Three-layer message flow guidance method and controller
A controller and message technology, applied in the communication field, can solve problems such as the failure of the safety protection function of the safety equipment and the attack on the customer network
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
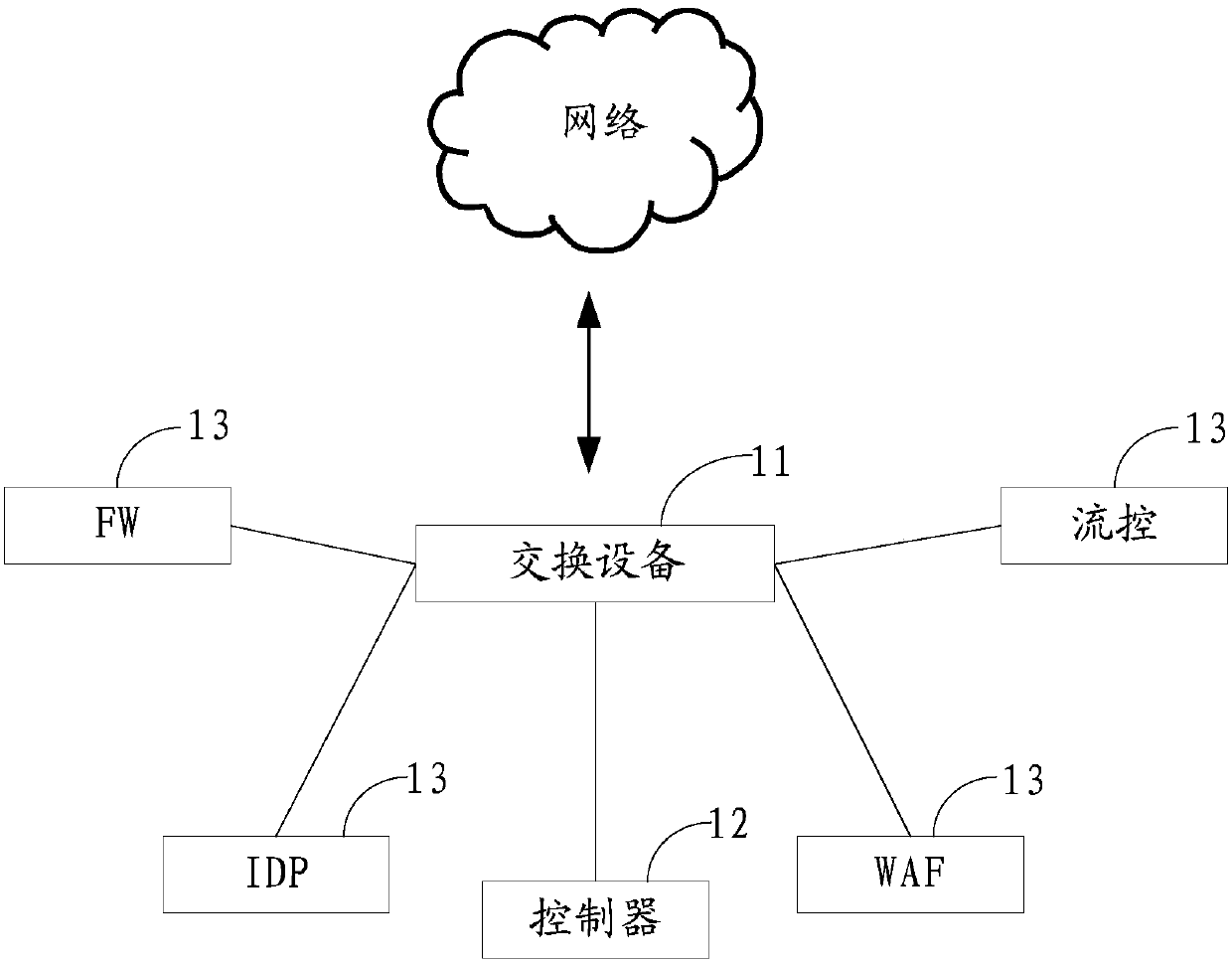
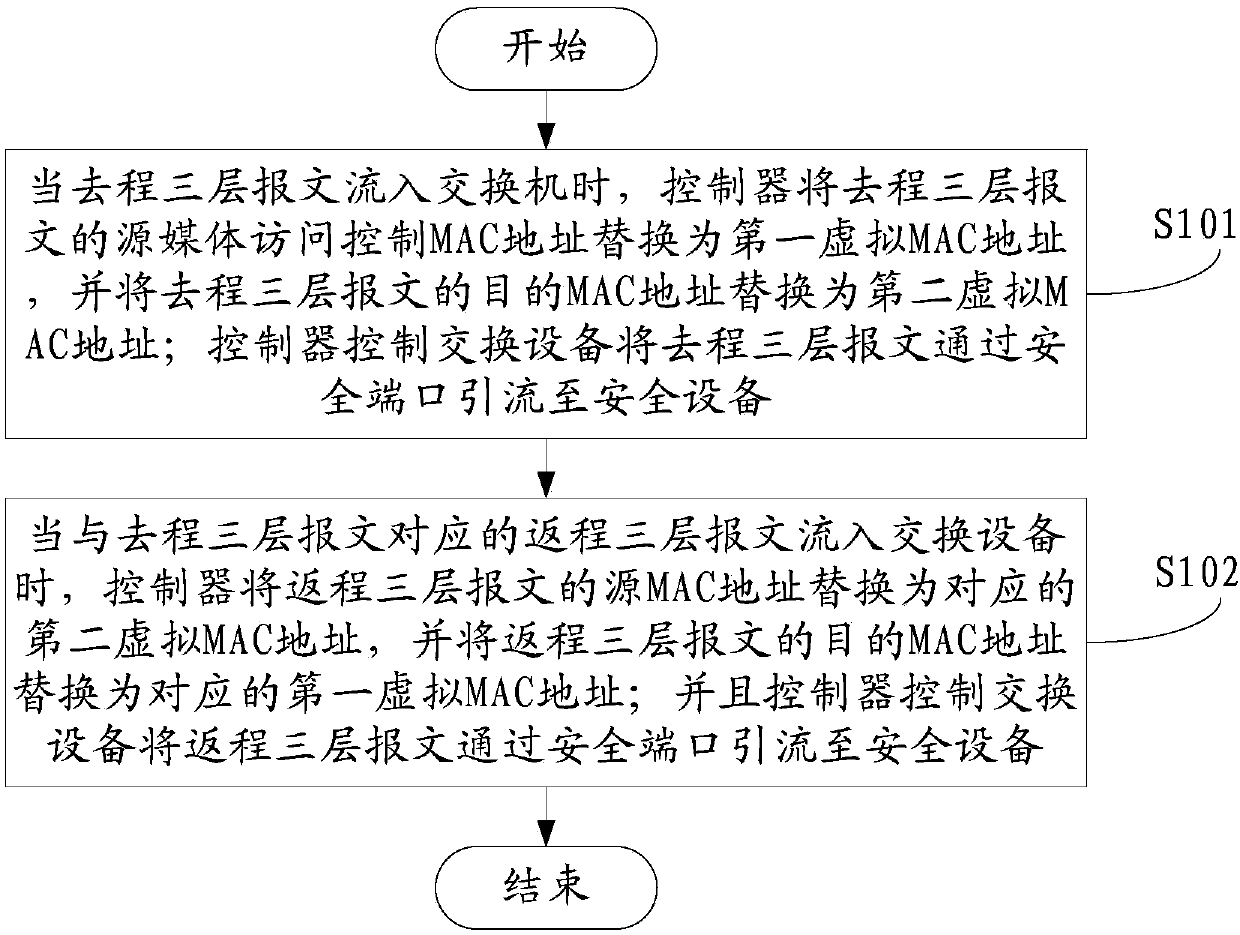
[0032] refer to figure 2 As shown in , the embodiment of this application provides a three-layer packet diversion method, which is applied to the above network architecture, and the method includes:
[0033] S101. When the outbound Layer 3 message flows into the switching device, the controller replaces the source MAC address of the outbound Layer 3 message with the first virtual MAC address, and replaces the destination MAC address of the outbound Layer 3 message Replace it with the second virtual MAC address; and the controller controls the switching device to divert the outbound Layer 3 packets to the security device through the security port.
[0034] The outbound packets are in one-to-one correspondence with the first virtual MAC address and the second virtual MAC address.
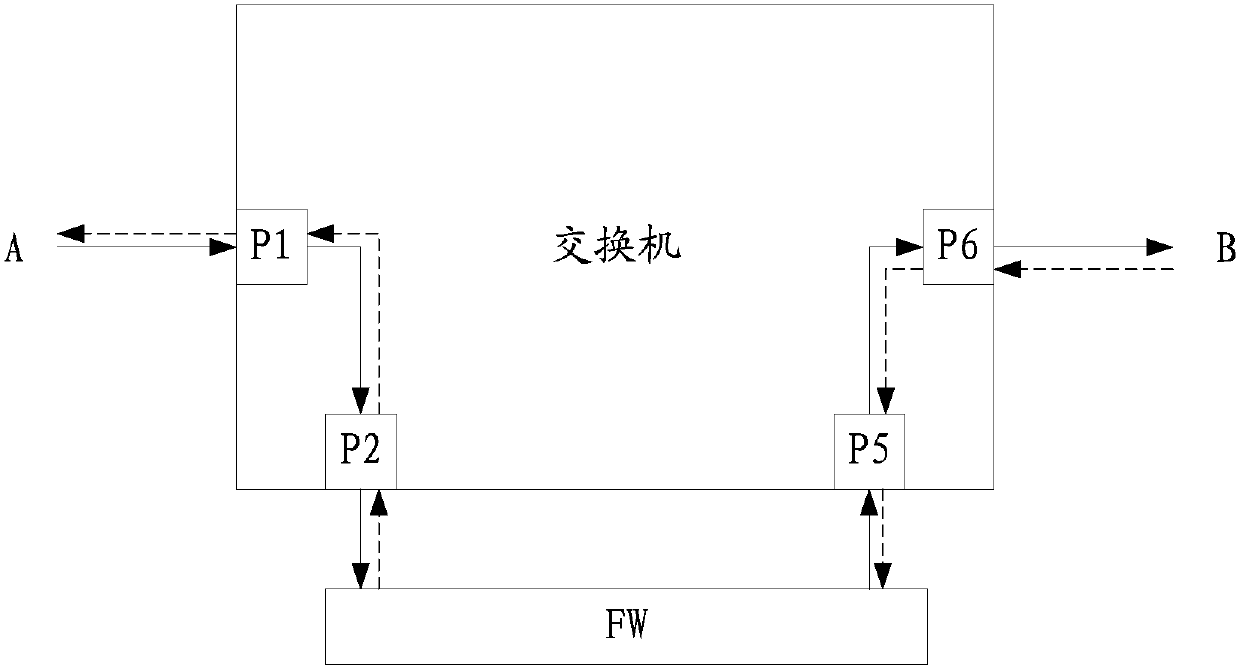
[0035] Take a security device as an example of a service chain, refer to image 3 As shown in , it is assumed that the security device includes a FW, and the switching device is a switch. The serv...
Embodiment 2
[0060] The embodiment of this application provides a controller, which is applied to the above-mentioned network architecture, referring to Figure 6 As shown in, the controller 60 includes:
[0061] The replacement unit 601 is configured to replace the source media access control MAC address of the outbound Layer 3 message with the first virtual MAC address by the controller when the outbound Layer 3 message flows into the switching device, and replace the outbound Layer 3 message The destination MAC address of the destination MAC address is replaced with the second virtual MAC address, and the outbound packet corresponds to the first virtual MAC address and the second virtual MAC address one by one.
[0062] The traffic diversion unit 602 is configured to control the switching device to divert outbound Layer 3 packets to the security device through the security port.
[0063] The replacement unit 601 is also configured to replace the source MAC address of the return layer 3...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com