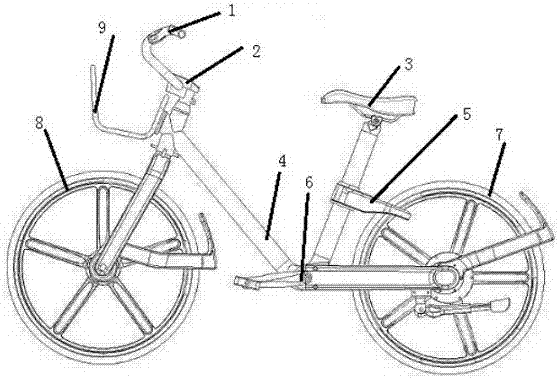
Method for adopting mobile terminal to open bicycle, corresponding bicycle operation platform and bicycle
A mobile terminal and operating platform technology, applied in coin-free or similar appliances, coin-operated equipment with meter control, coin-operated equipment for distributing discrete items, etc. User-friendly approach, QR codes are easily contaminated, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
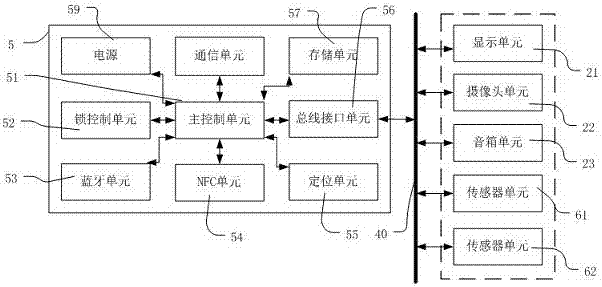
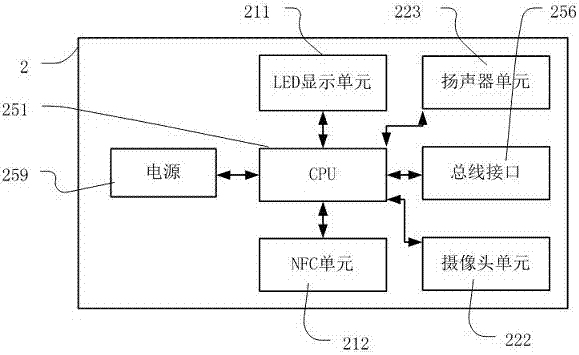
[0038] Embodiment 1 The workflow of using the user ID information stored in the NFC module of the mobile terminal to unlock
[0039] User ID information is the unique identity certificate issued by the bicycle operation platform to registered users. When a user registers on the bicycle operation platform through a mobile terminal, the bicycle operation platform will issue an encrypted user unique identity certificate to the user. The bicycle application on the mobile terminal The program writes the user's unique identity credential data into the data storage unit of the NFC module of the mobile terminal. When the mobile terminal is close to the NFC unit of the bicycle, the NFC unit of the bicycle reads the unique identity credential data of the user, unlocks the bicycle lock after the authentication is passed, and communicates with the bicycle operation platform through the communication unit 58, reports the riding record, and passes the The account of the user's unique identi...
Embodiment 2
[0045] Embodiment 2 The workflow of using the mobile terminal NFC module to store the one-time authentication key sent by the bicycle operation platform
[0046] Before the mobile terminal is out of power, the user obtains a one-time authentication key for NFC card mode authentication from the bicycle operation platform through the bicycle application program of the mobile terminal, and stores the key in the NFC unit of the mobile terminal. When the unit is read by the NFC unit of the bicycle, the NFC unit of the mobile terminal sends the one-time authentication key to the NFC unit of the bicycle, and the bicycle authenticates the validity of the key. The vehicle information is sent to the bicycle operation platform, and if it is illegal, it will call the police and remind the user.
[0047] Similarly, after the user obtains the one-time secret key, it is stored in the memory of the NFC unit of the bicycle for the convenience of using after power failure. If someone scans the ...
Embodiment 3
[0049] Embodiment 3 The workflow of using the unified ID number of the NFC module of the mobile terminal to unlock
[0050] Both the user ID information and the one-time authentication key mentioned above need to be obtained by the host of the mobile terminal device and written into the storage unit of the NFC module of the mobile terminal. At the same time, since the NFC module has a unified ID number, the ID number is also unique. It can also be used for user identification by binding the ID number with the user identity on the bicycle operation platform, that is, as long as the bicycle NFC module receives the ID The ID number is considered as the user bound to it, and the use of the bicycle with the ID number is equivalent to the use of the bicycle by the user. The binding process is very simple. The user logs in to the bicycle application on the mobile terminal and starts the NFC registration process. The bicycle application reads the ID number and sends it to the bicycle ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com