A Trajectory Privacy Preservation Method Based on Caching and Position Prediction Mechanism
A prediction mechanism and privacy protection technology, applied in transmission systems, electrical components, etc., to reduce risks, improve trajectory privacy, and reduce query overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0047] The present invention will be further described below in conjunction with the drawings and embodiments.
[0048] In this example, the user is used to represent the requesting client and neighboring clients.
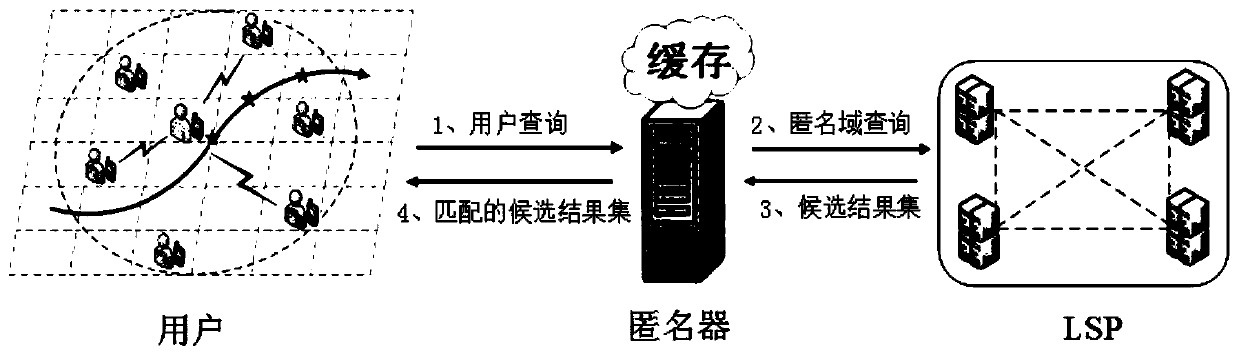
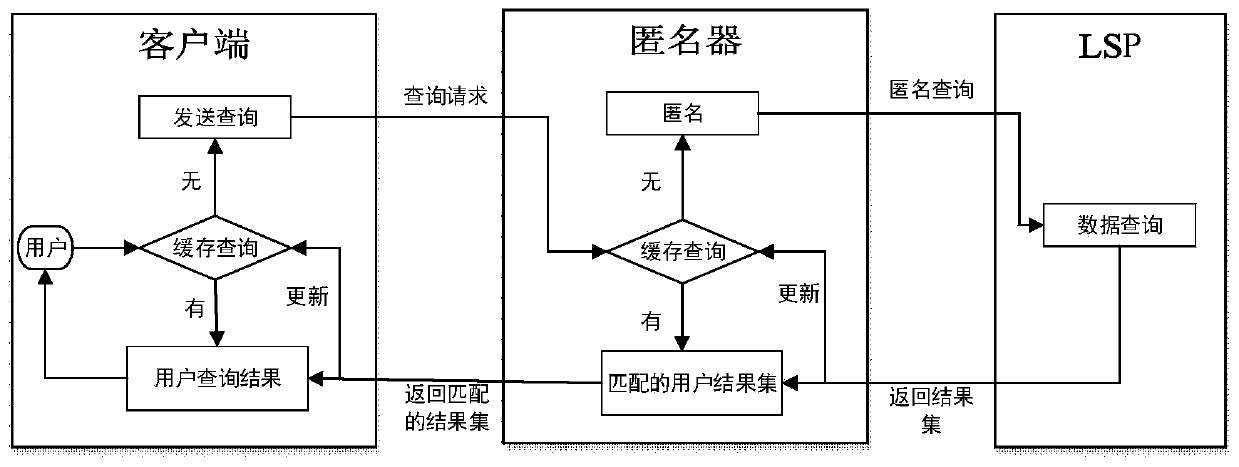
[0049] Such as figure 1 with figure 2 As shown, a trajectory privacy protection method based on cache and location prediction mechanism mainly includes client-side cache lookup and query request, anonymizer cache lookup and location anonymization, LSP data query, anonymizer update and matching user result set, request client The five processes of end update and refinement results are as follows:
[0050] Step 1: Client cache lookup and query request
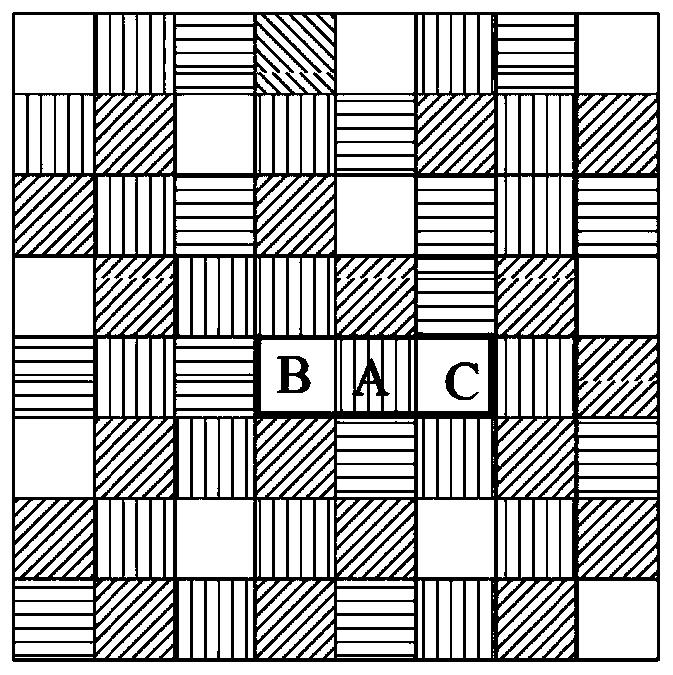
[0051] The system specifies a query range before the user query. The range can be determined by the coordinates of the lower left corner (x 1 ,y 1 ) And the upper right corner coordinates (x 2 ,y 2 ) Is determined, and it is divided into m×m grids of equal size. Therefore, the grid structure of the query range specified by...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com