System and method for security check of both passengers and personal belongings security check based on THz imaging technology
A technology of terahertz imaging and terahertz, which is applied in the field of security inspection system for simultaneous inspection of people, can solve problems such as lack, and achieve the effect of improving the effect of security inspection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
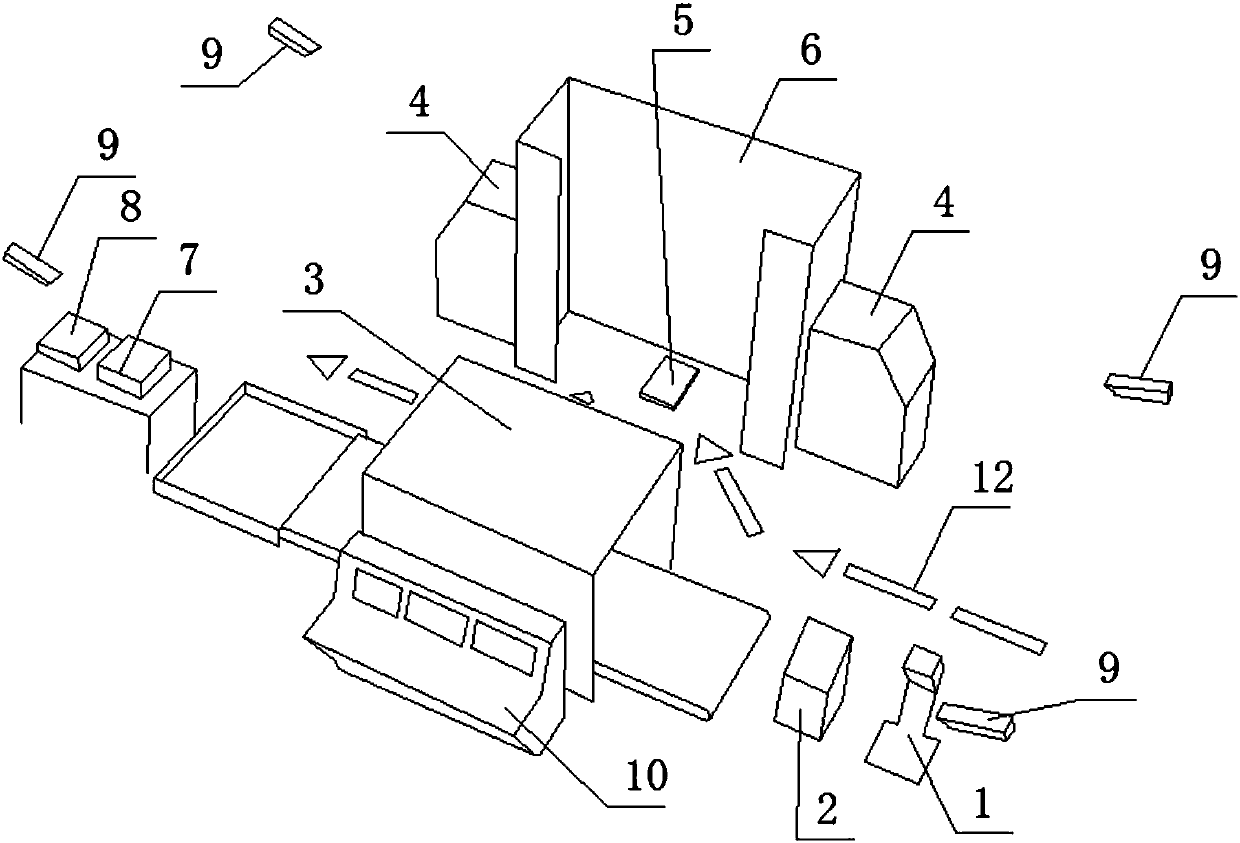
[0032] Such as figure 1 As shown in the figure, a security inspection system based on terahertz imaging technology, in which the central control and operation console 10 and the monitoring software 11 are used for the operation of the security inspection system, the control of other security inspection equipment in the security inspection system, and the display And store the detection results of other security inspection equipment, and have the function of viewing the security inspection data at any time before.
[0033] The central control and operation console 10 controls the mobile phone code detection device 1, displays and stores the mobile phone number and owner information of the detected person detected by the mobile phone code detection device 1, and can check the detection results at any time.
[0034] The central control and operation console 10 controls the witness comparison device 2, displays and stores the comparison results of the inspected person and the ID c...
Embodiment 2
[0047] A security inspection method based on a terahertz imaging technology-based security inspection system for simultaneous inspection of people. The security inspection system has a one-key start-up function. After the system is powered on, turn on the switch located on the central control and operation console 10, and all security inspection equipment is activated and started. Self-inspection, after the self-inspection is passed, the monitoring software 11 prompts that the system startup is complete, and the detected personnel can be detected. During the start-up process, there is no need to operate each security inspection device separately.
[0048] The inspected personnel follow the guide line 12 of the security inspection process and complete the security inspection process through the following steps:
[0049] Step 1: The detected person uses the mobile phone code detection device 1, which detects the mobile phone number and the owner of the mobile phone number of the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com