Verification method for dynamic shielded character string graphical verification code
A graphic verification code and verification method technology, applied in the field of computer software, can solve problems such as increasing the verification code recognition difficulty, and achieve the effect of preventing malicious screen capture and improving security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
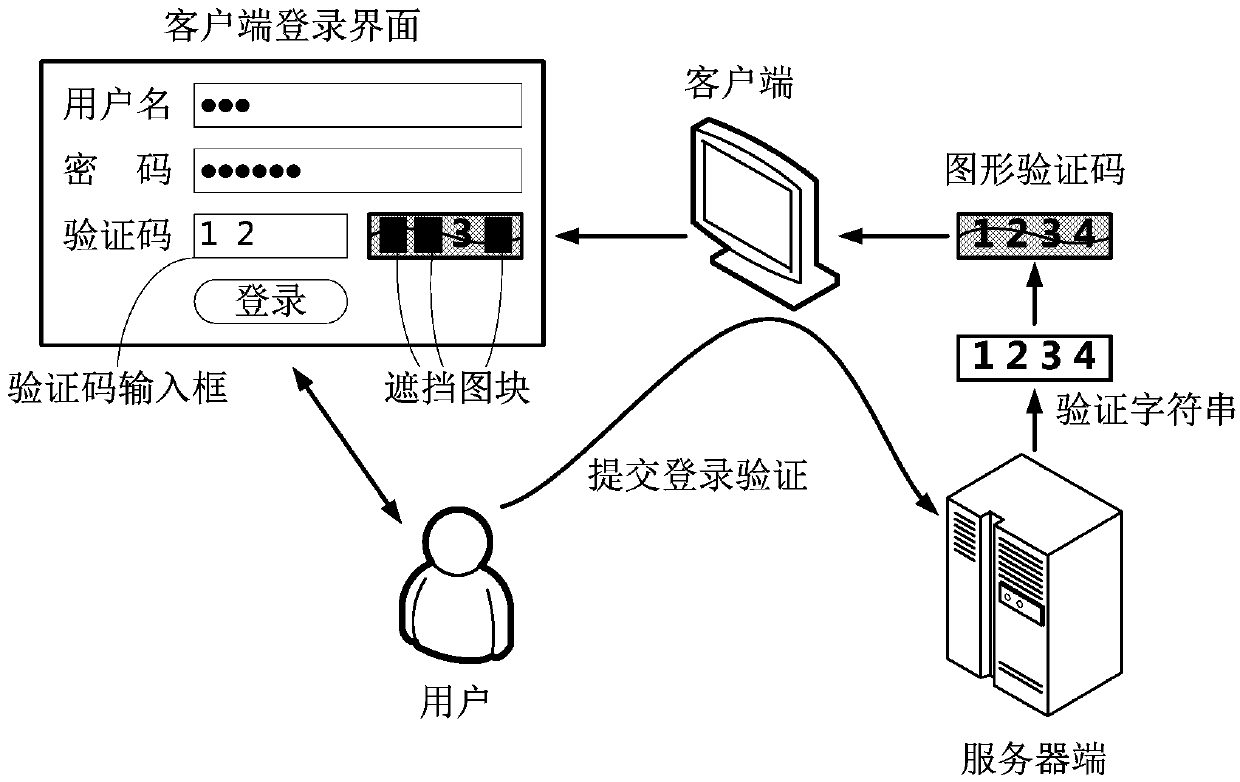
[0018] Captcha contains more than one character. Such as figure 1 As shown in , after the client sends an access request to the server, the server will send a verification string consisting of four random characters (here as figure 1 As shown, for example, the verification strings sequenced as 1, 2, 3, 4) are embedded into pictures with interferences such as random curves and / or random noise to form a graphic verification code and send it to the client. When the graphical verification code is displayed on the client login interface, at least one character in the verification string of the graphical verification code is blocked by a block (here as figure 1 As shown, for example, the four characters 1, 2, 3, 4 in the verification string are all blocked by the occlusion block);
[0019] On the client login interface, the user sequentially recognizes and inputs each character in the verification string of the graphic verification code into the verification code input box accordi...
Embodiment 2
[0022] The graphic verification code contains more than one character, and the character of the verification string is input by the voice input method at the same time. When the client receives the graphical verification code and displays it on the client login interface, at least one character in the verification string of the graphical verification code is blocked by the occlusion block, and the first character is not blocked (here as figure 1 As shown, for example, the three characters 2, 3, 4, etc. in the verification string are all covered by the occlusion block, while the character 1 is not covered); when the client captures the voice of the user reading the first character After that, it can be judged that the user has started voice input of the verification code information and completed the recognition of the first character, and then removed the occlusion blocks that block characters 2, 3, and 4 in order to perform recognition and voice input; finally, the user The c...
Embodiment 3
[0024] There is only one character in the graphic captcha. The unique character in the verification string is blocked by the blocking block; when the client login interface judges that the cursor is located in the verification code input box, immediately remove the blocking block blocking the unique character, and the unique character is displayed. It recognizes and inputs it into the verification code input box, and then submits it to the server for login verification; if the login verification is not submitted immediately, the blocked block removed within 5 seconds will return to its original position and cover the unique character.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com