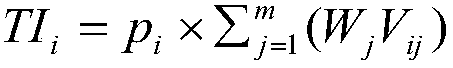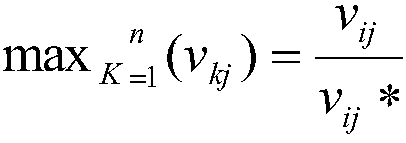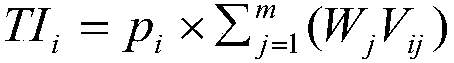Power system mobile terminal security threat assessment method
A mobile terminal and power system technology, applied in the field of power system, can solve the problems of waste of input cost, lack of unified R&D safety quality control and operation safety protection considerations, threats to the information network and business operation of power companies, etc., to ensure safety. effect used
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] A method for assessing the security threat of a power system mobile terminal in this embodiment specifically includes the following steps:
[0023] S1: Analyze the security threats faced by power terminals and generate a threat list T:{t i |i=1,2,3...,n}, where, t i is the threat in i, and n is the total number of threats faced by the system;
[0024] S2: According to the generated threat list, establish a power terminal threat set:
[0025] First determine the threat consequence attributes, including such as "inability to perform key operations", "loss of productivity", "loss of income", "damage to public reputation", "endangerment of public safety", etc. Then denote the threat consequence attribute type as X:{x j |j=1,2,3...,m}, where x j is the jth consequence attribute, m is the number of types of consequence attributes;
[0026] S3: Determine the threat consequence attribute, and determine the weight W corresponding to the threat consequence attribute:{W j |j...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com