Web attack identification method and device
A technology of attack identification and identification, which is applied in the field of computer network to achieve the effect of improving efficiency and shortening time-consuming
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
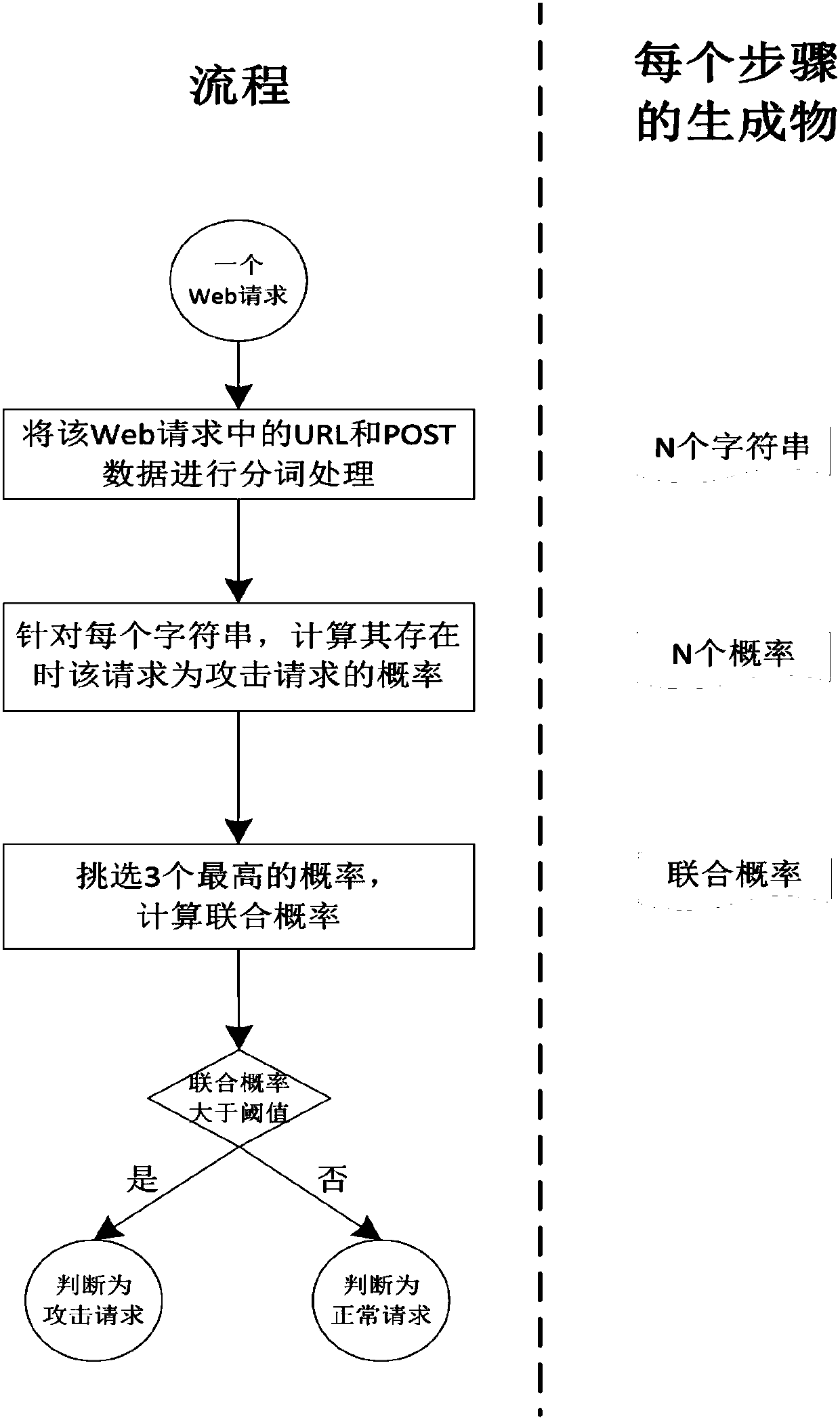
[0047] In order to make the above-mentioned features and advantages of the present invention more comprehensible, the following specific embodiments are described in detail in conjunction with the accompanying drawings.
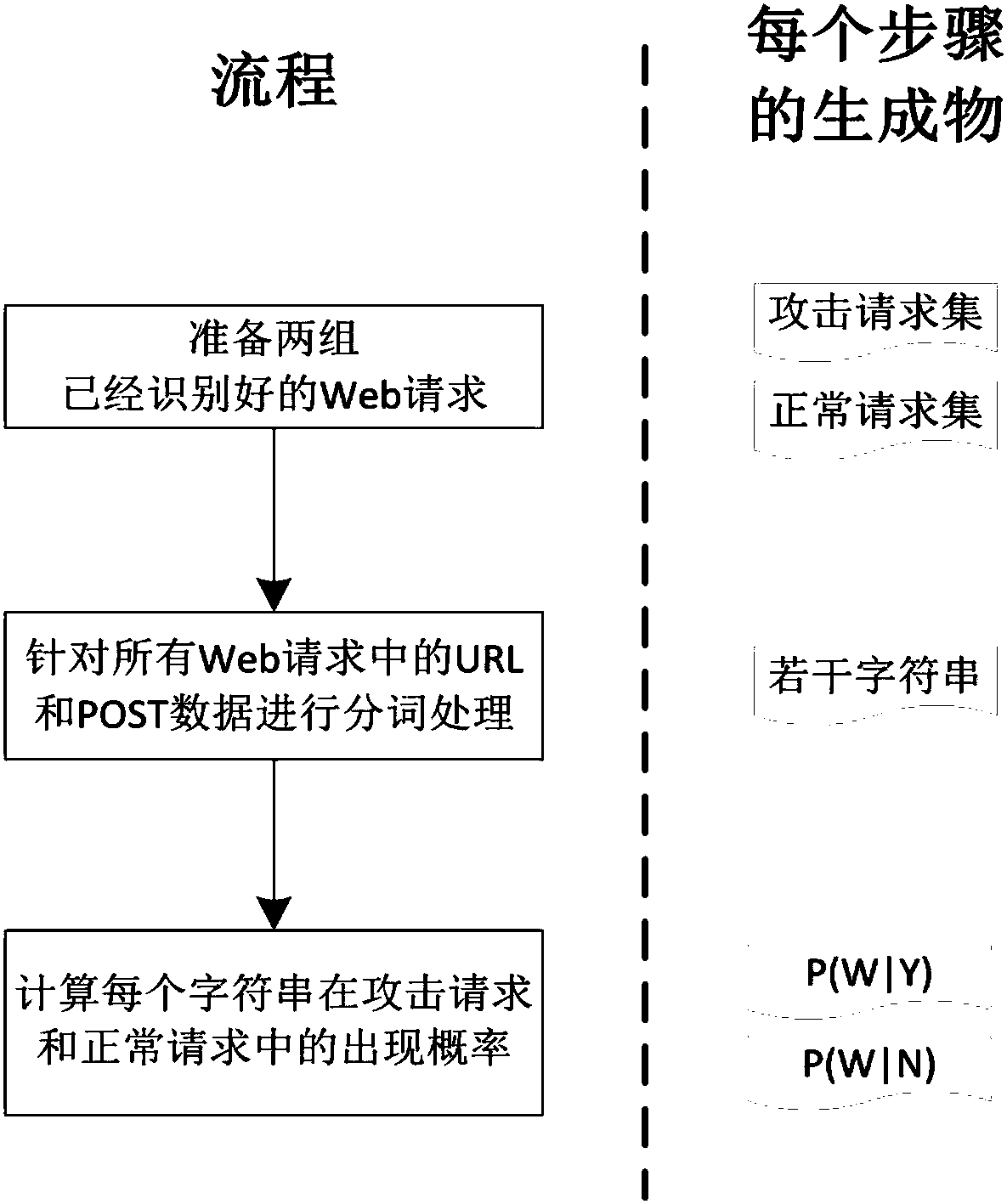
[0048] (1) Preliminary Statistics
[0049] (1) Prepare two sets of identified web requests
[0050] Prepared request sets, attack requests and normal requests are not less than 10,000.
[0051] (2) Word segmentation processing for URL and POST data in all web requests
[0052] The URL includes six elements: request protocol scheme, target address netloc, webpage path path, parameter params required by webpage path, query parameter query, and fragment identifier fragment.
[0053] scheme: / / netloc / path;params? query#fragment.
[0054] Example: http: / / admin:pass@www.test.com:80 / bbs / index.php;params? id=10#top.
[0055] in
[0056] scheme='http',
[0057] netloc='admin:pass@www.test.com:80',
[0058] path=' / bbs / index.php',
[0059] params='params',
[00...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com