Method, device and system for unlocking mobile terminal by network operator
A mobile terminal, operator technology, applied in the field of communication, can solve problems such as poor security, achieve the effect of improving satisfaction, speeding up, and simplifying the unlocking process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
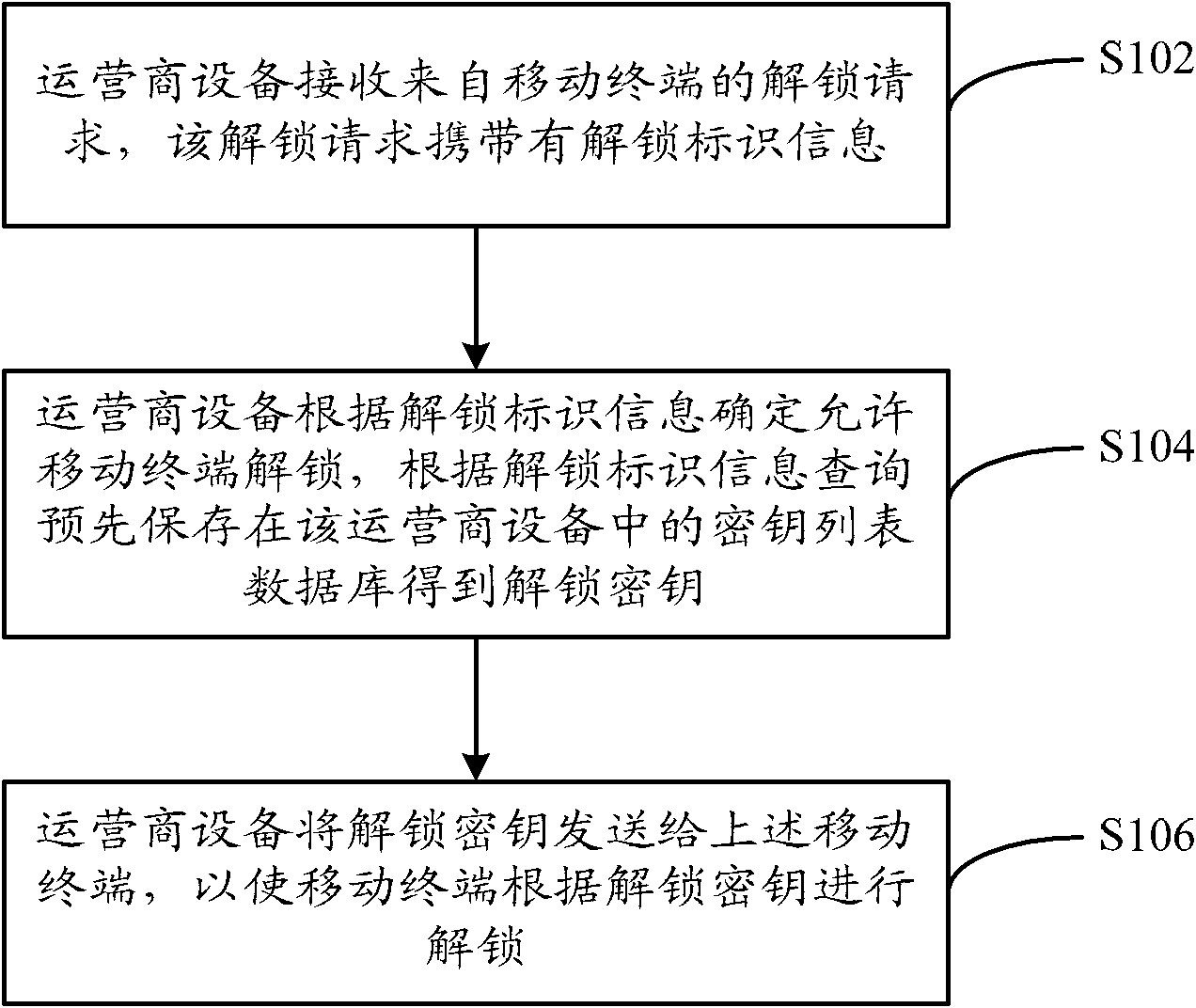
[0025] This embodiment provides a method for an operator to unlock a mobile terminal, see figure 1 , the method includes the following steps:
[0026] Step S102, the operator equipment receives an unlock request from the mobile terminal, and the unlock request carries unlock identification information;
[0027] Wherein, the operator equipment can receive the unlocking request from the mobile terminal in one of the following ways: SMS, USSD (Unstructured Supplementary Service Data, Unstructured Supplementary Service Data) or WAP (Wireless Application Protocol, Wireless Application Protocol) way.
[0028] Step S104, the operator equipment determines that the mobile terminal is allowed to unlock according to the unlock identification information, and queries the key list database pre-stored in the operator equipment according to the unlock identification information to obtain the unlock key;
[0029] The key list database pre-stored in the operator's equipment can be obtained in...
Embodiment 2
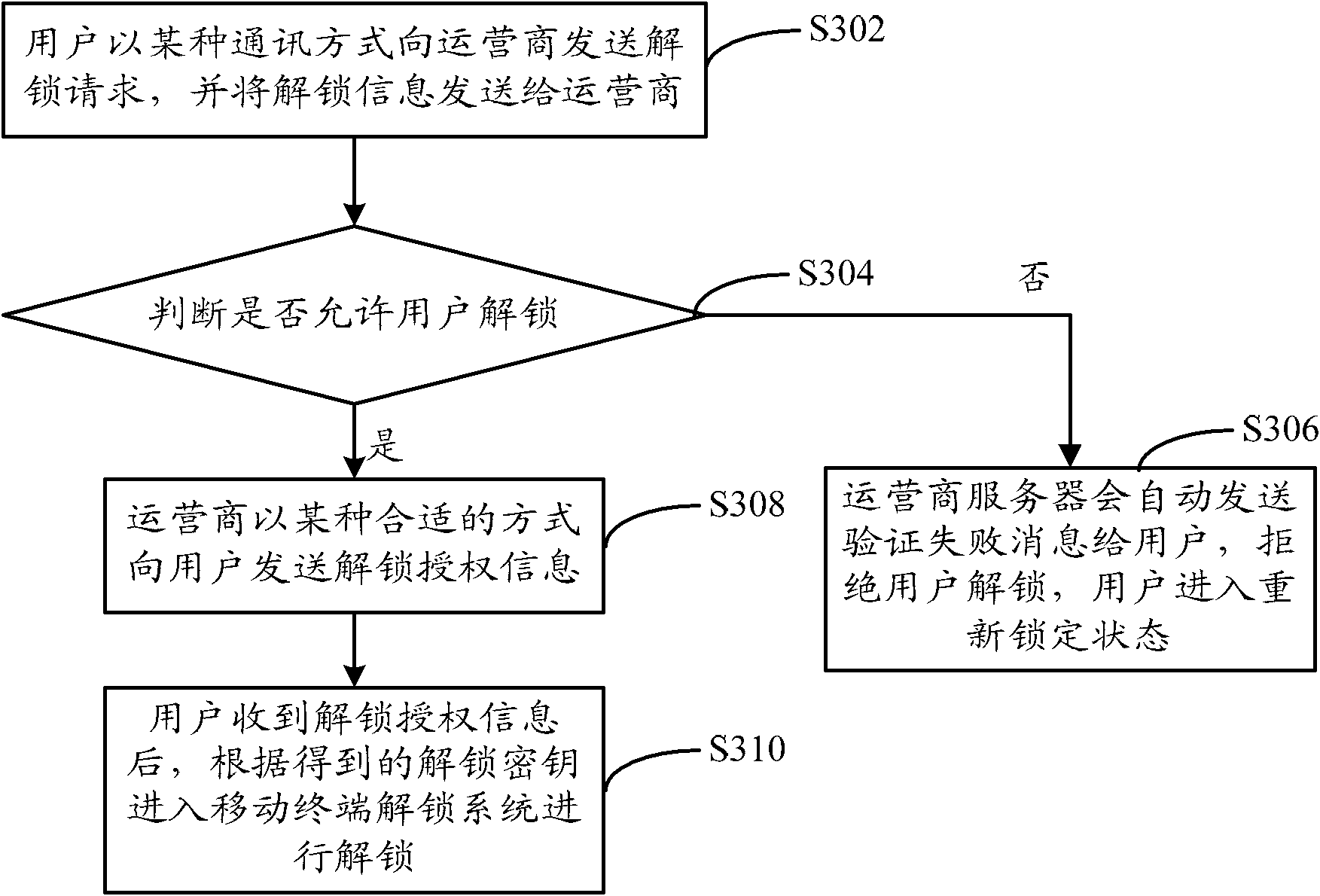
[0042] This embodiment provides a method for an operator to unlock a mobile terminal, see image 3 , the method for an operator to unlock a mobile terminal comprises the following steps:
[0043] Step S302, the user sends an unlocking request to the operator by a certain communication method, and sends the unlocking information to the operator;
[0044] Wherein, the unlocking information is some specific identification information, and these identification information can fulfill the requirement of key query required by a given locking mode. For example, for the card locking method, the unlocking information may include the International Mobile Subscriber Identity (IMEI number) of the user's mobile phone, the network control password, and the unlocking request.
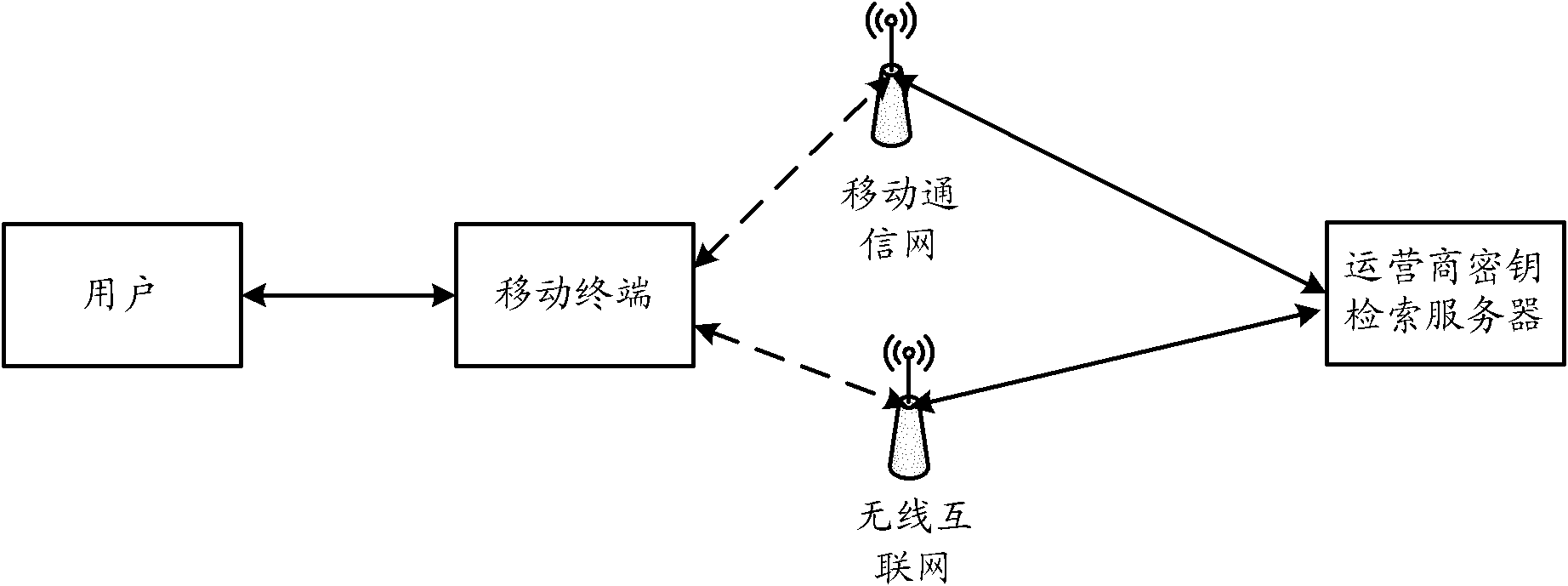
[0045] The communication method between the terminal phone and the operator can be any suitable method, as long as it can meet the unlocking requirements, for example, it can be implemented by sending short messages,...
Embodiment 3
[0063] This embodiment provides an operator equipment, see Figure 5 , the carrier equipment includes:
[0064] The receiving module 52 is configured to receive an unlock request from the mobile terminal, wherein the unlock request carries unlock identification information;
[0065] The operator's equipment receives the unlocking request from the mobile terminal in one of the following ways: SMS, USSD or WAP.
[0066] The retrieval module 54 is connected to the receiving module 52, and is used to determine that the mobile terminal is allowed to unlock according to the unlocking identification information, and query the key list database pre-stored in the operator's equipment according to the unlocking identification information to obtain the unlocking key;
[0067] The sending module 56 is connected with the retrieval module 54, and is used for sending the unlocking key to the mobile terminal, so that the mobile terminal can be unlocked according to the unlocking key.
[006...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com