Method and system for decryption of user terminal
A user terminal and user technology, applied in the field of mobile communication, can solve the problem of time-consuming, labor-intensive and insecure decryption, and achieve the effect of saving unlocking time, ensuring security, and ensuring data security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
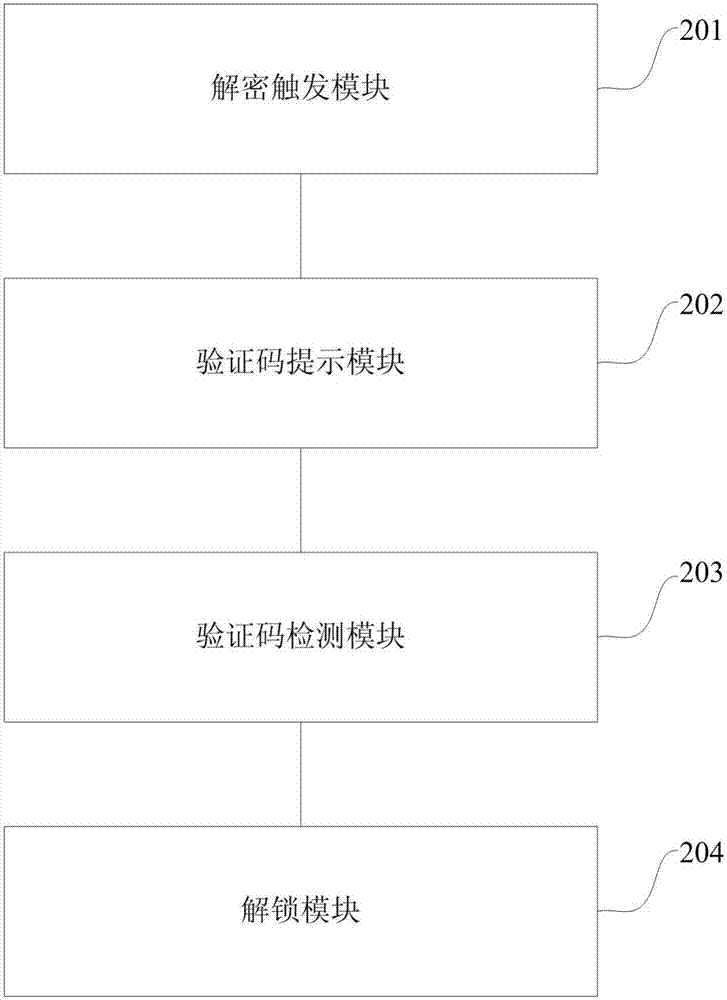
[0038] Embodiment 1 of the present invention provides a decryption method for a user terminal, such as figure 1 Shown is the flowchart of the first embodiment of the present invention, specifically including,
[0039] Step S101, when the user forgets the user terminal password, the user terminal prompts the user to decrypt, and receives the user's start decryption instruction to start decryption;
[0040] As an embodiment, when the user forgets the password of the user terminal, the words "forgot password" are displayed on the lock screen interface of the user terminal to prompt the user to click, and the decryption starts after receiving the user's click instruction.
[0041] Step S102, the user terminal internally generates verification code information, and prompts the user for the verification code information;
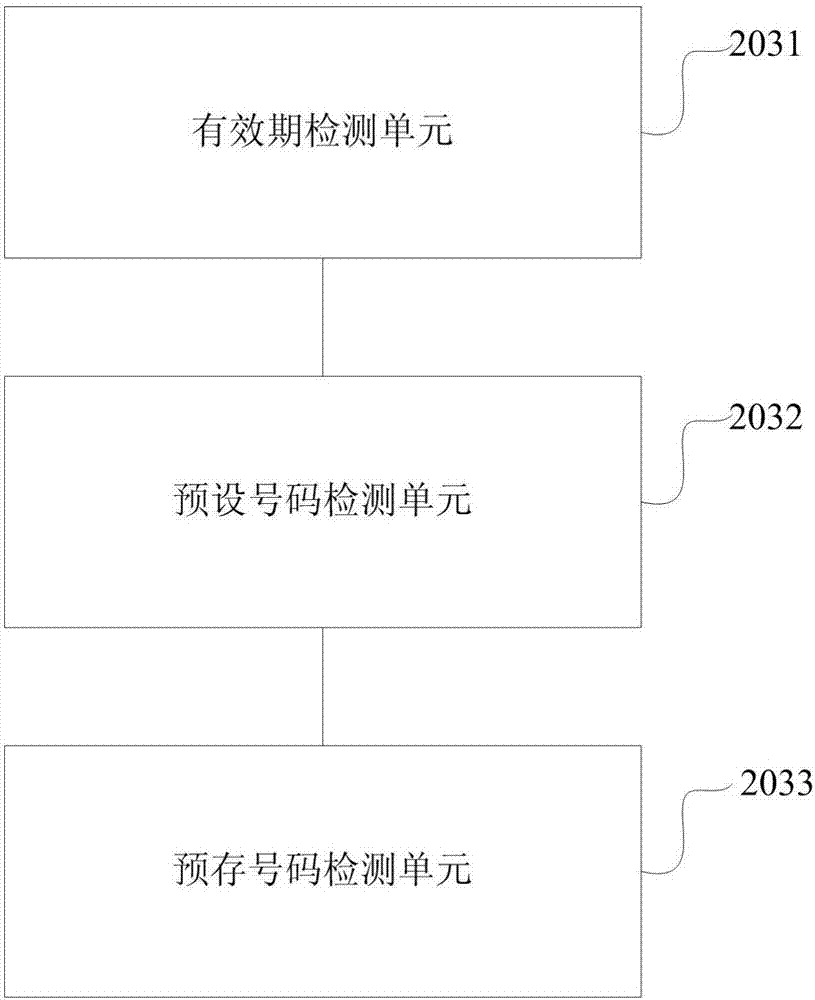
[0042] As an example, the verification code information generated inside the user terminal is a random digital verification code, and different algorithms may be...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com