Network safety evaluation method based on attack-defense utility
A network security evaluation and utility technology, applied in the direction of data exchange network, digital transmission system, electrical components, etc., can solve the problems of lack of evaluation index system, accurate measurement index value, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0080] The present invention will be further elaborated below in conjunction with the accompanying drawings and specific embodiments.
[0081] At first the technical terms used in the present invention are explained:
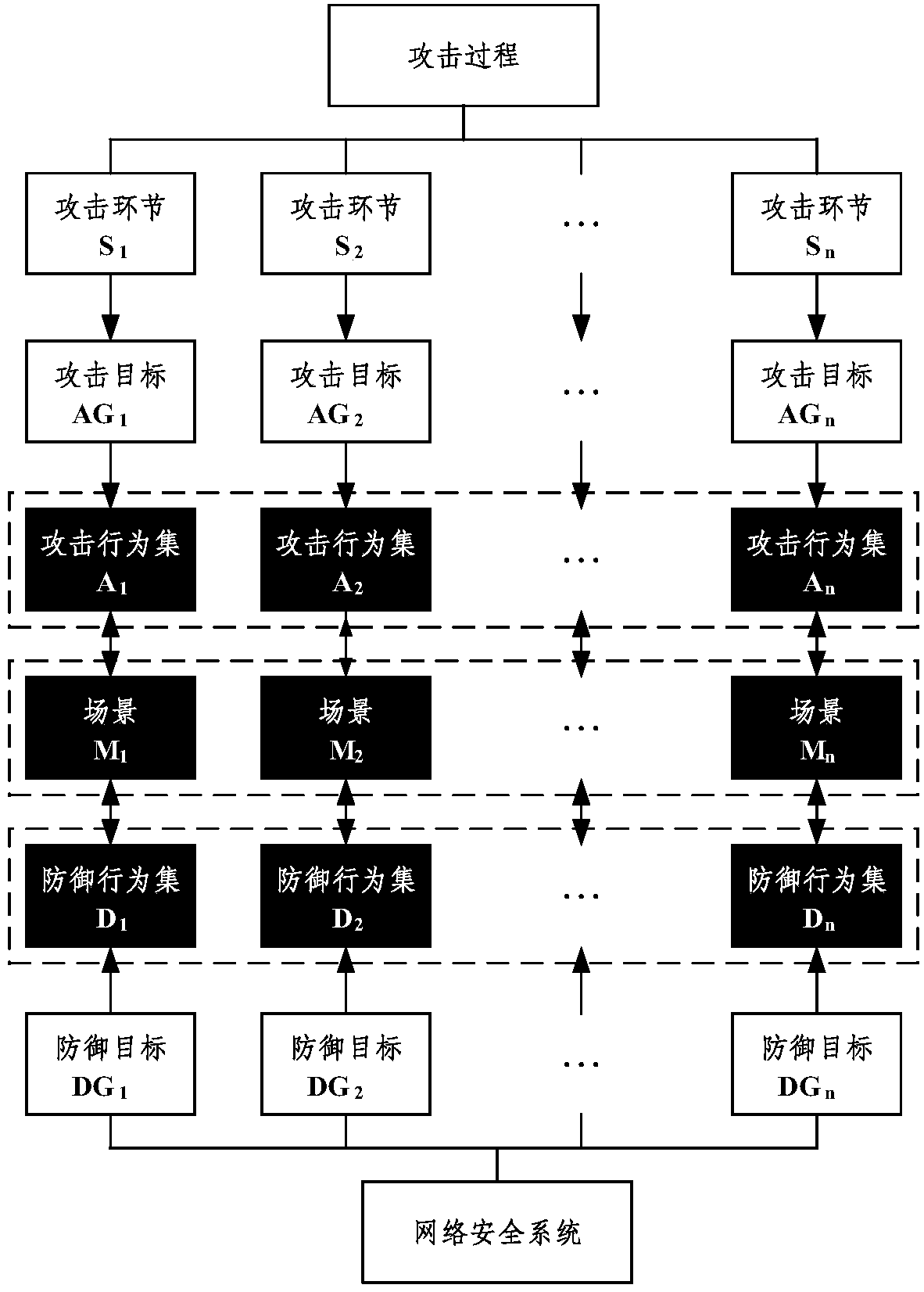
[0082] Network system: If the various objects of the network are set to a non-empty set A, and A satisfies
[0083] (1) A contains at least two different elements;
[0084] (2) The elements in A are related to each other in a certain way;
[0085] Then A is called a network system, and the elements of A are the components of the network system.
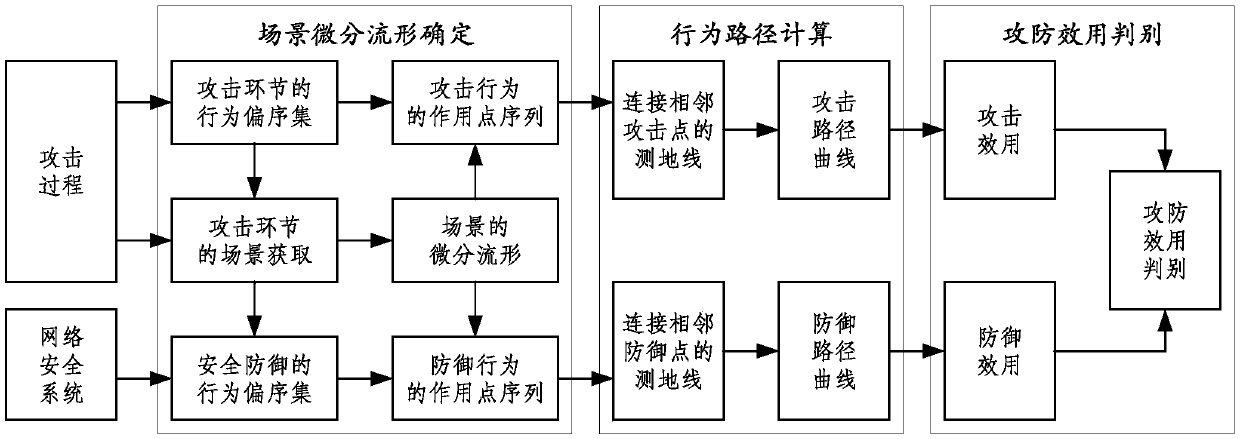
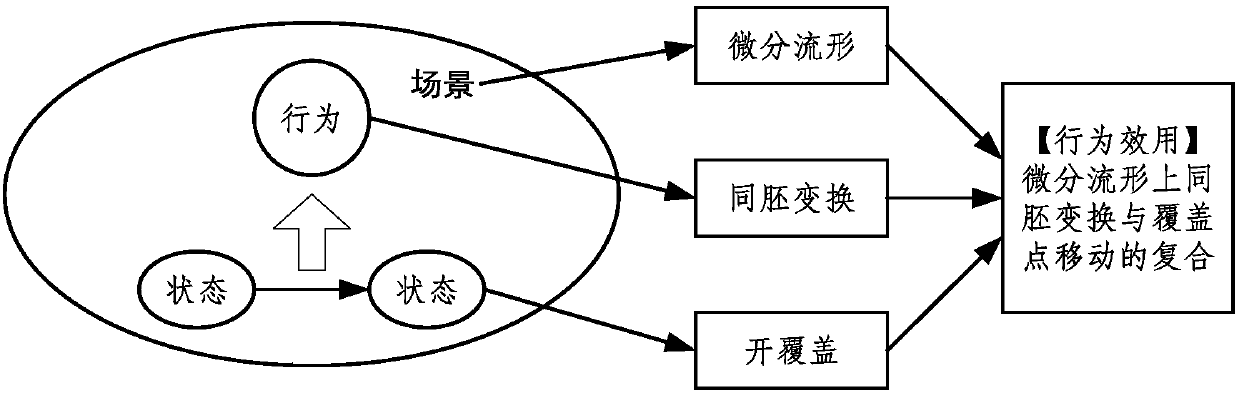
[0086] Behavior: Behavior refers to the homeomorphic transformation from one cover to another cover on the scene differential manifold;
[0087] Behavior path: Behavior path refers to a directed curve that connects the start and end points of behavior transformation and is smooth segment by segment.
[0088] Behavior paths have the following properties.
[0089] 1. Parallel movement of points The movement of any po...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com