Method and system for real-time detection of communication fraud base on suspicious behavior recognition
A real-time detection and communication technology, applied in speech recognition, wireless communication, telephone communication, etc., can solve the problems of lack of anti-communication fraud, uneven level of cultural accomplishment, and affecting the normal development of the telecommunications industry
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] Below in conjunction with accompanying drawing, further describe the present invention through embodiment, but do not limit the scope of the present invention in any way.
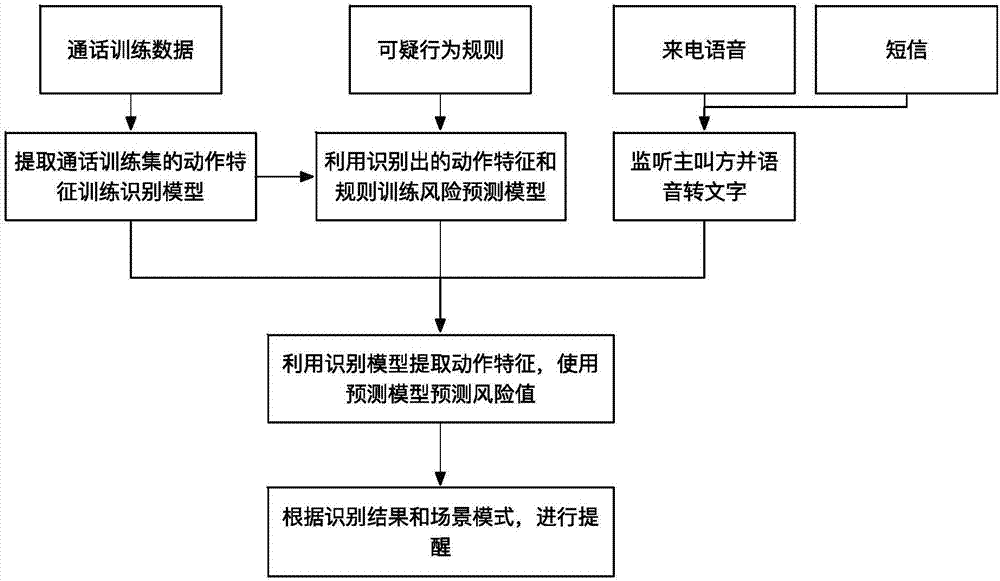
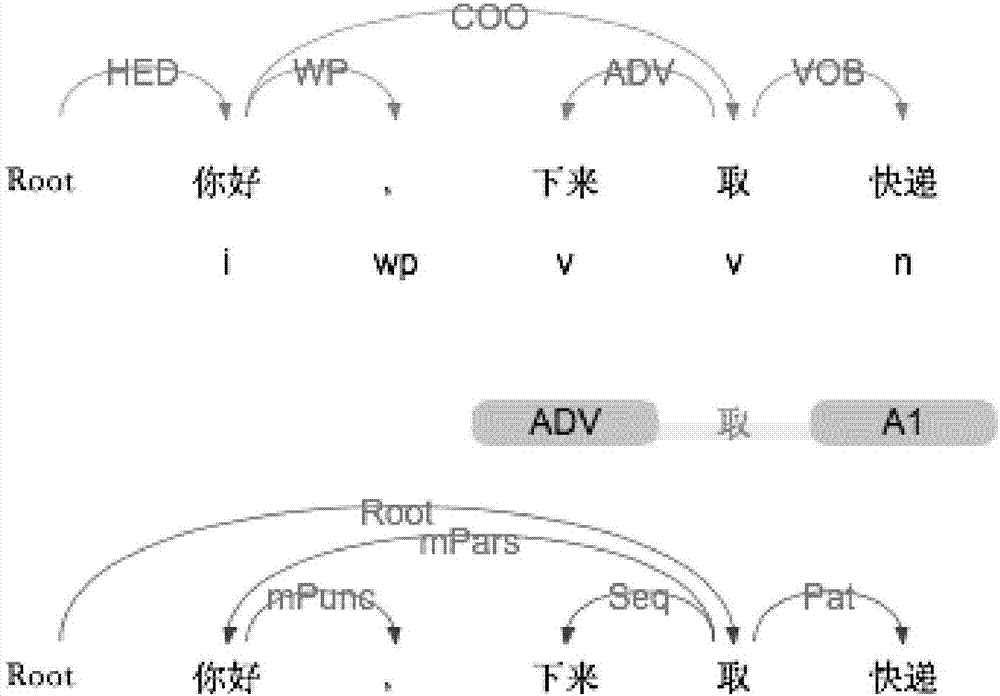
[0045] The present invention provides a method for preventing communication fraud based on suspicious behavior recognition. By identifying call voice and short message content, and using natural language processing technology to extract the action behavior characteristics of the caller's voice, each behavior characteristic is represented by a triplet Formally expressed, all behavioral characteristics in the call will be identified for suspicious behaviors one by one and the corresponding risk prediction score will be calculated, and the detection and reminder of communication fraud will be realized through this score.
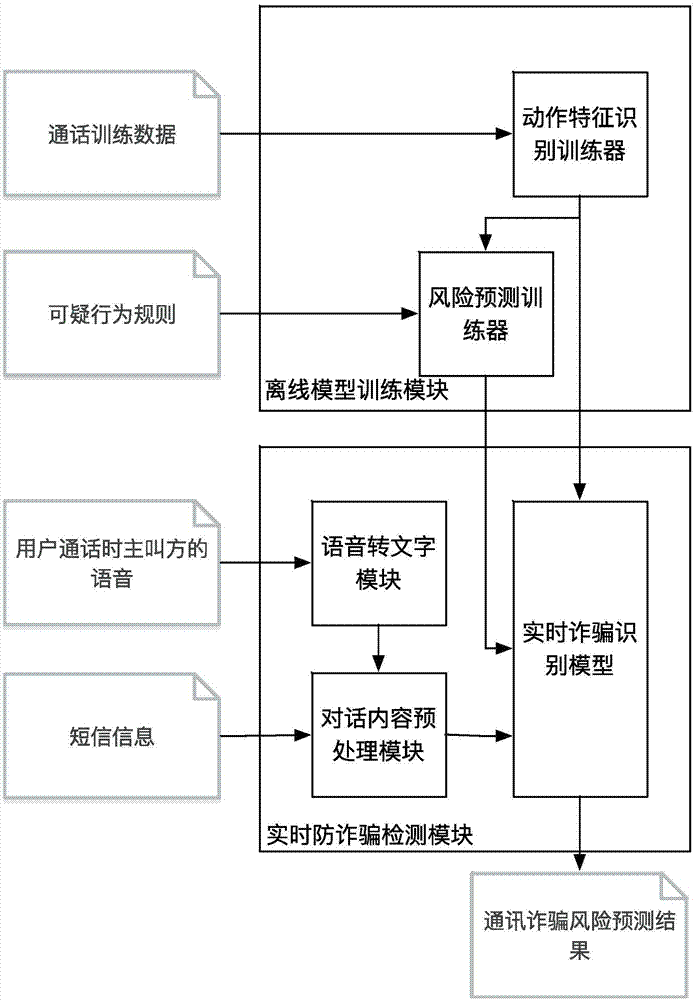
[0046] figure 1 It is a flow chart of a communication fraud prevention method based on suspicious behavior identification; figure 2 It is a structural block diagram of a communicati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com