A source location privacy protection method based on multi-phantom node strategy
A phantom node and privacy protection technology, applied in the network field, can solve the problem of poor effect of the source location privacy protection scheme, achieve the effects of optimizing transmission delay and routing energy consumption, enhancing practicability, and increasing security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach
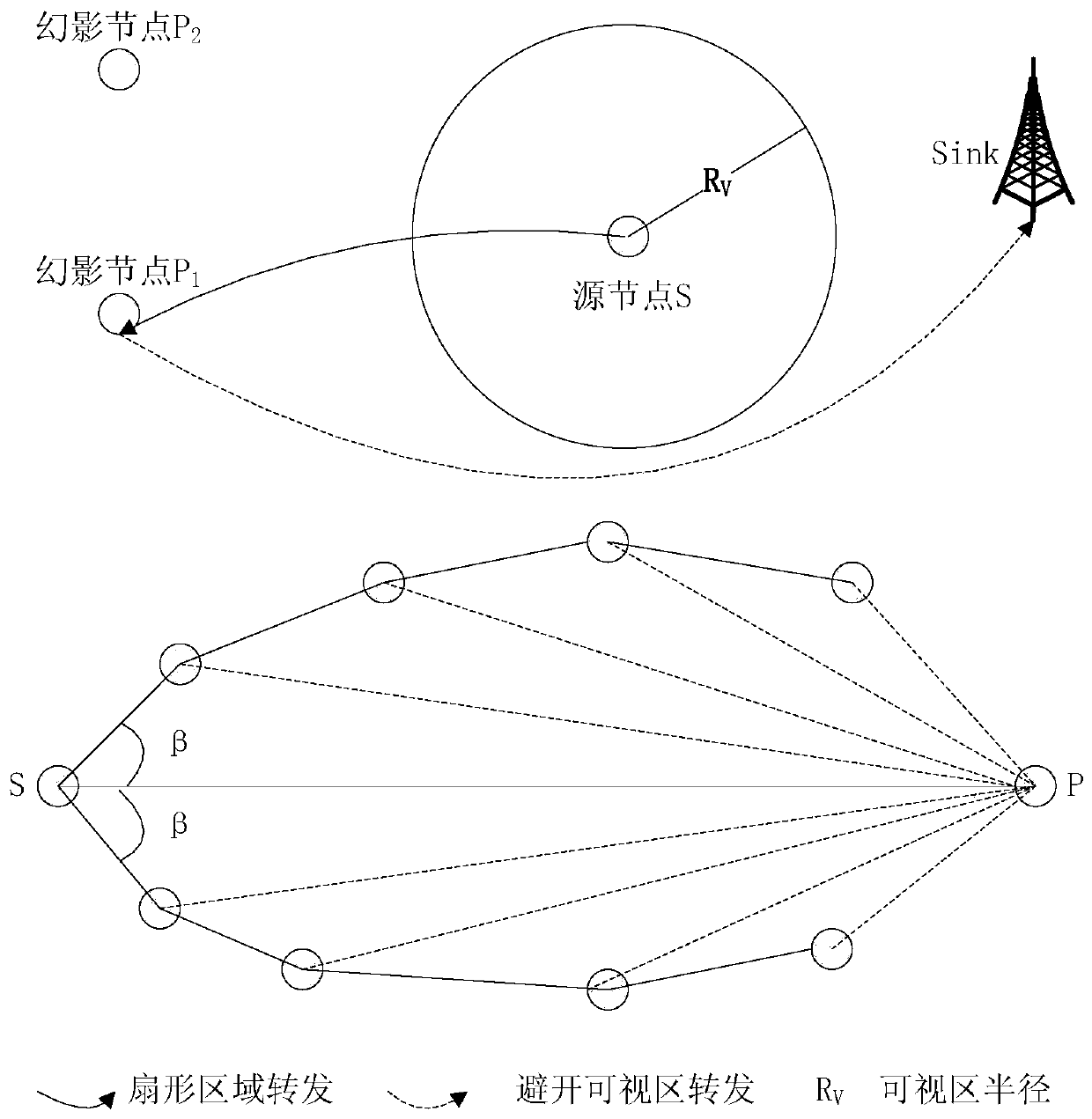
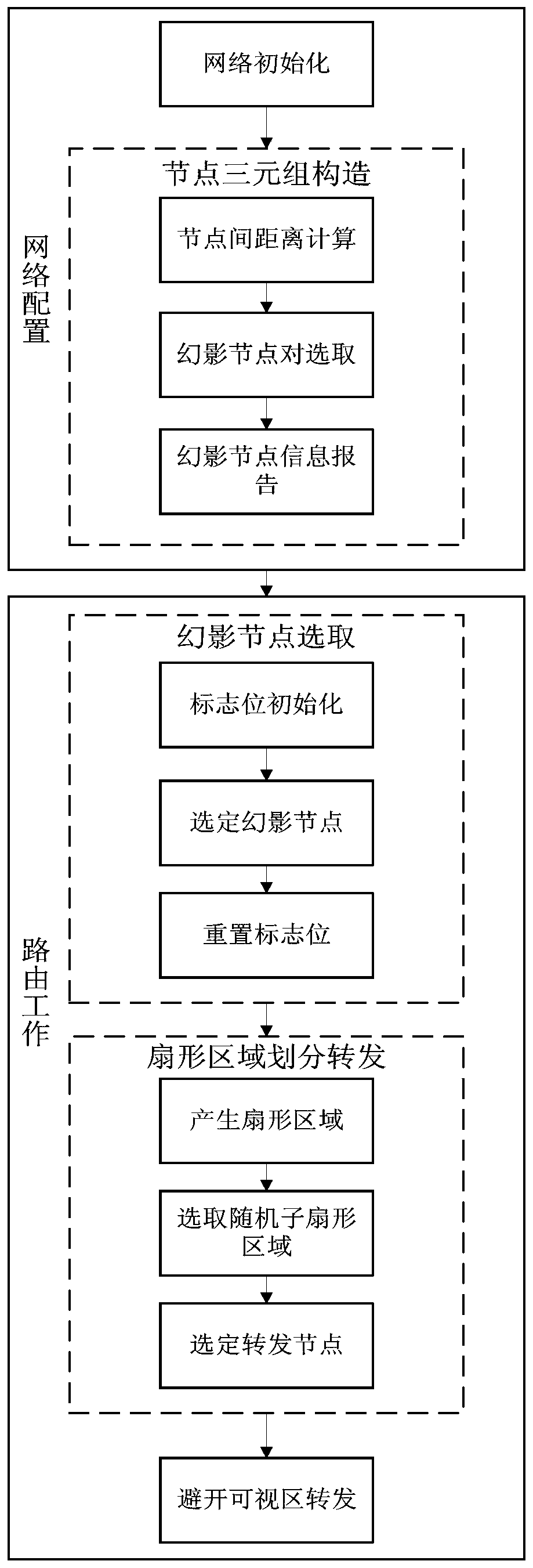
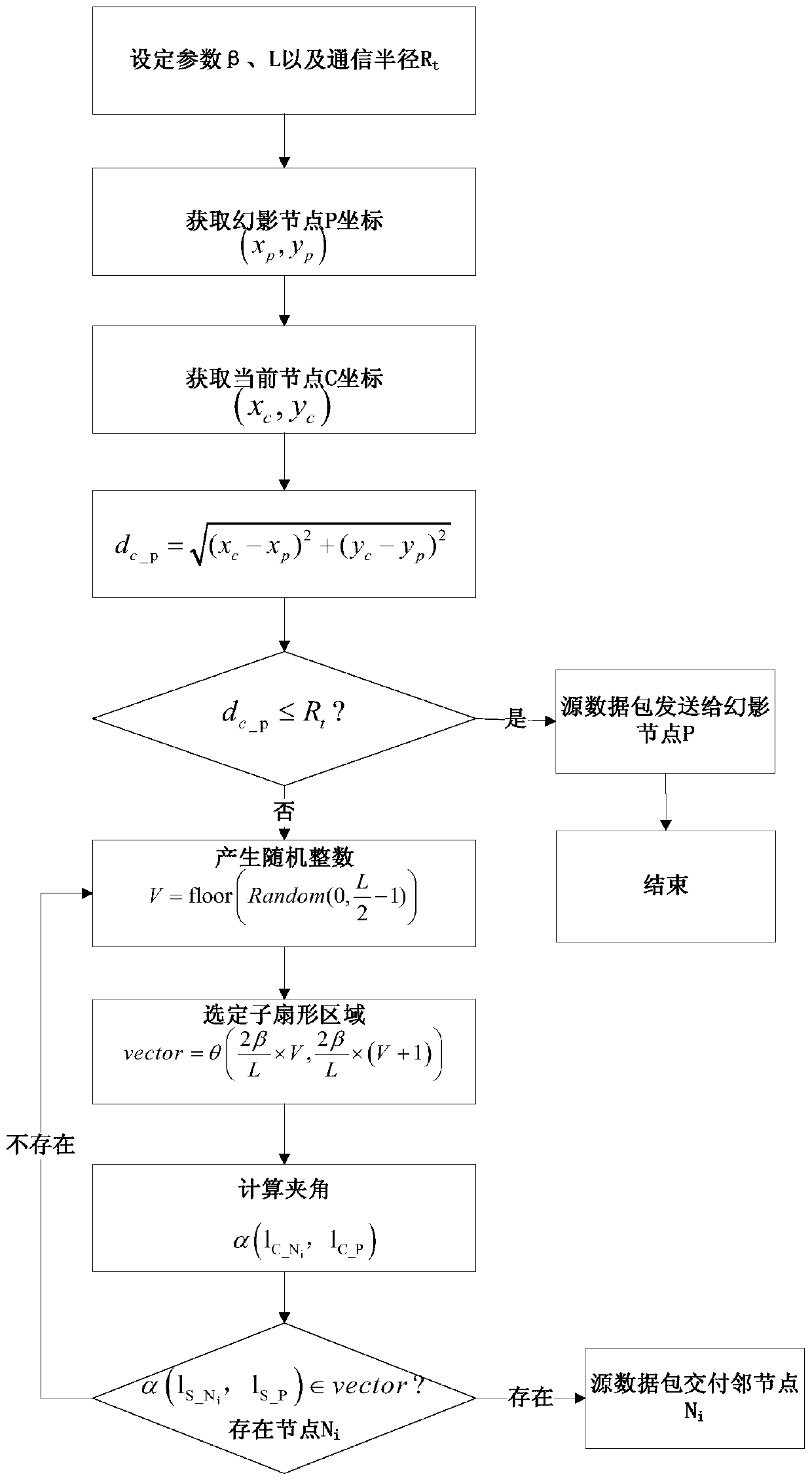
[0061] 3. The source node sends the source data packet to the phantom node to carry out the alternate selection process of the phantom node to ensure that the data packets of adjacent timing are sent to different phantom nodes, so as to increase the difficulty of the attacker's attack. The specific implementation method is:
[0062] Step 3.1: The network node internally stores a Boolean variable SelectFlag as a selection flag, which is set to FLASE during initialization.
[0063] Step 3.2: Before the source node starts to send the source data packet, judge the selection flag bit, if the flag bit is FALSE, select the phantom node 1 of the source node as the phantom node sending data in this round, and set the phantom node 1 ID is ID P1 and the position coordinates (x P1 ,y P1 ) into the data packet, set as the target phantom node ID and coordinates for this round of sending, and set the selection flag bit value to TRUE; if the flag bit is TRUE, select the phantom node 2 of t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com