Binary program-oriented heap overflow detection method
A binary program and detection method technology, applied in the field of network security, can solve problems such as unsatisfactory efficiency, achieve the effect of preventing missed reports, reducing potential harm, and ensuring operating efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] The technical scheme of the present invention will be described in detail below in conjunction with the drawings:
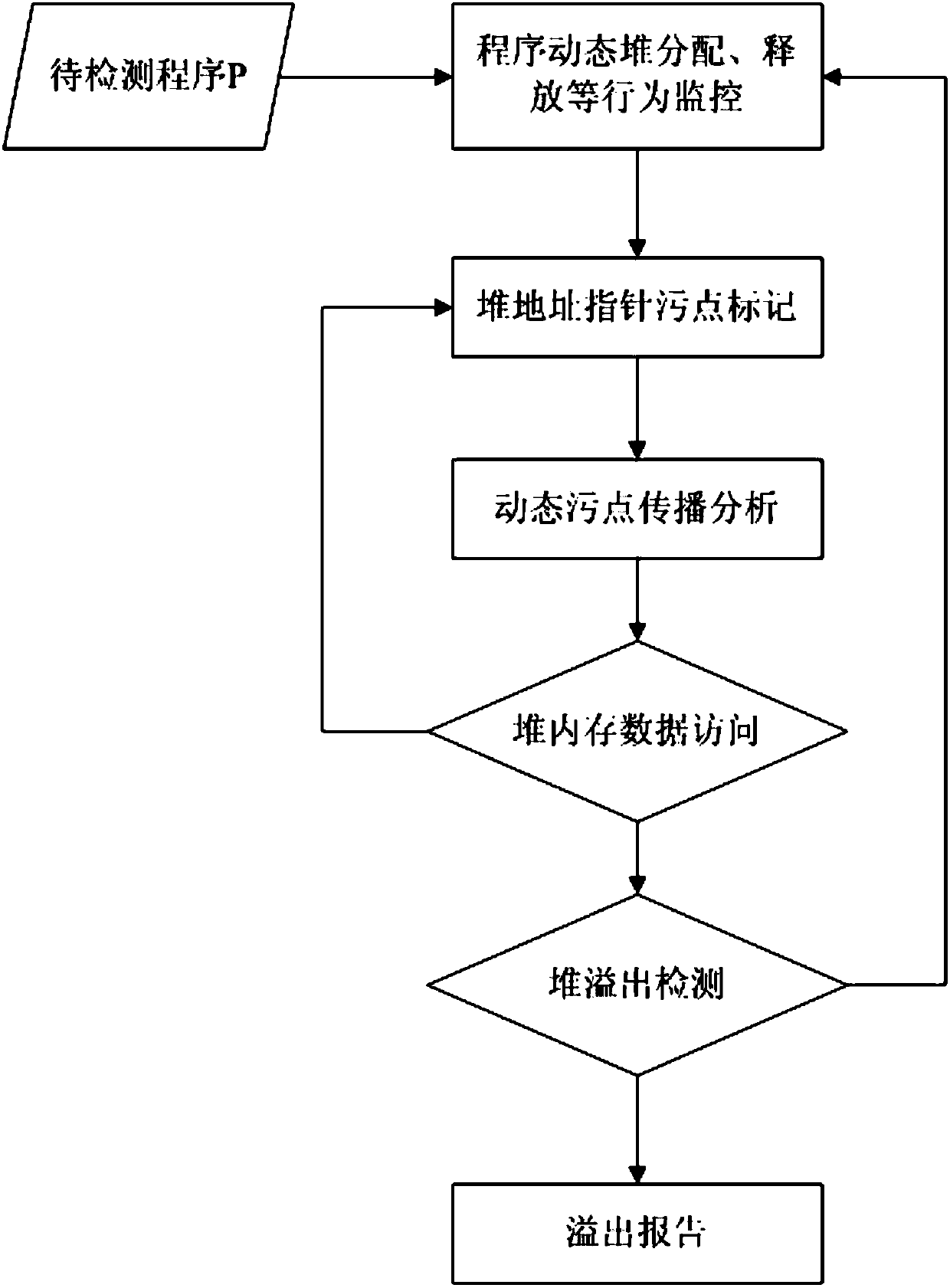
[0032] Such as figure 1 As shown, in one embodiment, a binary program-oriented heap overflow detection method is provided, which includes the following steps:
[0033] 1. Monitor program dynamic heap allocation, release and other behaviors;
[0034] Real-time record according to the call situation of heap management operation functions such as heap allocation, release, and reallocation during the running of the program, and related heap allocation (including reallocation), released size, heap starting address and other heap management operation information Make a record.
[0035] First of all, through program dynamic monitoring technology, obtain heap allocation (including reallocation), release and other behaviors, and on the basis of heap operation behavior records.
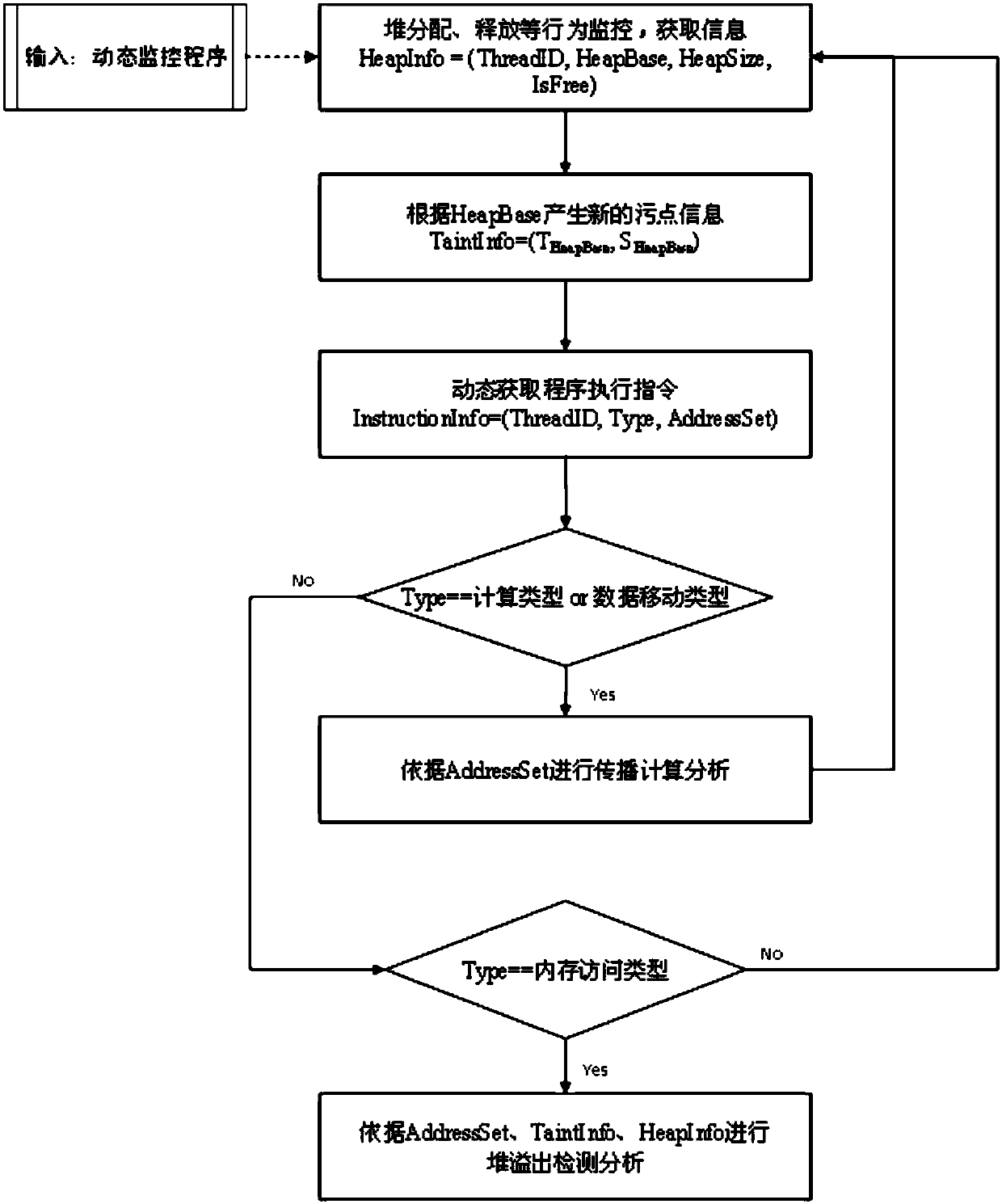
[0036] Specifically, the present invention uses heap information HeapInfo=(ThreadID, HeapBase, H...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com