Software protection method and device and software protection lock
A software protection and software technology, applied in computer security devices, program/content distribution protection, instruments, etc., can solve problems such as waste, waste of resources, and difficulty in modification by software developers, so as to reduce the cost of use and protect the right to use Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040] In order to enable those skilled in the art to better understand the present invention, the embodiments of the present invention will be described in detail below with reference to the accompanying drawings, but this is not intended to limit the present invention.
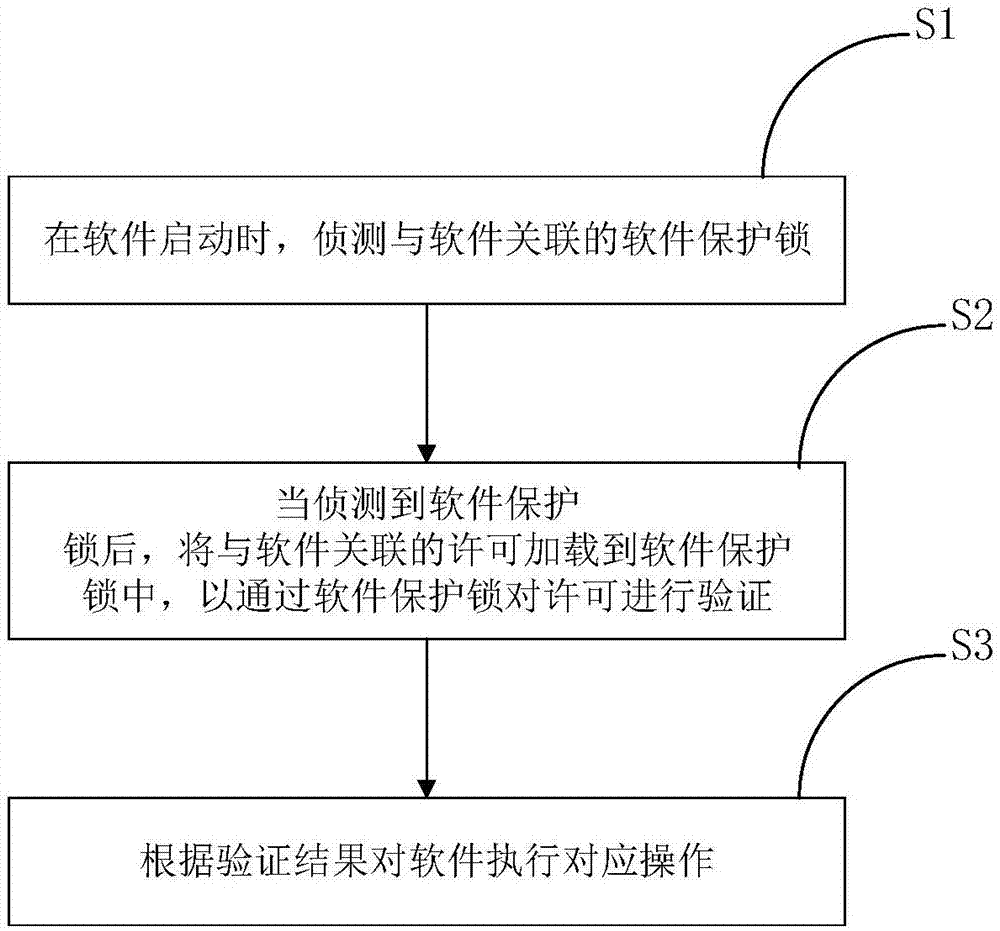
[0041] figure 1 It is a flowchart of a software protection method according to an embodiment of the present invention. A software protection method according to an embodiment of the present invention is used to protect software, such as figure 1 As shown, the software protection method includes the following steps:
[0042] S1, when the software is started, detect the software protection lock associated with the software;
[0043] Software and software protection locks have an associated relationship. For example, after a software manufacturer establishes a cooperative relationship with a software protection lock manufacturer, it can establish an association relationship between the software developed by t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com