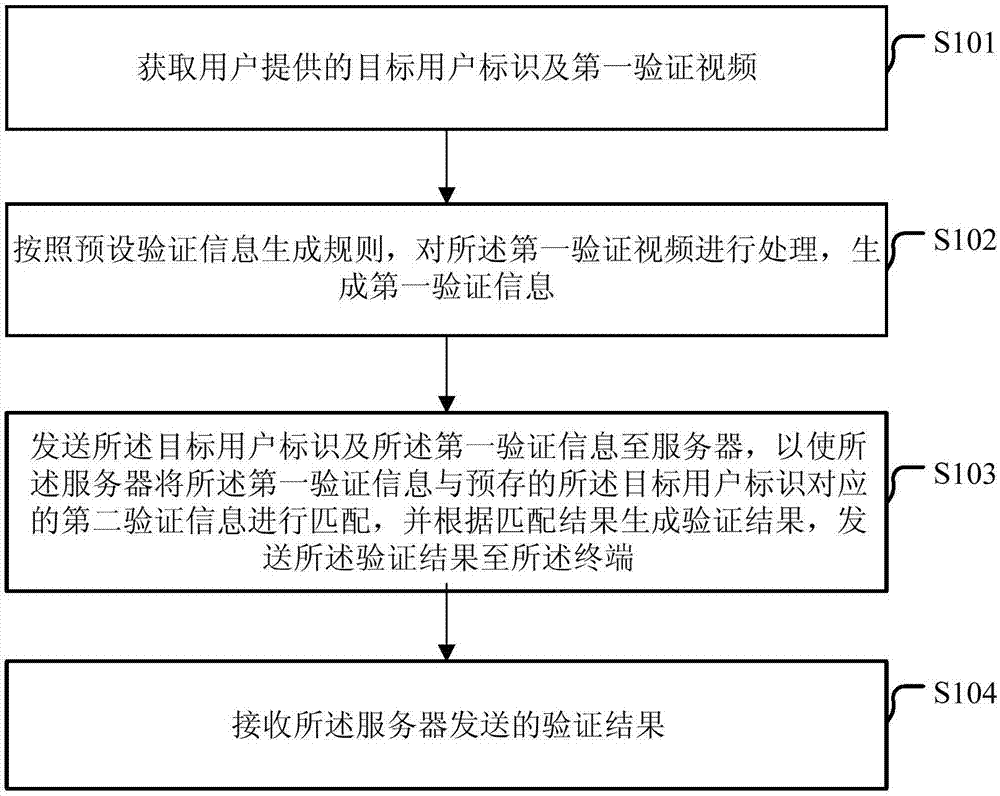
Login verification method and device
A technology for login verification and verification of information, which is applied in the field of network communication, and can solve problems such as simple character passwords, easy to remember passwords, high security, and low security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
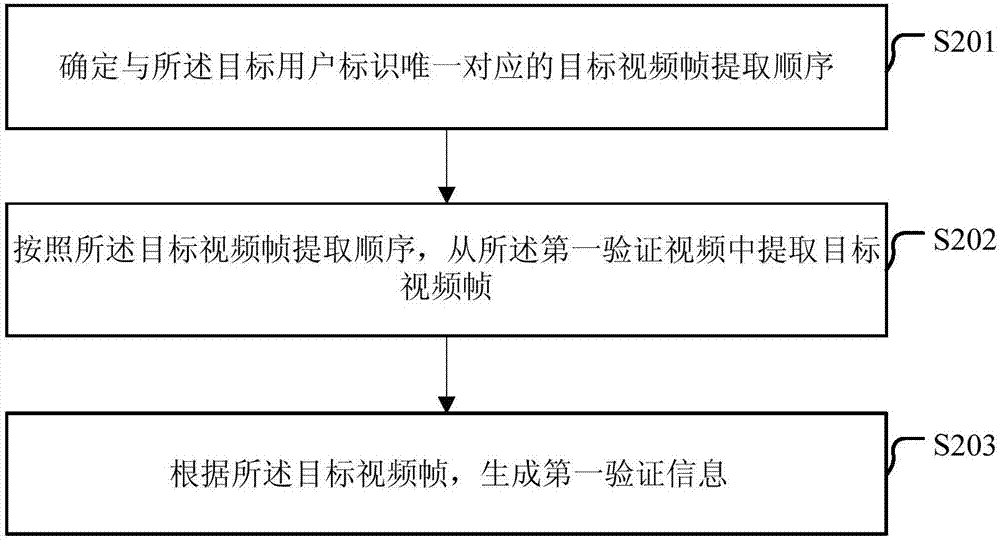
[0154] As an implementation manner of the embodiment of the present invention, the verification information generation module 520 may include:
[0155] Extraction sequence determination unit ( Figure 5 Not shown in ), used to determine the extraction sequence of the target video frame uniquely corresponding to the target user identifier;
[0156] Video frame extraction unit ( Figure 5 not shown in), for extracting target video frames from the first verification video according to the target video frame extraction sequence;
[0157] Verification information generation unit ( Figure 5 not shown in ), used to generate first verification information according to the target video frame.
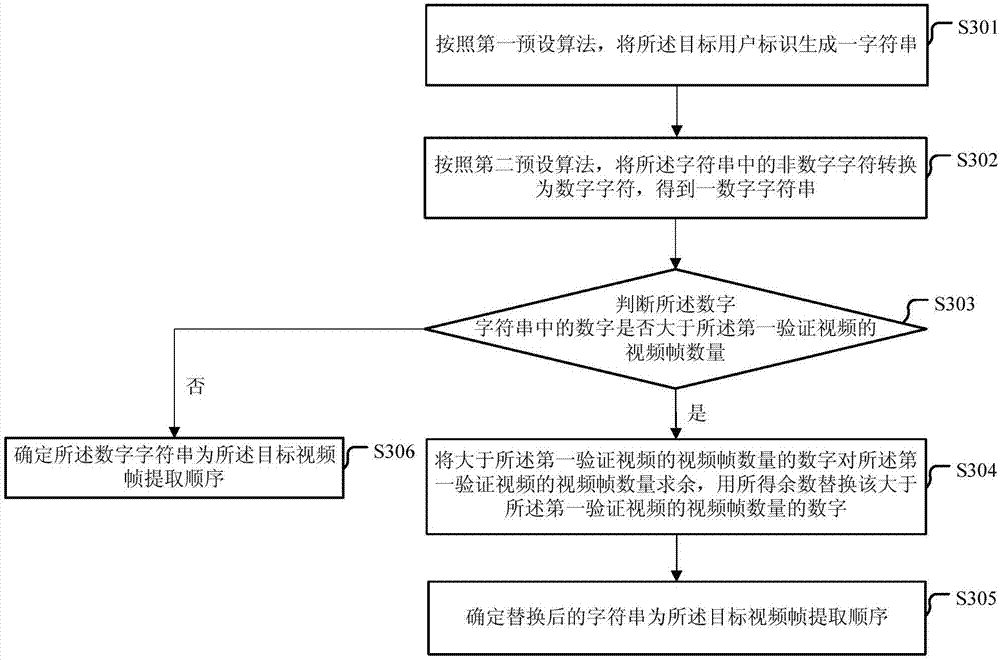
[0158] As an implementation manner of an embodiment of the present invention, the extraction order determination unit may include:
[0159] Find subunits ( Figure 5 not shown in ), for searching the target video frame extraction sequence corresponding to the target user identifier from th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com