Active defense method of network system based on vulnerability correlation analysis
A network system and active defense technology, applied in the field of information security, can solve problems such as inaccurate vulnerability classification results, network explosion, and limiting the practicability of attack graph generation tools
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0070] The technical solutions of the present invention will be described in detail below in conjunction with the accompanying drawings and embodiments.
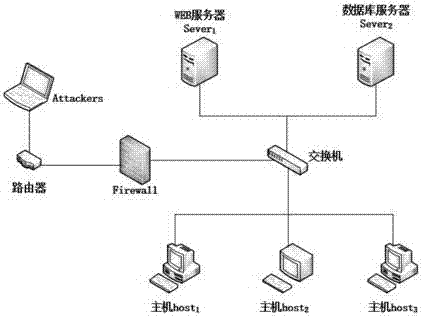
[0071] The network topology in this embodiment is as follows figure 1 shown. In this network system, the firewall separates the LAN from malicious visitors, and the WEB server Server 1 , database server Server 2 , host host 1 , host host 2 with the host host 3 Connected through a switch and can share information in a certain way.
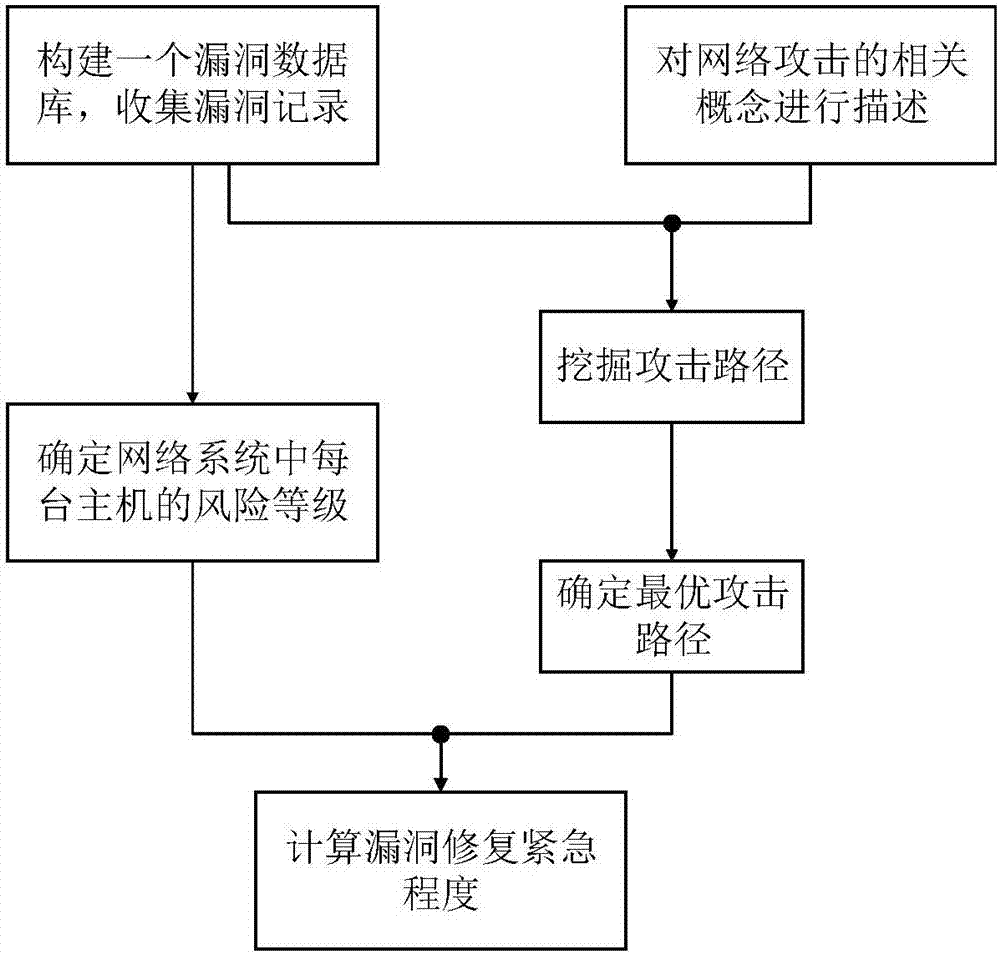
[0072] Use the method proposed by the present invention to build a network system active defense strategy, and its operation process is as follows figure 2 As shown, specifically:
[0073] Step 1. Build a vulnerability database and collect vulnerability records.
[0074] Select the National Vulnerability Database (National Vulnerability Database, NVD) as the data source to build a vulnerability database.
[0075]The vulnerability database includes: Common Vulnerabilities and Exposures (...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com